Maintaining database security is of utmost importance in our modern digital age. It protects our data from unauthorized access. For example, we can consider how they might be threatened by hackers who might try to infiltrate a database to gain access to users’ personal data or company funds.
In addition, database security helps protect our information from unexpected system failures that can result from storing large amounts of data. If the database is not provided with the proper level of protection, all this data may be lost.
The main threats faced by databases include:
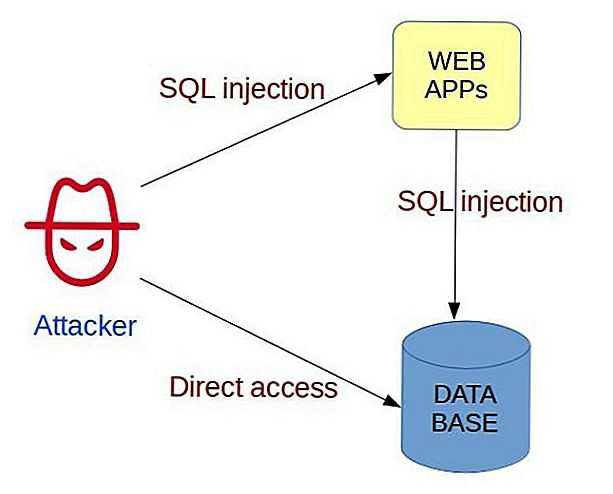
SQL injection is a type of attack in which an attacker uses bugs in a website or application to gain access to a database. As a rule, this happens by injecting malicious SQL code into forms, input fields, or through other services. An attacker can enter SQL commands instead of entering standard parameters. This allows him to access important information or change the contents of the database. Example: An attacker can add a DELETE command to remove data from a database.
Password cracking is an attack in which an attacker attempts to guess a password or use weak passwords to gain access to a database. Password cracking can be automated using brute-force programs, which allows an attacker to quickly find the correct password and gain access to valuable information.
Unauthorized data access is when an attacker gains access to a database without the permission of the owner or database administrator. This can happen through the use of weak passwords or security vulnerabilities. As a result, an attacker can gain access to confidential information and use it for their own selfish purposes.
There are a lot of problems in history related to database security. One of the most famous is the Equifax database attack in 2017, when attackers stole the personal information of more than 143 million people. This attack was due to unimaginably weak passwords and vulnerabilities in the security system itself.
Database authentication methods
Password hashing is one of the popular authentication methods. Instead of storing the password in clear text in the database, the password is hashed using a special hashing algorithm and stored as a hash value. A hash is a complex algorithm that is used to create a unique and encoded value for each password.
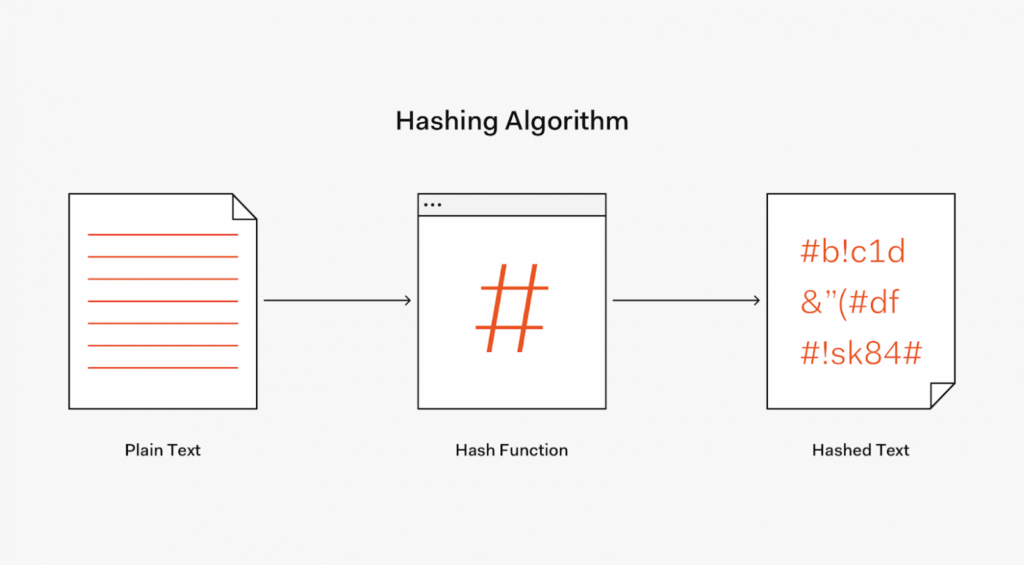
The best way to verify that the password was entered into the system correctly is to compare the hash value that was generated when the password was entered with the hash value that was stored in the database. If the two values match, the user is granted access to the database. If not, then access to the database is not available.
However, not all hashing algorithms are secure.
Using SSL/TLS encryption. During data transmission over the network, the data can be intercepted by intruders who can gain access to it, but when using SSL / TLS data encryption, this becomes almost impossible. SSL/TLS encryption uses special certificates and protocols to encrypt data and protect it from unauthorized access.
Let’s take a look at how SSL/TLS encryption works using a simple request to a website, for example to get a page on the Internet.
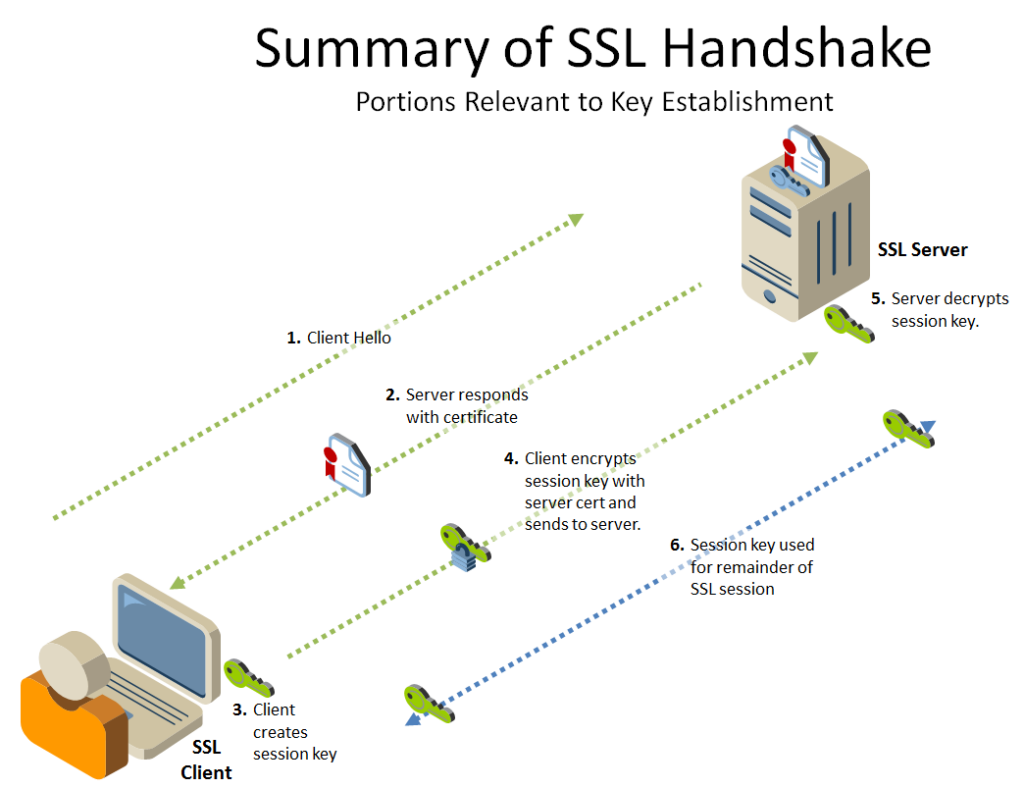
1. When you enter a website’s URL into the browser’s address bar, the browser establishes a connection to the server hosting the website.
2. When the server receives a connection request from the browser, it sends its digital certificate to the client side. This certificate contains the public key that the browser uses to establish a secure connection.
3. The browser checks the digital certificate to make sure that the site it is about to connect to is valid and not fake. It does this by verifying the chain of certificates—public keys, root CA certificates, and other intermediate certificates.
4. If the certificate is valid, the browser generates a session encryption key, which is used to encrypt data sent between the client and server.
5. When the client and server communicate with each other, all data transmitted between them is encrypted using this session key. This means that even if someone intercepts this data, he will not be able to read or use it.
6. At the end of the session, the browser and server exchange messages to close the secure connection. The session encryption key is destroyed and can no longer be used.
SSL/TLS encryption ensures the security of data transmitted over the Internet and protects against cyber attacks and hackers. This is an important data protection technique used by most web services and applications. Developers and DBAs should ensure that SSL/TLS encryption is used for all data transfers between client and server for maximum security and data protection.
Using OAuth and OpenID to authorize through any OAuth provider such as Facebook, Twitter, Google is one of the most common forms of authentication. It allows third parties to access resources without having to share the user’s password. When using this form of authentication, users can grant access to their accounts without revealing their username and password. Instead, the service uses an access token to authenticate the user.
For example, you can enter the site using your Google account without entering your password and login on the new site. This is possible thanks to the OAuth and OpenID protocols , which allow services to request permission to access your account on other sites without revealing your password or login.
OAuth is an authentication protocol that allows users to grant access to their accounts on other sites to control their authorization and access. An example would be social networking applications that can process user data, request their profile, update statuses, etc. without having to provide your username and password on each of these platforms.
OpenID is a similar authentication protocol but with a wider range of applications. It allows users to use one account to access multiple sites. Thus, a user can use their OpenID to access services without giving them their password and login.
The benefits of using the OAuth and OpenID protocols for authentication are clear. These methods protect user data and provide ease of use because users can use existing user data to access new sites. In addition, they get rid of the need to remember many logins and passwords for each service.
Authorization methods in databases
Nowadays, even with the most advanced information security systems, it is still possible for the user to gain unauthorized access to the database, which can lead to a breach of data confidentiality and many other problems.
Database level permissions
This authorization method controls access to the database through a permissions system at the database level. The programmer or database administrator can control the levels of access to the database so that users can only access certain parts of the database.
Consider a company that works with the data of its customers. The database stores data such as name, address, phone number, etc. By using database level permissions, a company can allow multiple users to access a particular part of the database. For example, the analytics department may only be granted access to each customer’s purchase data, while the sales force may be given access to the customer’s contact information.
Access rights at the database level allow you to restrict access to specific tables or parts of tables, as well as determine the rights to read, write and edit data in a particular table. This way, users will only be able to access the data they need, rather than the entire database.
Separation of access rights at the application level
The second authorization method is application level separation of permissions, where permissions are managed from the application rather than directly from the database. This method is sometimes referred to as the role-based access method. users must be assigned a specific role in order to access the application and its functionality.
A news paper application can use application-level segregation to control user access to certain parts of the site. For example, an administrator can get additional options for editing or deleting products, and a reader can leave a comment.
This authorization method controls access to the application, not the database. This means that users can access the application, but they will not be able to access the data in the database unless they have the appropriate rights. In addition, this method allows more control over the management of user access rights, since the access rights can be changed according to the values stored in the database.
Audit methods in databases
This is an important part of the information security system, which allows you to assess the level of confidentiality and security of data stored in the database.
Logging all actions in the database
Activity logging is the process of recording all database-related events in a system log (log). It may include information about running database queries, data changes, user session time, and other events.
Consider a company that stores sensitive customer data in a database. Logging all actions in the database allows you to keep track of all data changes, understand who accessed this data and when, and also track any unauthorized actions in the database, such as hacking attempts or changes.
Logging all activities helps to identify database security vulnerabilities and prevent potential security risks.
User activity monitoring
The second method of auditing in databases is monitoring user activity. It is the process of monitoring user activity on the system in real time to detect any unauthorized activity or unusual user traffic.
In large organizations such as banks or manufacturing companies, user activity is monitored to detect any changes in normal work activity, such as unusually active sessions or attempts to access sensitive data at unusual times.
User activity monitoring helps identify suspicious activity and notifies database administrators of potential security risks.
Filtering logs and analyzing results
This is the process of extracting the necessary information from the log log and analyzing the results. The log filtering process may include steps such as searching for specific types of events or requests, filtering by time or users, etc.
Suppose a company has been found to have unauthorized access to sensitive data. Log filtering allows you to analyze the data associated with this incident in order to identify the causes and details of what happened, as well as identify potential security vulnerabilities and take corrective actions.
Analyzing the results of log filtering helps to determine which changes require practical solutions, compliance or technical security measures.
Examples of Successful Implementation of Security Methods
Let’s look at a few examples that can serve as clear evidence of the effectiveness of security methods in databases.
1) Management of access rights in Oracle Database. Oracle Database is one of the most widely used databases in the world and provides many security features, including access control. The system allows database administrators to control access to data by assigning specific roles and rights to users and user groups. In practice, this means that users will only be able to access the data they need to complete their tasks.
2) SSL encryption in MongoDB. MongoDB is a document-based database used by many large companies around the world. One of the security methods used in MongoDB is SSL encryption. SSL encryption protects data sent between the client and application server by encrypting the data before it is sent over the network. This helps prevent hackers from intercepting data.
3) Google Cloud SQL. Google Cloud SQL is a managed service that provides a MySQL cloud database. The advantage of Google Cloud SQL is that Google automatically implements many security methods into this service, such as data encryption at rest and in motion, access control, and access monitoring and control features.
4) Authorization methods in Microsoft SQL Server. Microsoft SQL Server is a fairly common relational database with a wide range of security features. In SQL Server, administrators can implement authentication policies to control access to the database. One of the authorization methods in SQL Server is Windows Authentication, which allows administrators to control database access using Windows accounts.
So , summarizing the main recommendations for database security, it is necessary:
1. Structuring access rights at the database and application levels.
This method involves managing user rights at the database and application levels. Proper structuring of access rights allows you to restrict a user’s access to only those data that are necessary for his work. This helps to avoid unauthorized access to the database.
2. Regular updating of passwords and encryption keys.
The next recommendation is to regularly update passwords and encryption keys. The more frequently a password or key is changed, the more difficult it is to intercept it and use it for unauthorized access to the database. This method helps keep data secure.
3. User activity monitoring and log analysis.
User activity monitoring and log analysis is the third best practice for database security. This monitoring allows you to identify unusual activity, risk events, and other data security issues.
These methods will help protect data from unauthorized access, hacking and leakage. To ensure security in databases, it is recommended to use all of these methods in combination with each other, thereby strengthening and increasing the level of data security.