So, we have a domain user or computer account. To continue testing, we need to collect available information for further attack planning. Let’s consider some of the tools that will help us to determine the search for the most critical systems, plan and execute an attack.
Bloodhound
One of the most important tools that is used in almost all internal penetration testing. The project is actively developing and supplemented by new features.
Information collected by bloodhound
The information collectors are SharpHound.exe (installed .NET v3.5 is required) and the script SharpHound.ps1 written in powershell. There is also a compiler written by a third-party Python developer, Bloodhound-python.
As a database, is used Neo4j, which has its own syntax and allows you to perform custom queries.
Out of the box are available 12 requests
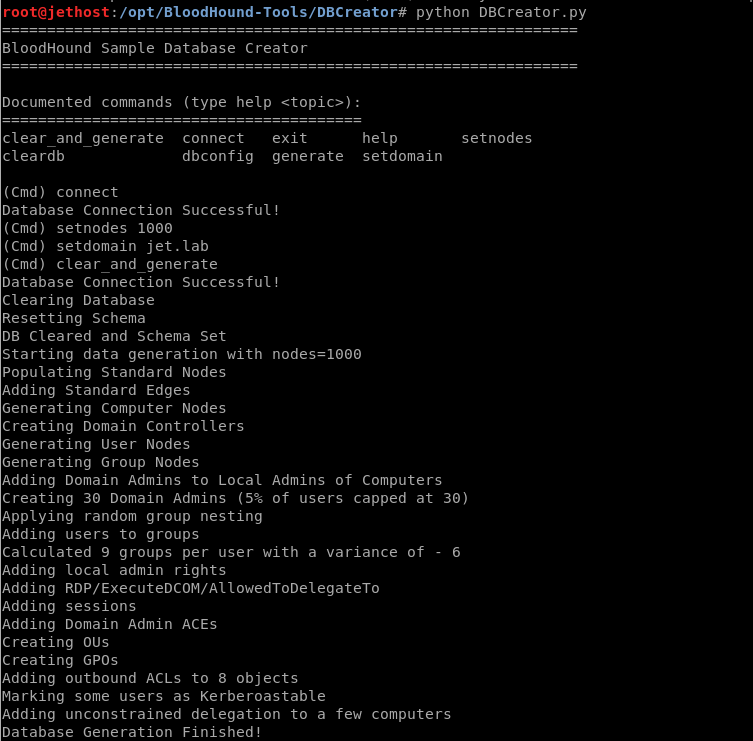
The developers also provide the DBCreator.py script, which allows you to generate a random database for testing.
Neo4j has a REST API. There are various utilities that can connect to the database and use the received data:
- CypherDog
- GoFetch
- ANGRYPUPPY
- gt-generator
CypherDogGoFetchANGRYPUPPYgt-generator
Let’s consider some of them.
Cypherdog
CypherDog is a BloodHound shell written in powershell. Includes 27 cmdlets.
By default, is required authentication to access the neo4j database. You can disable authentication by editing the neo4j.conf file. It needs to uncomment the line dbms.security.auth_enabled = false. But this is not recommended, since any user will be able to connect to the database at 127.0.0.1:7474 (the default configuration).
Gofetch
GoFetch uses a graph created in bloodhound to plan and execute an attack.
Attack launch
. \ Invoke-GoFetch.ps1 -PathToGraph. \ PathFromBloodHound.json
gt-generator
gt-generator, using BloodHound data, makes it easy to create golden tickets. To receive a golden ticket,are required only the username and password hash of the KRBTGT user.
python gt-generator.py -s 127.0.0.1 -u user -p pass administrator <KRBTGT_HASH>
Powerview
PowerView is a Powershell framework included in PowerSploit. The following is a list of some cmdlets that will help you gather information about a domain.
Adidnsdump
When using integrated DNS in Active Directory, any domain user can query all the default DNS records.
Tool Used: Adidnsdump.