All online businesses need a stable and reliable infrastructure. The most advanced advertising campaigns, go-to-market and customer retention strategies lose their meaning if the store’s website is systematically unavailable, and payments are accepted only once. All of this is true for the cybercriminal business as well. In this post, we will tell you how the hacker infrastructure works and how to ensure the smooth operation of criminal services.
Each cyber group has its own specific set of requirements for network infrastructure. Someone needs temporary servers for brute-force passwords, network scanning or phishing emails, others need bulletproof hosting hidden behind a chain of reverse proxies. However, all the diversity boils down to several typical scenarios:
- hosting sites with illegal or questionable content,
- management infrastructure hosting,
- hosting service applications and components,
- hosting anonymizers, forward and reverse proxies,
- dedicated servers for scanning and brute force attacks,
- platforms for phishing and spamming.
Thus, the criminal network infrastructure generally consists of the following areas:
- special hosting services,
- hosting based on compromised servers,
- confidentiality and anonymity services,
- DNS services.
Let’s take a closer look at these components and start with dedicated hosting services.
Bulletproof hosting
Any illegal activity sooner or later leads to the fact that the resources associated with it become the object of the attention of law enforcement agencies. And then the IP addresses of these resources are blocked, the servers are seized, and the domains are partitioned. This situation leads to the disruption of cyber attacks and the need to spend on organizing new infrastructure. To avoid such a situation, illegal structures resort to services that are immune to police requests.
For example, the legislation of Belize and Seychelles allows companies providing such hosting services to ignore all requests from law enforcement agencies regarding resources hosted at their facilities. As a result, many bulletproof hosting sites are hosted there.
Another example is placing a criminal hosting in a private house. It was such an illegal data center, which contained more than 100 servers, that the Ukrainian police recently discovered and eliminated.
Fast-flux services
Fast-flux is a completely legal technology that is used to provide increased service availability and load balancing by constantly switching domain name resolution to a pool of IP addresses. This approach allows criminals to achieve increased resistance to hacking and interceptions, allowing them to hide the location of their server. A pool of IP addresses is often used to chain reverse proxies and can be provided by several resources: rented cloud VPS, botnet hosts, or compromised machines.
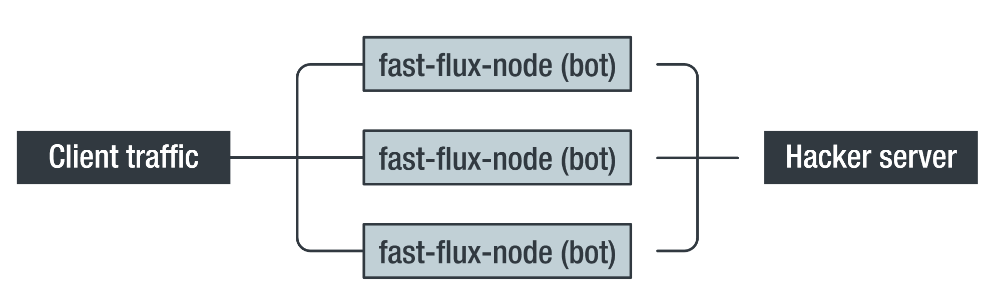
The essence of the fast-flux method is to use short TTL (time-to-live) for DNS A records. This prevents staging DNS servers from caching the domain name and forces them to always request permission from the advertised Domain Name System (DNS) servers. Low TTL values allow attackers to direct the domain to IP addresses in a dedicated pool with high frequency and ensure service availability even if some of the addresses are compromised or banned by the ISP.
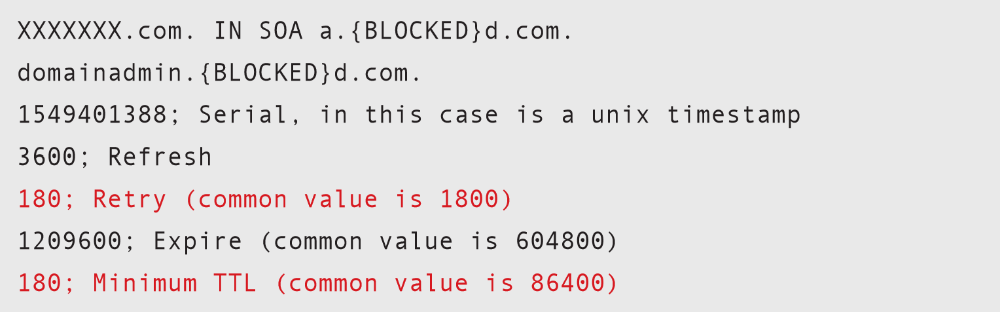
TTL values shown in red are set with unusually low retries and minimum TTL times (in seconds). Under normal circumstances, this will put additional load on the DNS server, but in the case of fast-flux, the goal is to suppress the caching mechanism so that the client is presented with a valid IP address, which is currently provided by the “fast-flux” infrastructure.
Fast-flux services tend to be more expensive than bulletproof hosting because their operator has to maintain a pool of IP addresses to provide a “fast-flow” infrastructure, which requires additional costs.
DDoS protection
Cybercriminal groups compete with each other no less than legal organizations, and as a means of competition, they arrange attacks on denial of service to the resources of competitors using Layer4 and Layer7 methods. That is why many bulletproof services offer DDoS protection hosting or DDoS protection service that you can use for your resource.
As a rule, such services are provided by placing a specialized resource in front of the protected server, like a WAF (Web Application Firewall).
VDS from compromised hosts
Compromised servers are often used for hosting during one or more stages of their criminal monetization lifecycle.
To capture control are used:
- vulnerabilities in server software,
- bruteforce attacks,
- stolen API keys,
- stealing accounts through connected servers,
- phishing and fraudulent campaigns.
Password guessing is usually used in attacks against SSH, VNC and RDP services.
The credentials for accessing the captured servers are subsequently sold on hidden online stores:
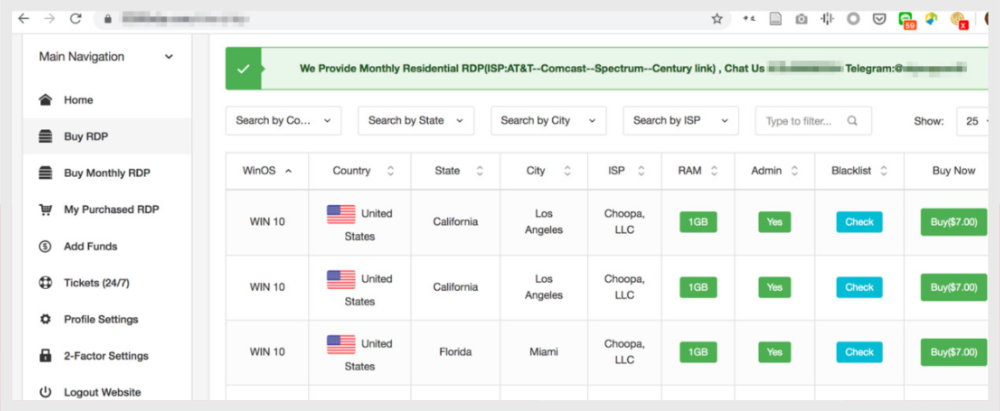
Taking over more secure servers may require zero-day vulnerabilities, which are also offered on cyber forums.
Announcement of the sale of a vulnerability in OpenSMTPD that allows you to compromise servers running FreeBSD, NetBSD, Debian, Fedora and Alpine Linux and use them for hosting
Compromising cloud hosting
From the attacker’s point of view, Google Cloud and Microsoft Azure are extremely accessible resources, since both allow users with a bank card connected to their account to try the services for free. This has led to cybercriminals actively collecting data from Google accounts with connected bank cards and then using it to launch instances of dedicated servers. Detailed tutorials are published for novice hackers:
For those who do not want to bother with hacking accounts, there are stores offering already hacked Microsoft Azure and Google Cloud accounts.
Socks, Proxy and SSH Tunnels
SOCKS and proxy services allow attackers to hide without attracting too much attention or triggering detection through network security monitoring tools.
In view of the demand for this tool, it is relatively easy to find resources offering to purchase SOCKS proxies, and you can pay for the purchase with cryptocurrency.
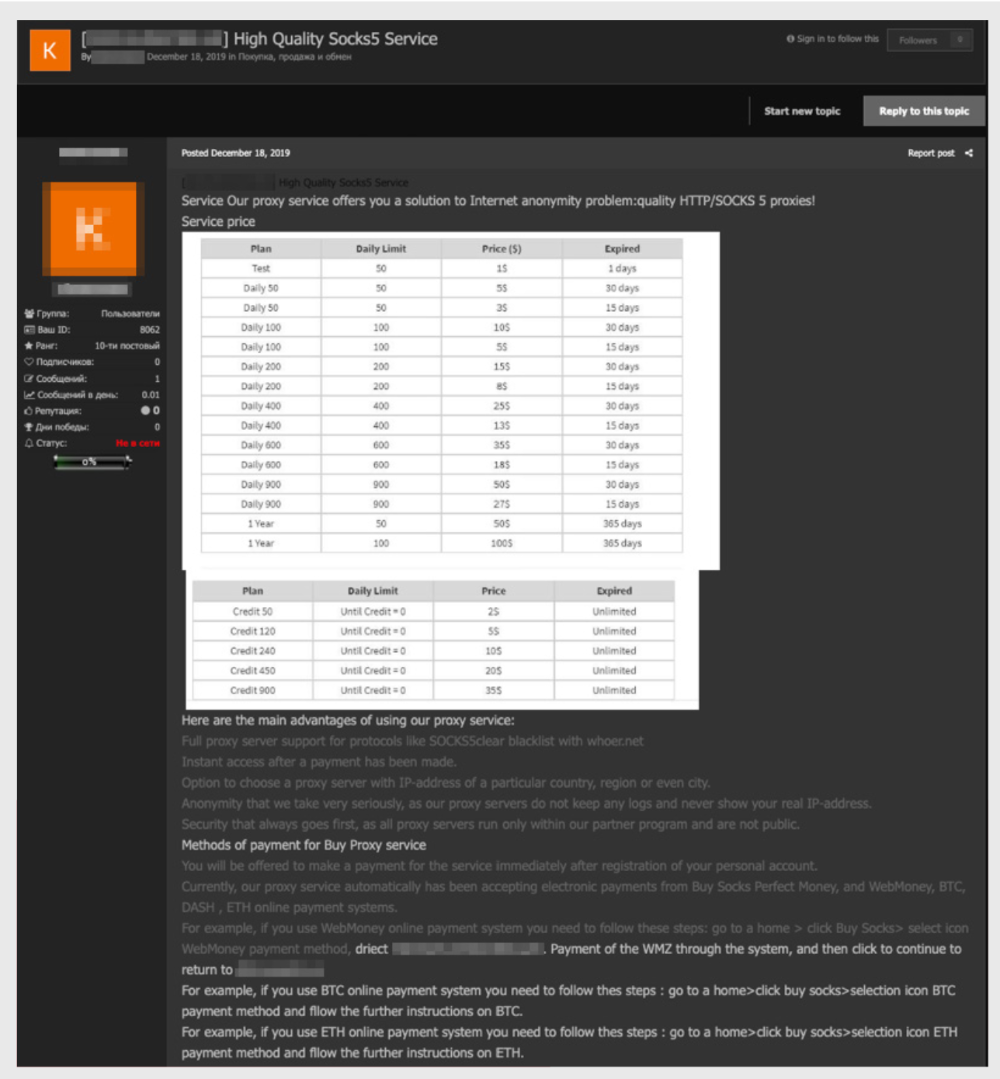
Another way of hiding communication is tunneling into legitimate protocols, for example, in SSH:
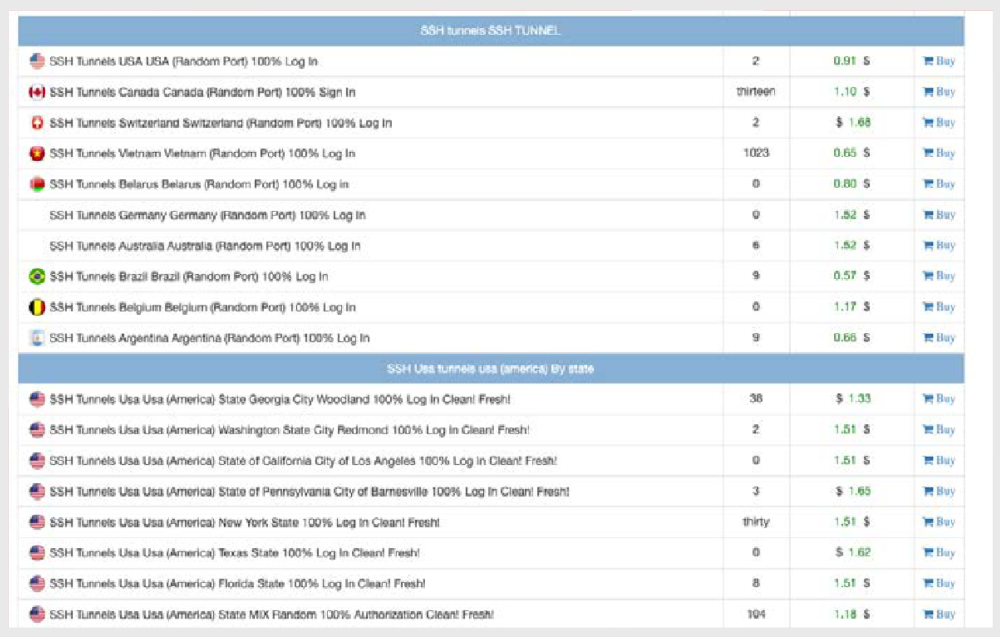
The cost of SSH tunnels depends on the country of location. Location is very important for some illegal activities. For example, banks’ anti-fraud systems correlate information about the cardholder with the geolocation of the IP address at which an attempt was made to use it. Therefore, criminals are willing to pay more to buy a tunnel that matches not only the desired country, but also the city.
Anonymizing VPN
Another service that is in demand in the cybercriminal environment is anonymous VPN, and in this part the preferences of the groups are divided: some prefer to use legal commercial VPNs like NordVPN or ProtonVPN, others rent similar services in the hidden market, and still others create their own infrastructure based on OpenVPN, WireGuard or SoftEther …
One of the signs that indirectly indicate that compromised hosts are used to provide VPN services is the indication of the “availability guarantee period” of the service. The lower the number, the more suspicious these services are. It is unlikely that a legitimate VPN provider will write in the terms that “If the provided credentials do not work within the next 24 (48 or 72) hours, the new credentials will be provided free of charge.” But this is exactly what is usually present in the offers of illegal services.
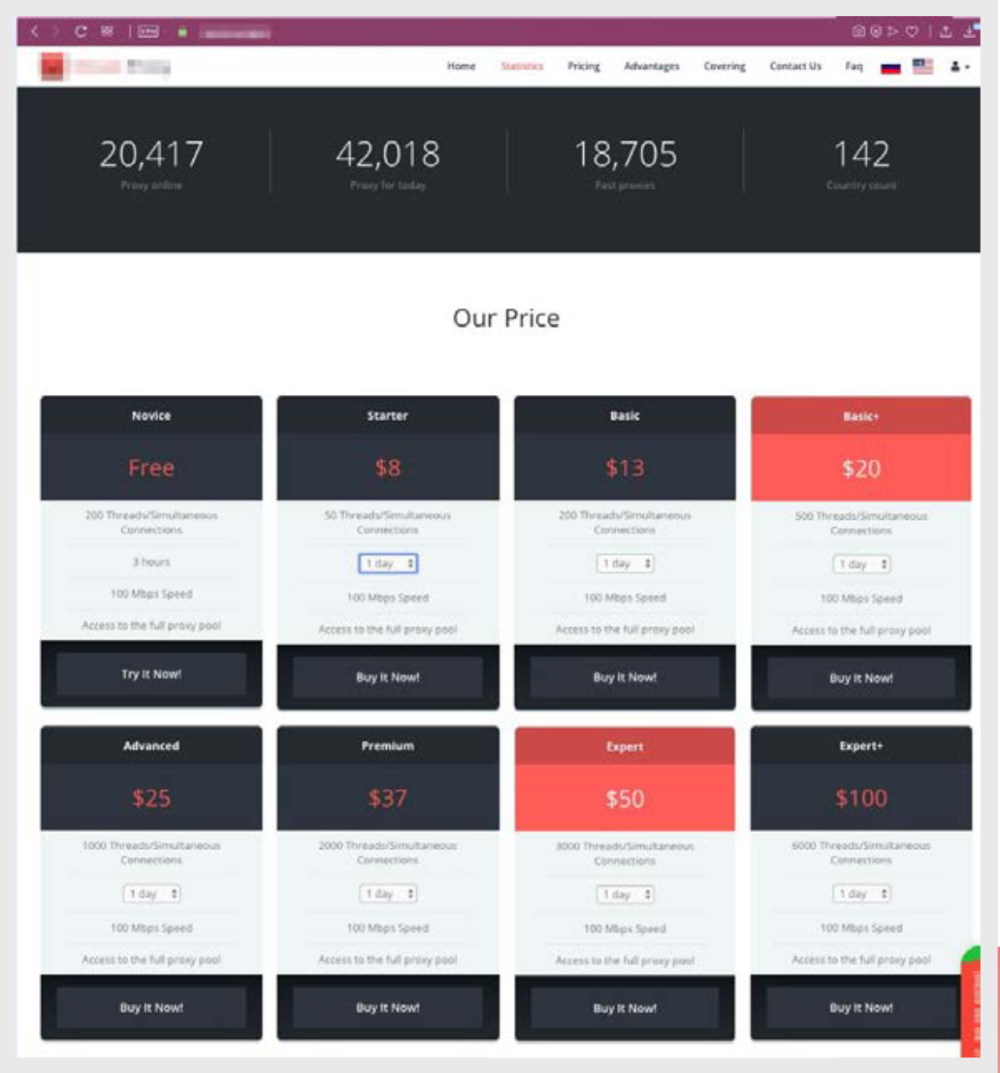
Another suspicious sign of a possible criminal nature of anonymization of services is the term of the contract. Legal VPN providers provide services for at least a month, while in the criminal environment, there are VPN services for a period of no more than one day. It is difficult to imagine cases of legal use for which such a short time is enough. However, for criminals, this is quite enough to
- check the validity of compromised bank cards,
- check the validity of compromised accounts,
- register accounts on cloud platforms or content hosting platform,
- make a fraudulent mailing on social networks,
- launch a malicious ad campaign.
Infrastructure offerings of shadow cyber business are not limited to relatively standard services. Studying the ads, you can find quite interesting services that are still in demand by niche clients, or are gaining popularity trends.
Mobile workplaces
Some vendors offer bulletproof mobile workstations to those wishing to be protected from outsiders.
Although the site’s policy formally prohibits the spread of malware, we found advertisements on the forum suggesting that other malicious actions are acceptable:
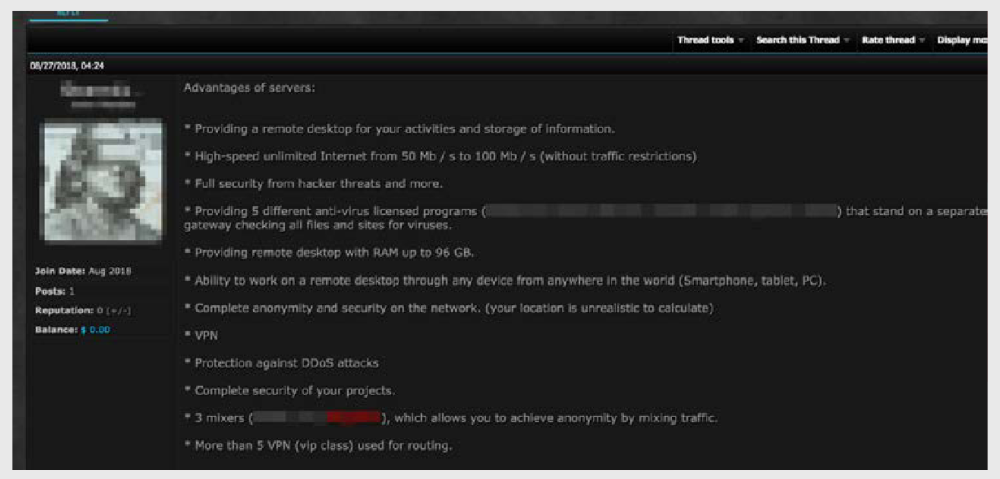
The proposal mentions complete anonymity, inability to locate the user, high-speed internet connection, DDoS protection, an outbound traffic mixer and five different VPNs. Despite the fact that direct port scanning, brute-force and malware distribution are not allowed, an attacker can commit other criminal actions using such AWPs.
Anonymizing traffic mixers
Tor isn’t the only way to hide from the watchful eye of law enforcement and competitors. Services offering robust workspaces have developed their own traffic mixers using a geographically dispersed network of routers. This traffic is mixed with the traffic of anonymous VPSs that periodically move between data centers located in different countries, making it even more difficult to trace such systems.
Custom services are also available for bundling VPN connections, Tor and geographically dispersed sets of routers. These combinations create such a complex chain of hosts and redirectors that it is almost impossible to trace.
For example, one of the services suggests using the following chain:
Host → VPN1 → VPN2 → TOR → gateway for bouncing traffic → traffic mixer → geographically distributed routers for bouncing traffic → remote desktop (RDP) for work → connection via other geographically distributed routers → Tor servers → output node → destination.
Conclusions
Our research has shown that the cybercriminal infrastructure is significantly more advanced than many researchers assumed. We believe that this particular component is one of the most mature aspects of the criminal business. Network worms are giving way to Trojans, browser exploits to targeted phishing attacks, and outright extortion is replacing the business model of information theft. However, the infrastructure on which all these actions are based remains in demand and is constantly evolving, offering new technically sophisticated services.
Cybercriminals need a reliable service that allows them to act while hiding from law enforcement agencies as long as possible. This demand has spawned a whole industry of semi-legal services that cater to cybercriminals, indirectly helping criminals. The problem is that providing reliable, untraceable hosting services is not illegal in and of itself. Solving this problem is a very important piece of the puzzle for those who are fighting cybercrime as a global problem.