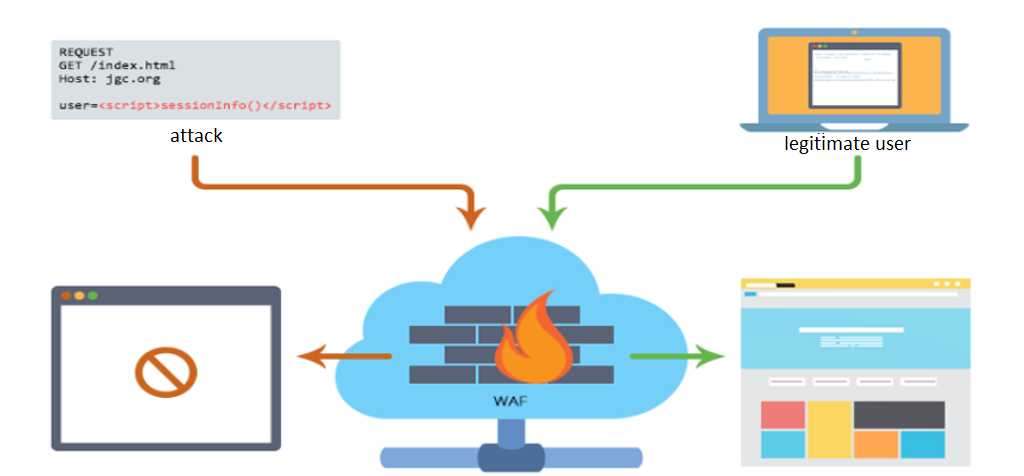
Information security risks are increasing with possible hacking threats. What should be done in this case to protect valuable information within web application? Countermeasures can be applied at two applications stages.
- During development stage, by using the latest versions of scripts and CMS, testing application security, conducting various analyses.
- At the operational stage, it is better to implement attack prevention systems: Next Generation Firewall (NGFW) and Web Application Firewall (WAF).
Using WAF is an effective method of applications protection that does not require further development of application itself.
Web Application Firewall is a firewall for application protection used to detect and block attacks on web applications, it allows to identify and prevent such types of vulnerabilities:
SQL Injection
Cross Site Request Forgery (CSRF)
Remote File Inclusion (RFI)
Cross Site Scripting (XSS)
Insecure Direct Object Reference
Local File Inclusion (LFI)
Auth Bypass
Remote Code Execution (RCE)
Bruteforce
General requirements which the hacking prevention system must comply:
- PCI DSS requirements must be met;
- OWASP Top Ten list threats prevention;
- requests and responses validation for compliance with security policy, event recording; data leakage prevention;
- tracking web pages content including DHTML, HTML, CSS, and protocols (HTTP/HTTPS);
- web service notifications tracking;
- protection from threats aimed directly at WAF;
- data flow tracking;
- SSL\TLS usage;
- session ID forgery detection and blocking;
- automatic tracking of new attack signatures;
- fail-open and fail-close mode availability;
- clients' SSL certificates support;
- hardware key storage ability (FIPS).