Often our clients (usually small organizations without their own IT service) need to provide access to their terminal server (there will be a separate article on configuring and ensuring fault tolerance) via the global Internet. Of course, we advise you not to do this, but use a VPN to connect (we recommend our beloved SoftEther VPN Server), but if the client insists, then we try to secure him as much as possible. And that’s just about how we achieve this and will be discussed in this article …
The first program we will discuss is called Cyberarms Intrusion Detection and Defense Software (IDDS).
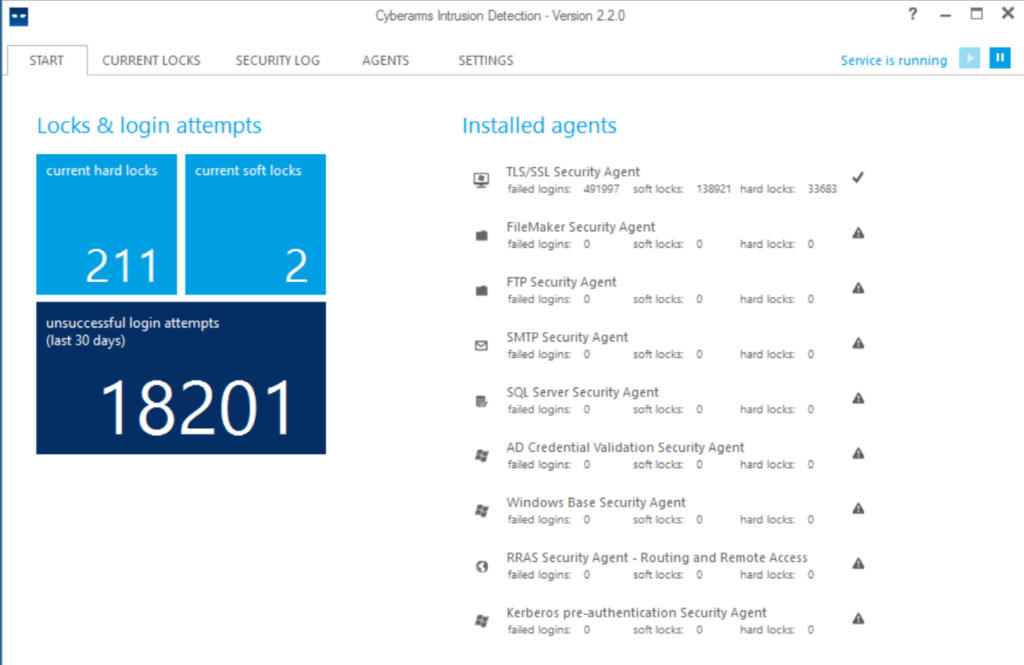
The principle of operation is quite simple, but at the same time effective: after several unsuccessful attempts to enter a password (the number for blocking is specified in the parameters), a Soft lock is triggered (suspicion of brute force), an incident is created in the log and the IP is marked as suspicious. If there are no new attempts, then after 20 minutes the address is removed from the list of watched. If the password brute-force continues, then the “attacker’s” IP address is added to the rule of the Windows firewall that denies connections (must be in an activated state), and thus the password guessing from this address is temporarily stopped since connections are completely blocked. The Hard lock will last 24 hours – this parameter is set by default. Eternal blocking, “Hard lock forever”, is not recommended to be enabled, otherwise, the number of IPs in the firewall rule will quickly “swell” and the program will slow down.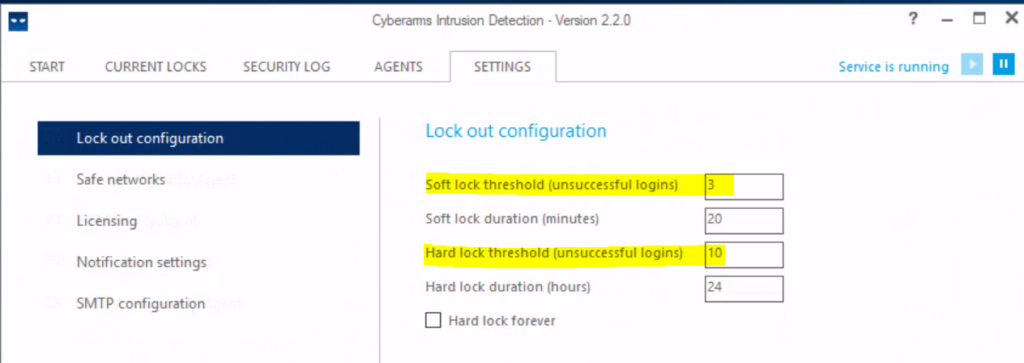
The second program is Duo Authentication for Windows Logon and RDP
is a multifactor authentication tool from Duo Security (Cisco), a commercial multifunctional product that works flawlessly and allows you to use smartphones, tokens and codes for 2FA.
Configuring the software is a little more complicated than the previous program, but thanks to good documentation from the developer, it is still quite fast.
- Register yourself an administrative account to access the control panel (Personal Account). We recommend immediately adding another administrator, because restoring access with the help of a developer is quite problematic, and precedents with the unexpected loss of an administrator’s smartphone often arise.
- Log into the Duo admin panel and go to Applications.
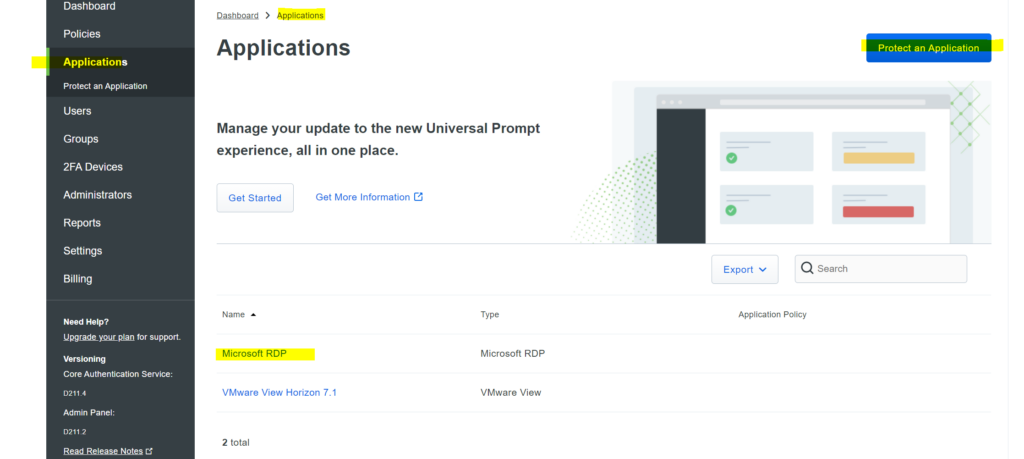
- Click “Protect Application” and find the entry for Microsoft RDP in the list of applications. Click Protect in the far right corner to set up your application and get your integration key, private key, and API hostname. You will need this information to complete the setup (during the Duo Authentication for Windows Logon installation ).
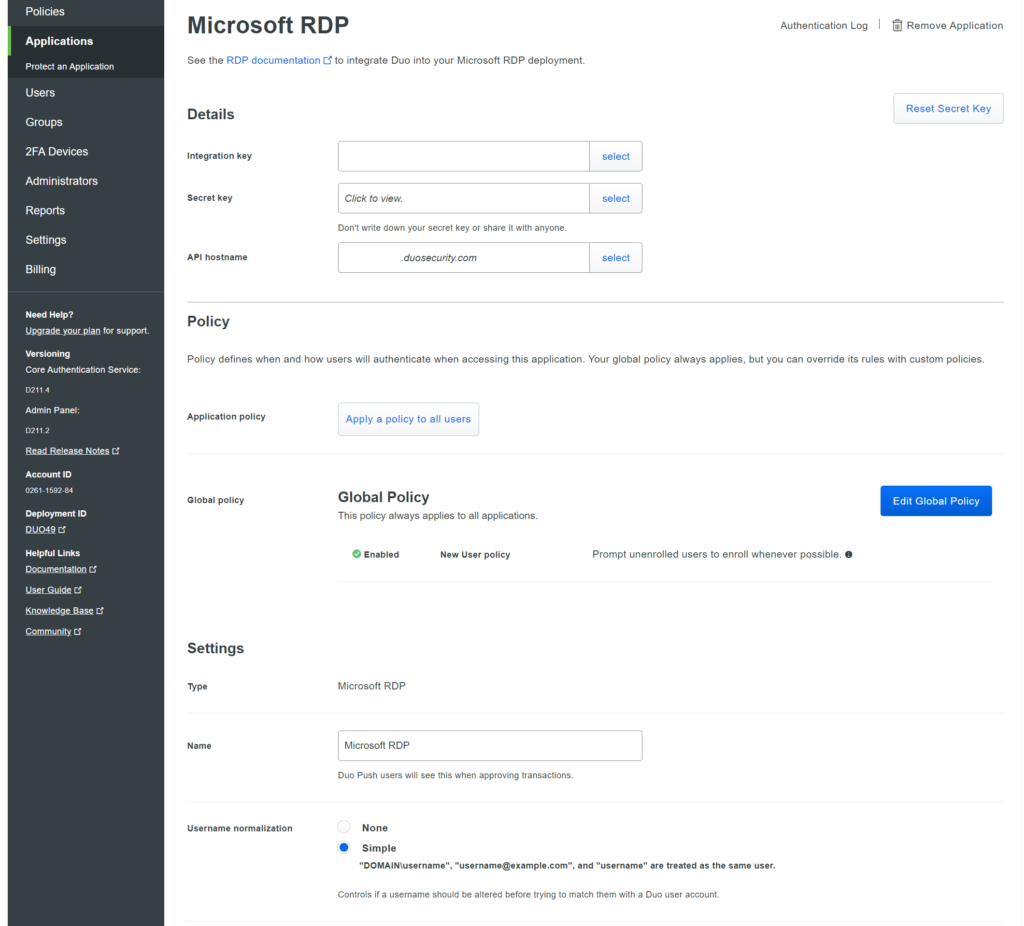 We recommend that you set the default policies for new users of the Microsoft RDP application to Deny Access , because no user who is not registered with Duo should be able to successfully authenticate. But to do this, you will need to add all users to Duo through the control panel manually or, which is much more convenient, through import from Active Directory (more on this later) and send them a link to activate the Duo Security application pre-installed on their smartphones.
We recommend that you set the default policies for new users of the Microsoft RDP application to Deny Access , because no user who is not registered with Duo should be able to successfully authenticate. But to do this, you will need to add all users to Duo through the control panel manually or, which is much more convenient, through import from Active Directory (more on this later) and send them a link to activate the Duo Security application pre-installed on their smartphones.
4. Download and install the Duo Authentication for Windows Logon installer package . During installation, enter the information obtained in the previous step.
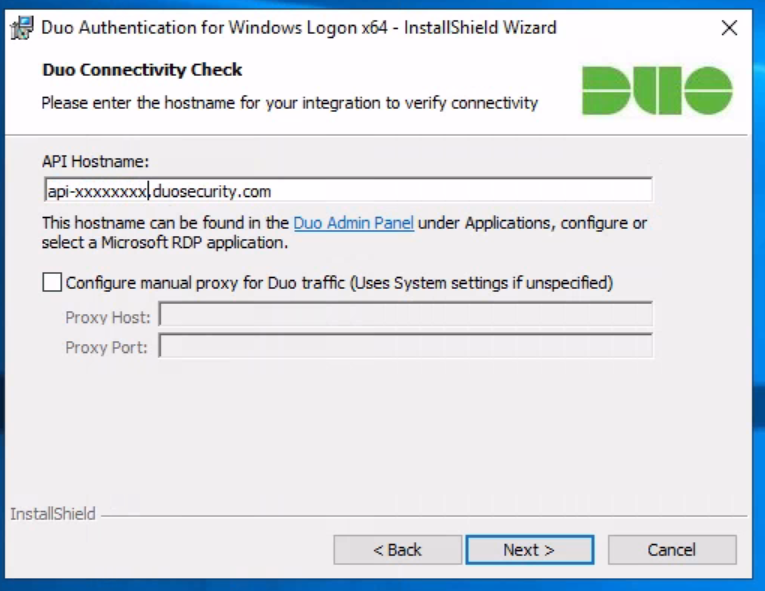 If you’d like to enable offline access using Duo MFA, you can do so now in the Offline Access Settings section of the Duo app page, or return to the admin panel later to set up offline access after the first two-factor login check. authentication.
If you’d like to enable offline access using Duo MFA, you can do so now in the Offline Access Settings section of the Duo app page, or return to the admin panel later to set up offline access after the first two-factor login check. authentication.
Also, during installation, we recommend that you install all 3 checkboxes in the checkboxes – these settings will allow you to access the OS without 2FA, for example, when using the hypervisor console or when there is no connection to Duo servers (often there is a big-time difference):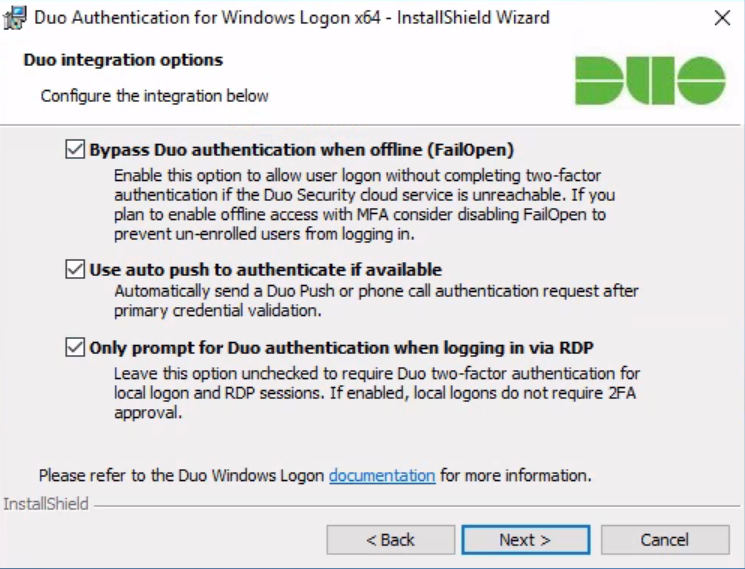
it will not be superfluous to remind you of the safe storage of all keys:
Treat your secret key like a passwordThe security of your Duo application is tied to the security of your secret key (skey). Secure it as you would any sensitive credential. Don’t share it with unauthorized individuals or email it to anyone under any circumstances!
After installing Duo Authentication for Windows Logon, you can add a user (your own, without administrator privileges) and activate the application on your smartphone. To do this, go to the Users section, click Add User – fill in the required fields. Next, add a phone to the user (section Phones – Add Phone) and activate Duo Mobile (you can send an SMS to the user to activate the link if there is money on the balance, or manually via email or in another convenient way).
 Now, upon connection and successful authorization (by login and password), the user will be sent a push notification to the smartphone with the Duo Mobile application activated:
Now, upon connection and successful authorization (by login and password), the user will be sent a push notification to the smartphone with the Duo Mobile application activated:
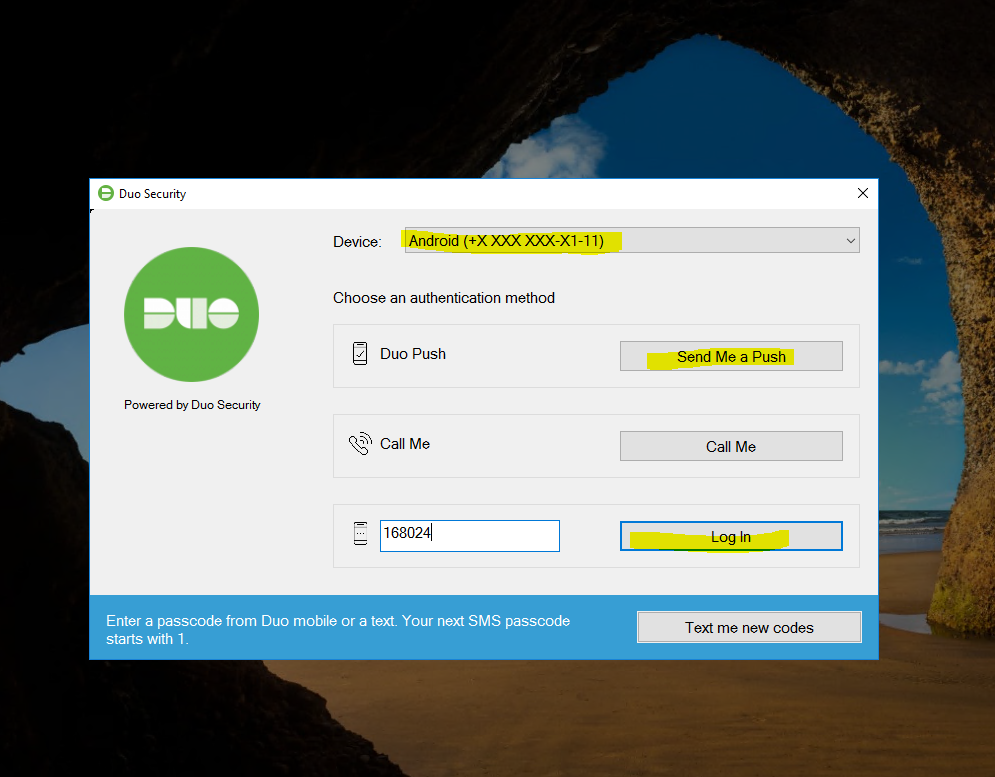
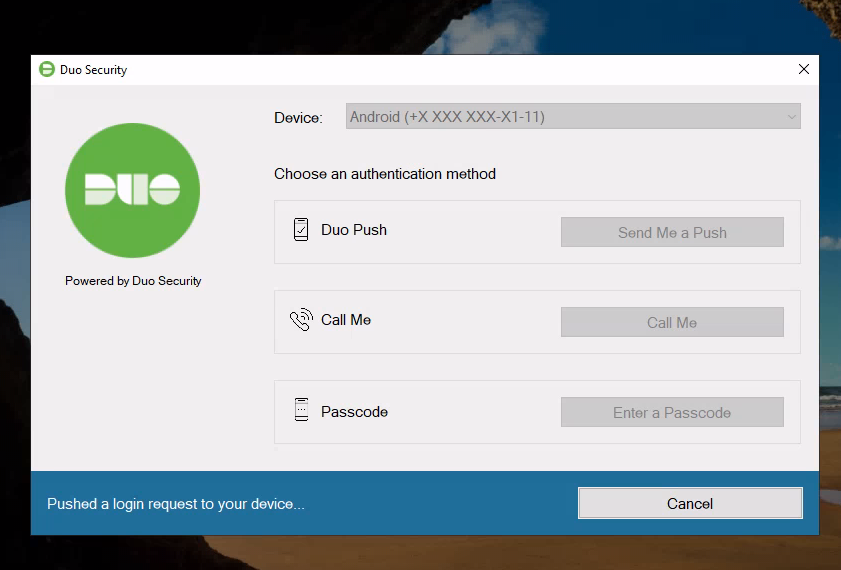 If the smartphone does not have access to the Internet (and, accordingly, Push will not come), then you can confirm authorization with the generated code (Passcode) from the application:
If the smartphone does not have access to the Internet (and, accordingly, Push will not come), then you can confirm authorization with the generated code (Passcode) from the application:
 Configuring user synchronization with the global catalogue (Azure AD – Active Directory – LDAP) is well described in the developer documentation, I just want to clarify that this is a paid functionality. The main component for user synchronization is Duo Authentication Proxy – software that provides a connection to the directory.
Configuring user synchronization with the global catalogue (Azure AD – Active Directory – LDAP) is well described in the developer documentation, I just want to clarify that this is a paid functionality. The main component for user synchronization is Duo Authentication Proxy – software that provides a connection to the directory.
If you are using RDWEb (client access or gateway), then another component comes in handy – Duo Authentication for Microsoft Remote Desktop Web . Configuring it is similar to Duo Authentication for Windows Logon and should be straightforward.
Summing up, we note that the considered software is not a panacea for all ills for public services (accessible from the Internet), because there are vulnerabilities, the exploitation of which allows malicious actors to bypass even such measures to ensure the security of the OS/infrastructure as a whole. Therefore, you must always take a comprehensive approach to this issue – monitoring, auditing and regulatory procedures for updating will allow you to feel protected in this turbulent world. Protect your data!