Last week Threatpost published a list of the most popular vulnerabilities among cybercriminals. The rating method is rather controversial, but it has a right to exist: the Cognyte company analyzed discussions on 15 criminal forums for the period from January 2020 to March 2021. Any mention of vulnerability identifiers in the CVE database was recorded, so the final list reflects the intentions of the criminal world rather than actual actions.
Nevertheless, the result partly coincides with the exploits actually used in various attacks. In the first place was the vulnerability CVE-2020-1472, also known as ZeroLogon – a hole that allows you to take control of a domain controller. A patch for Windows Server OS starting from 2008 R2 was released in August 2020.
The second most mentioned vulnerability is CVE-2020-0796, also known as SMBGhost. Closed in March 2020, it threatens both Windows servers and clients using the SMBv3 protocol. TOP 3 closes the CVE-2019-19781 vulnerability in Citrix Application Delivery Controller and Citrix Gateway solutions.
Three more vulnerabilities from the list are the BlueKeep hole in Remote Desktop Services for Windows and two vulnerabilities (CVE-2017-0199 and CVE-2017-11882) in Microsoft Office from 2017.
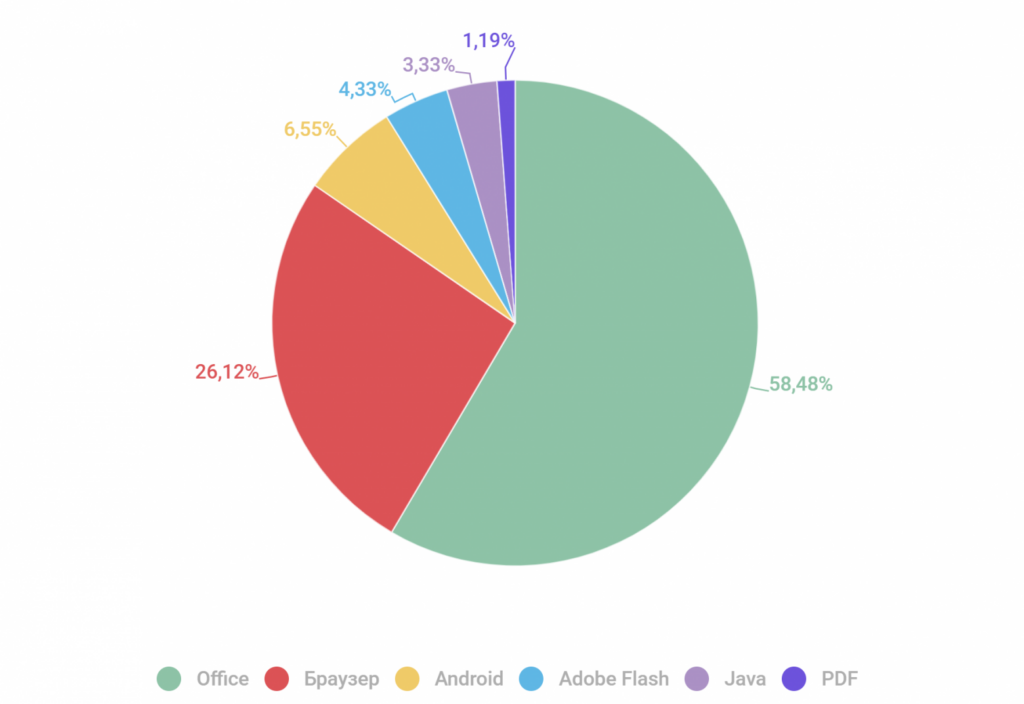
These general statistics may not show trends in targeted attacks, but vulnerabilities in Microsoft Office are most often exploited in large-scale attacks on users. Moreover, according to the data for the first quarter of 2021, the same vulnerability CVE-2017-11882 is listed as the most frequently exploited. In second place in terms of real popularity are browser exploits, which are not mentioned at all in the analysis of discussions on underground platforms.
What else happened
Last week’s story about PrintNightmare vulnerabilities continued. Another issue has been identified in the Print Spooler service that has not yet been closed and, according to Microsoft, is not being exploited. The recommendation is the same: disable the print service where it is not used.
A critical vulnerability was found in the Woocommerce extension for WordPress used for online stores. An emergency patch was released last week, as exploiting the hole makes it possible to steal information down to credit card numbers.
It is also known about the LuminousMoth attack detected in the countries of Southeast Asia. This is a fairly rare case of massively distributed malware, although the organizers have a fairly narrow range of goals. Other technical features include the use of a fake Zoom client.
A study by experts from the Google Project Zero team describes an attack on officials in Europe using vulnerabilities in the LinkedIn messenger and the Zero-Day vulnerability in the Safari browser.