One of the really useful innovations in Windows Server 2019 is the ability to enter servers without having to do Sysprep or a clean install. Deploying infrastructure on virtual servers with Windows Server has never been easier.
Today we’ll talk about how easy it is to install and manage Active Directory through Powershell.
Set the role
RSAT or local server with GUI
First you need to add the server to RSAT. It is added on the main page using a domain name or ip address. Make sure that you enter the login in the format local \ Administrator, otherwise the server will not accept the password.
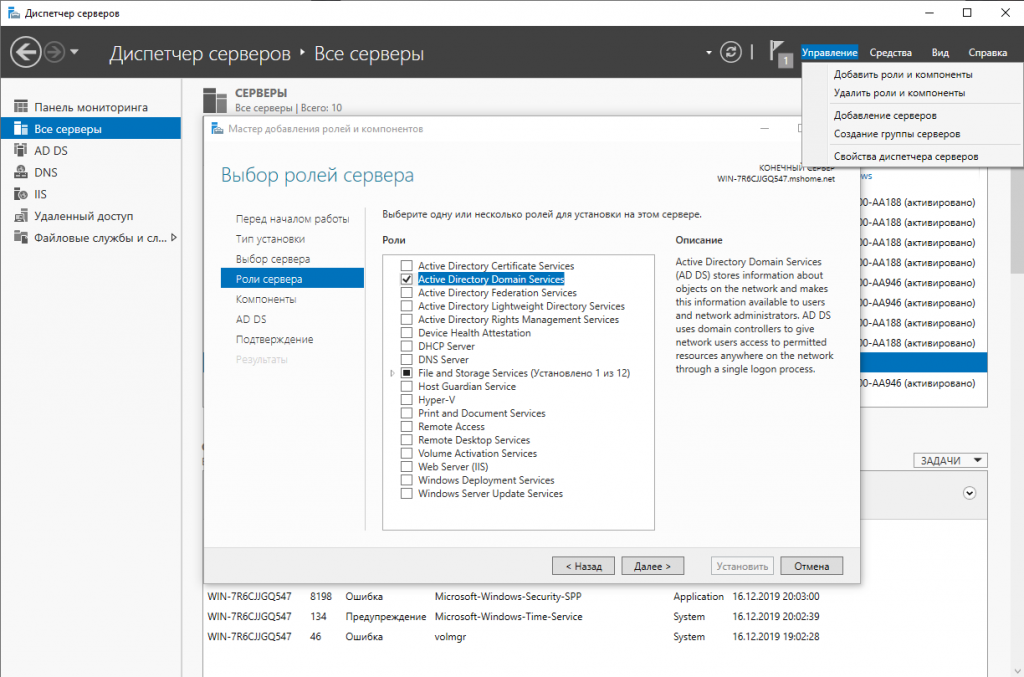
Go to add components and select AD DS.
Powershell:
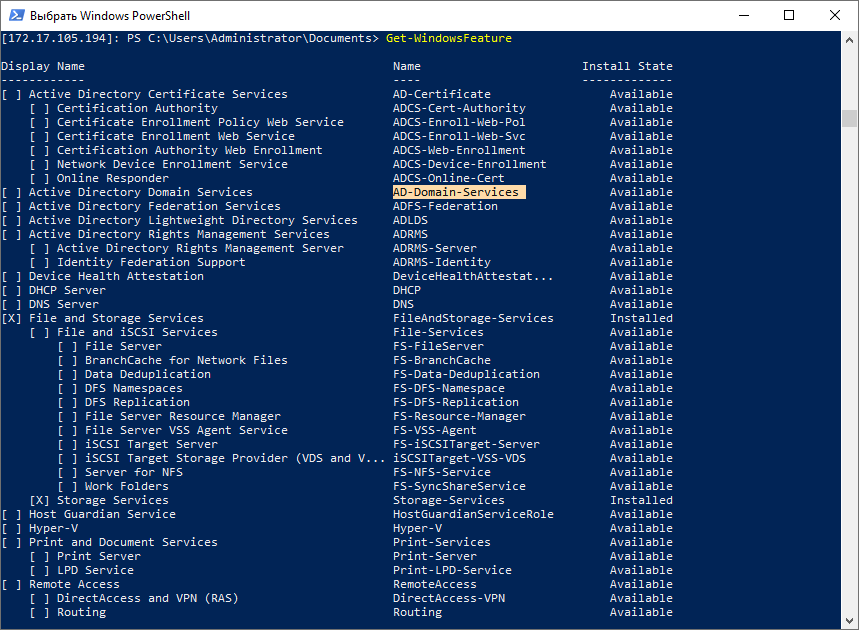
If you do not know the name of the system component, you can run the command and get a list of available components, their dependencies and names.
Get-WindowsFeature
Copy the name of the component and proceed with the installation.
Install-WindowsFeature -Name AD-Domain-Services
Windows Admin Center:
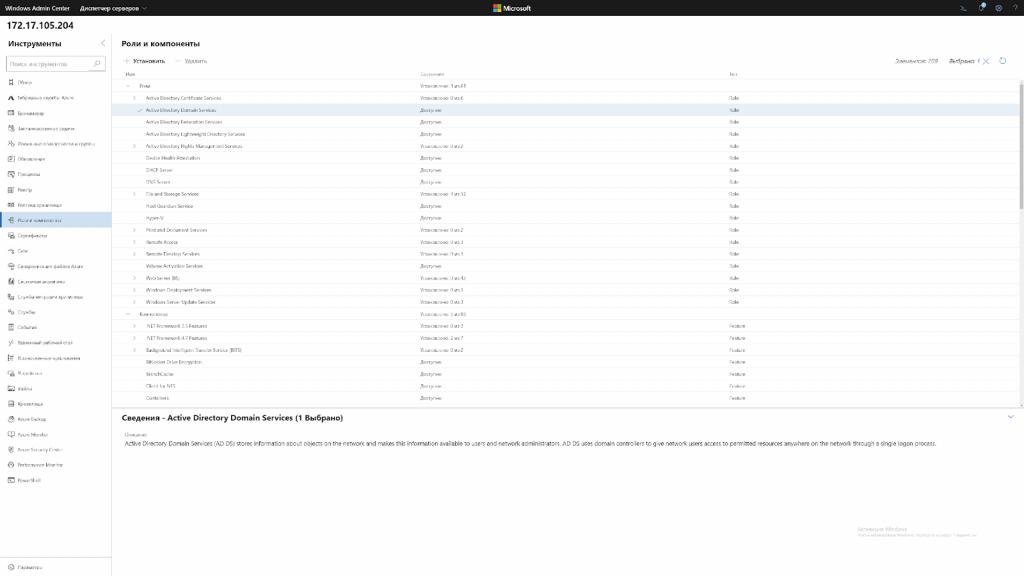
Go to “Roles and Features” and select ADDS (Active Directory Domain Services).
And that’s literally all. It is currently not possible to manage Active Directory through the Windows Admin Center. Its mention is nothing more than a reminder of how useless it is so far.
Raise the server to a domain controller
RSAT or local GUI servers:
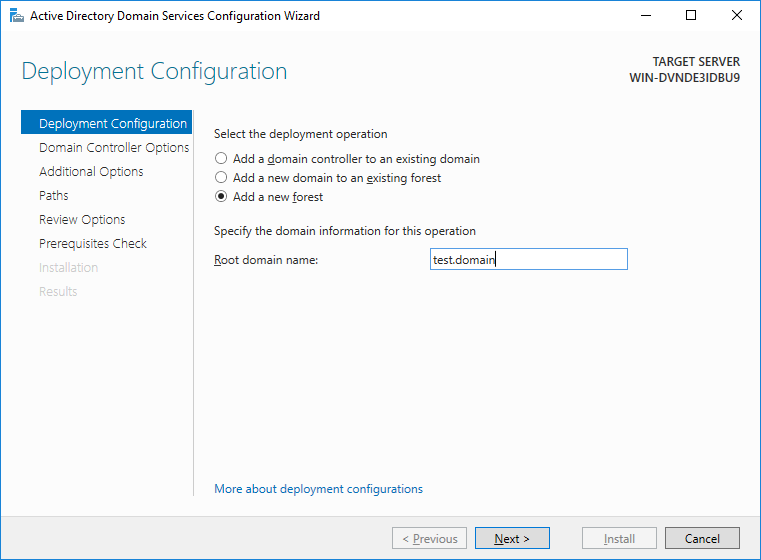
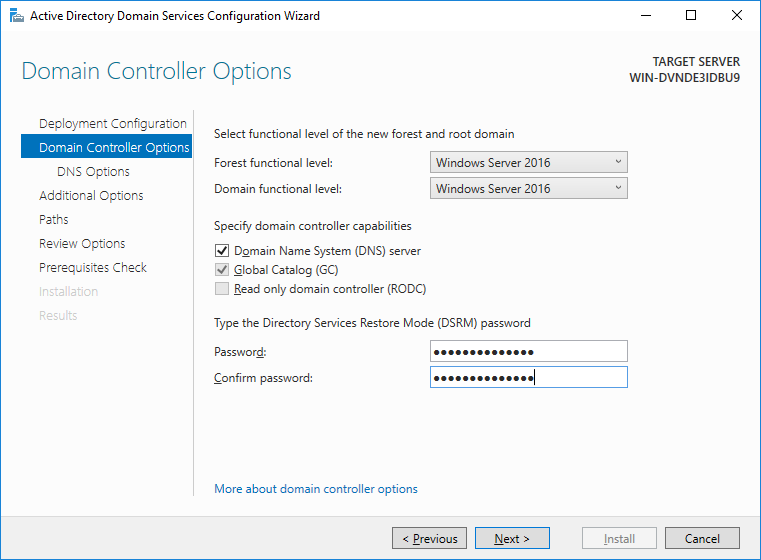
We strongly recommend that you leave everything as default, all components out of the box work fine and do not need to be touched without special need.
Powershell:
First you need to create a forest and set a password for it. Powershell has a separate variable type for passwords – SecureString, which is used to securely store a password in RAM and transfer it across the network.
$pass = Read-Host -AsSecureString
Any cmdlet that uses anyone’s password must be entered in this way. First, write the password to SecureString, and then specify this variable in the cmdlet.
Install-ADDSForest -DomainName test.domain -SafeModeAdministratorPassword $pass
As in the installation via the GUI, even the output to the console is the same. Unlike a server with a GUI, both installing a role and installing server as a domain controller does not require a reboot.
Installing the controller using RSAT takes longer time than using Powershell.
We manage the domain
Now, to understand how much Active Directory management differs through Powershell and AD AC (Active Directory Administrative Center), let’s consider a couple of working examples.
Create a new user
Let’s say we want to create a user in the Users group and want him to set a password for himself. Via AD AC, it looks like this:
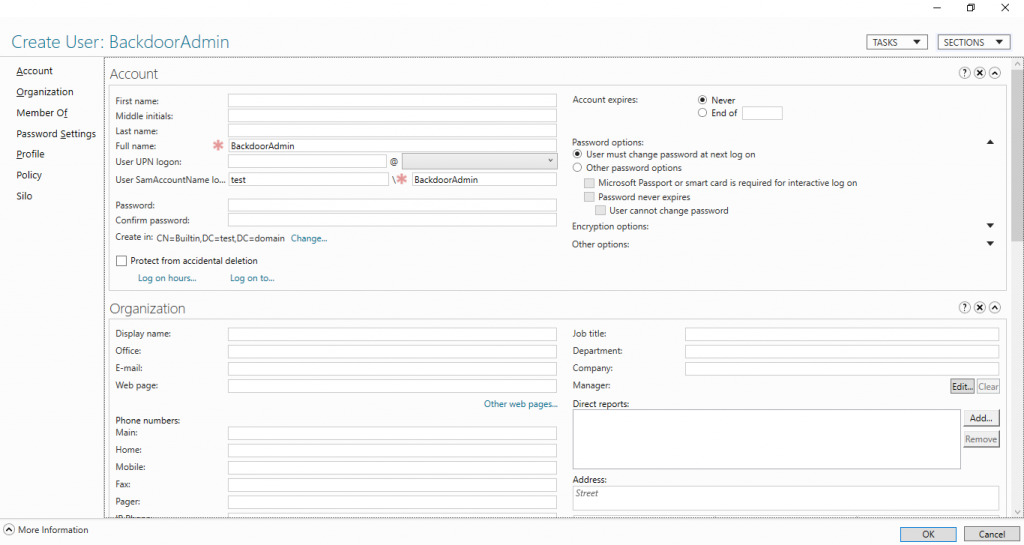
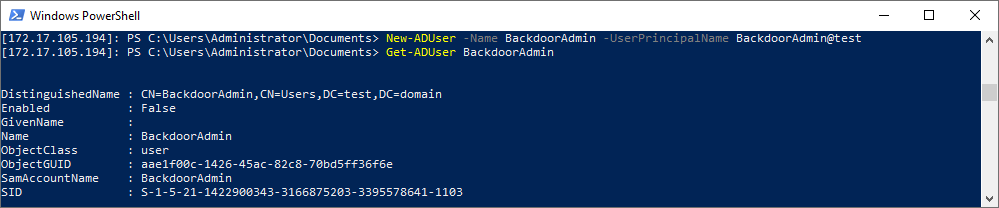
New-ADUser -Name BackdoorAdmin -UserPrincipalName BackdoorAdmin@test Get-ADUser BackdoorAdmin
There are no differences between AD DC and Powershell.
Enable User
RSAT or local GUI servers:
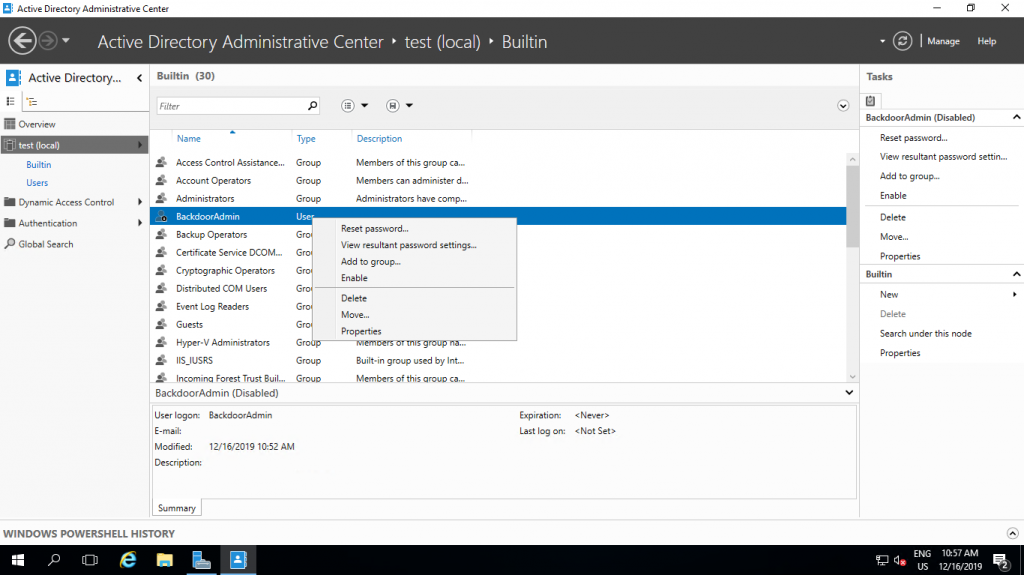
Through the GUI, the user must first set the password corresponding to the GPO and only after that it can be turned on.
Powershell:
Powershell is almost the same thing, only the user can be made active even without a password.
Set-ADUser -Identity BackdoorAdmin -Enabled $true -PasswordNotRequired $true
Add user to group
RSAT or local server with GUI:
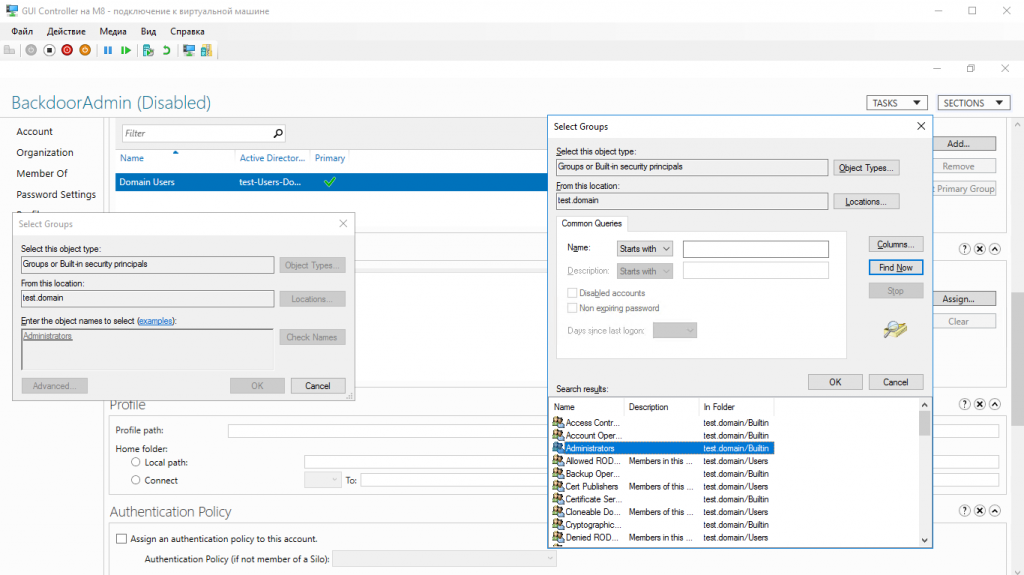
Using AD DC, you need to go to user properties, find the column with user membership in groups, find the group in which we want to place it and add it finally, and then click OK.
Powershell
If we do not know the name of the group we need, we can get a list of them using:
(Get-ADGroup -Server localhost -Filter *).name
You can get a group with all the properties like this:
Get-ADGroup -Server localhost -Filter {Name -Like "Administrators"}
Finally, add the user to the group:
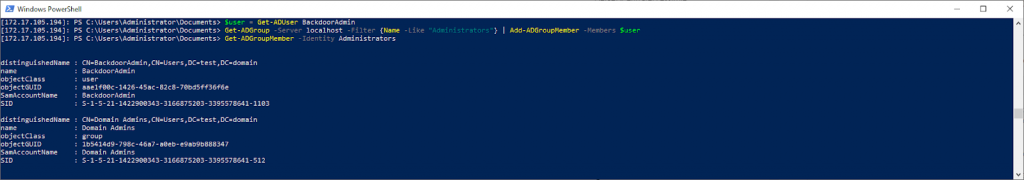
Further, due to the fact that everything is an object in Powershell, we, like through AD DC, must first get a user group and then add it to it.
$user = Get-ADUser BackdoorAdmin
Then we add this object to the group:
Get-ADGroup -Server localhost -Filter {Name -Like "Administrators"} | Add-ADGroupMember -Members $user
And check:
Get-ADGroupMember -Identity Administrators
As you can see, there are almost no differences in managing AD through AD AC and Powershell.
Conclusion:
If you have already encountered the deployment of AD and other services, then you may have noticed the similarities of the deployment through RSAT and Powershell, and how everything really looks like.
We hope the article was useful and interesting.
And finally, a couple of practical tips:
- Do not install other roles on a domain controller.
- Use BPA (Best practice analyzer) to speed up the controller a bit
- Do not use the built-in Enterprise Admin’s, always use your own account.
- When deploying the server on a white IP address, with forwarded ports or on VSD, be sure to close port 389, otherwise you will become the point of DDoS attacks amplification .