Microsoft has introduced a new Azure-based security solution to protect smart home devices – IoT Azure Defender. The system is implemented on the principle of a clientless firewall that controls external connections and requests to IoT devices on the home network. Azure Defender integrates with the existing information security product Azure called Sentinel. It is in the Sentinel panel that the defender of IoT devices displays all the basic information. In addition, Defender integrates with third-party solutions such as SIEM, CMDB and SOAR, which allows you to customize continuous monitoring of the infrastructure under control.
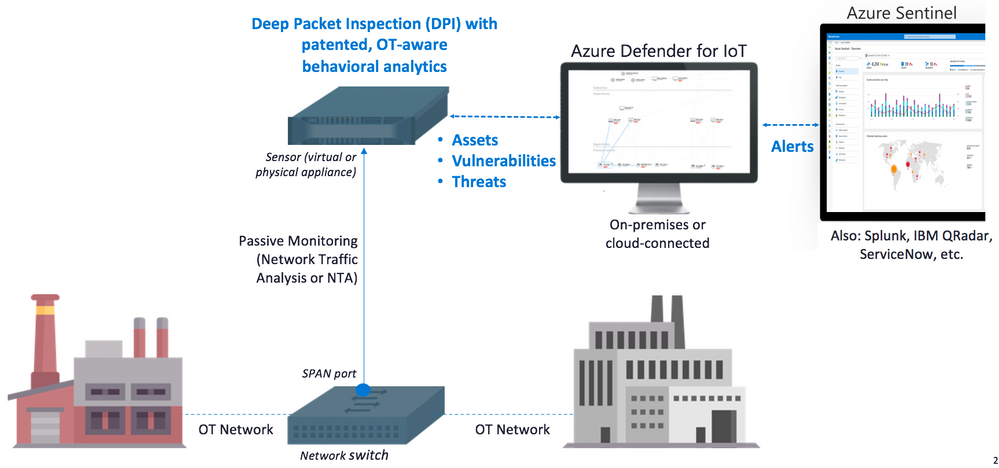
Security loop diagram based on Azure Defender bundle and Azure Sentinel dashboard
Azure Defender is focused on providing security monitoring for specialized device types, applications, and Machine-to-Machine control, that is, when your coffee maker decides to communicate with a vacuum cleaner or microwave. The solution supports specialized industrial protocols Modbus, DNP3, BACnet and a number of others, which are actively used in creating IoT device environments and closed systems of a smart home.
According to the developers, this adds transparency to improperly configured, unmanaged or unconnected IoT devices, as a result of which it becomes much more difficult for hackers to attack them in order to gain an access inside the network of both private households and in the networks and infrastructure of industrial enterprises and organizations.
The use of Azure in conjunction with Microsoft Sentinel is also interesting. In the standard configuration offered by the developers, it is proposed to use the Azure Sentinel panel for monitoring, which will receive all notifications from the Defender screen. Alerts are based on detection and analytics mechanisms for security perimeter violations, security policy violations, industrial malware detection, anomaly detection and incident detection, including at the sensor level. It all works through the collection and analysis of ICS network traffic.
Alerts “based on real-time traffic analysis” cover a wide range of incidents, including alerts of the following types:
- unauthorized device is connected to the network;
- unauthorized connection of the device to the Internet;
- unauthorized remote access;
- network scan operation detected;
- unauthorized programming of a PLC (programmable logic controller);
- changing the firmware version;
- “PLC Stop” and other potentially harmful commands;
- device is suspected of intentionally disconnecting;
- error requesting Ethernet / IP CIP service;
- BACnet operation error;
- unauthorized operation DNP3;
- Master-Slave authentication error;
- known malware was detected (for example, the ransomware WannaCry, EternalBlue, etc.);
- unauthorized login via SMB.
The list of threats that Defender controls is wide enough. At the same time, the solution is not a “standardized” antivirus or firewall that catches everything, but an IoT solution. It implements both monitoring of attacks on firmware, and monitoring of attempts to capture control / disable the device from the outside. The latter is extremely important for IP cameras in enterprises, which cybercriminals will tend to disable rather than take control of themselves.
But the developers did not limit themselves to the standard response list. Apparently, for the industrial segment, first of all, it is offered the opportunity to expand the list of alerts for monitoring in manual mode, that is, the administrator will be able to determine the most vulnerable points of his circuit and draw the system’s attention to them.
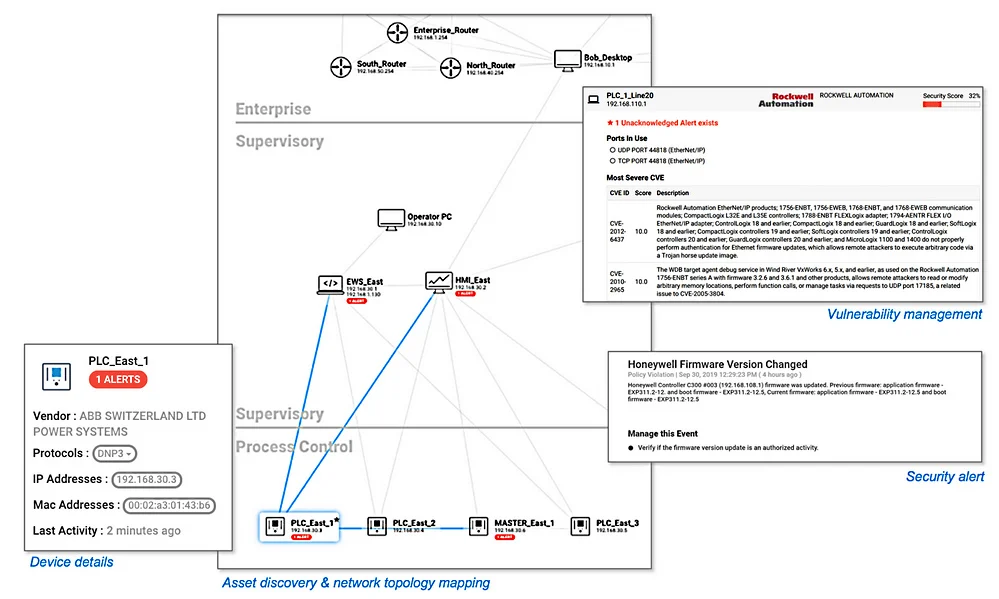
The custom alert works in the same way as the pre-installed one, and notifies the owner that a situation has arisen that requires his attention. In theory, even household owners will be able to use these features. For example, the physical disconnection of any devices or sensors may indicate an emergency in a house or apartment.
The product presented by Microsoft is one of the few software packages in recent years that has a dual purpose and is applicable both in the industrial field and for individuals. In recent years, the company has increasingly focused on business development, leaving the consumer segment at the mercy of Windows 10 patches and some lines of personal devices. Azure, in general, is promoted exclusively as a platform for business with solutions that comply with this policy.
The problem of IoT botnets has been quite acute for at least five years. Since the moment manufacturers began to implement smart functions, remote control via the Internet and other sensors into their equipment, the world has already faced massive DDoS attacks through cameras, refrigerators and irons several times. One of the reasons why such massive attacks became possible lies in two global problems from the field of information security culture.
On the one hand, we have absolutely disorderly manufacturers whose only goal is to introduce a “smart” function into another coffee maker in order to triple its cost and roll out a “new” device to the market. At the same time, the cheapest solutions and components are used. Manufacturers of household appliances generally do not like to spend money on computing power, which was clearly learned by buyers of “smart” TVs in the early and mid-2010s.
On the other hand, these devices, which have a couple of megabytes of memory, a simple firmware at the chip level and a Wi-Fi module for communicating with the owner’s smartphone over the network, end up in a completely unprotected home circuit. We still live in a world where the vast majority of routers within private households are equipped with a factory set of login and password. Although, the default configurations of IoT and IP devices are a problem not only for individuals, but also for large organizations.
We have already encountered botnets based on IoT devices. The Mirai botnet alone, which appeared in 2016, attacked millions of devices around the world, and then took an active part in massive DDoS attacks. By the way, his problem has not gone anywhere: the botnet and its updated versions were actively mentioned up to 2019, and in April 2020 we encountered a descendant of the Mirai botnet and the Qbot banker – the Dark Nexus botnet, which massively attacked routers and smart devices using both factory data and expolites.
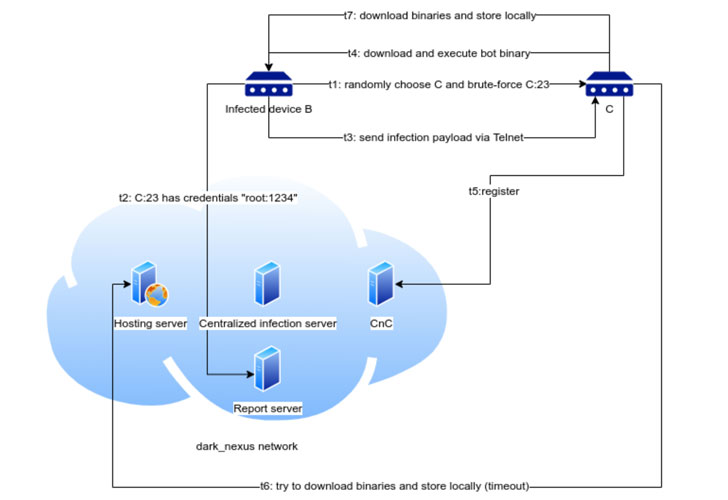
Dark Nexus attack scheme
Microsoft Defender is not a panacea for all the security problems of smart devices and routers in the field, but it is one of a number of solutions that can make life much easier for administrators and owners of smart home systems. As mentioned above, one of the advantages of Azure Defender is the lack of a client and works as a firewall. Moreover, anyone can try the preliminary version of the system absolutely free. You can also connect the 30-day trial of Azure Sentinel and work with the full bundle of the screen and dashboard offered by the developers from one manufacturer.