In the previous articles, we talked mainly about the static aspect of Docker security: vulnerable kernels, untrusted images, privileges that can be given or removed during startup, etc. And what if, despite all the security measures taken, the image started to show suspicious activity?
Best practices
The static countermeasures described in our articles do not cover all possible attack vectors. But what if in your own application are vulnerabilities or attackers use 0-day, which is not detected by the scanner? Runtime security can be compared to an anti-virus scanning in Windows, whose tasks include finding malware and preventing the further spread of the attack.
There is no need to replace static image verification with dynamic runtime protection, since preventing an attack is always better than repelling it. Use dynamic protection as an additional layer of security.
Detailed and convenient logs are very helpful for post-mortem analysis of attacks, the contents of which correlate well with changes made to the system.
Examples
Sysdig Falco is a software behavioral monitoring system designed to detect abnormal activity. The source code of the system is open. Sysdig Falco on Linux hosts acts as an intrusion detection system and is especially useful when using Docker, because it supports container-specific contexts when creating rules, for example container.id, container.image, Kubernetes resources or namespaces.
Falco rules can generate alerts for different types of abnormal activity. Let’s look at a situation where someone launched a shell in a container in production.
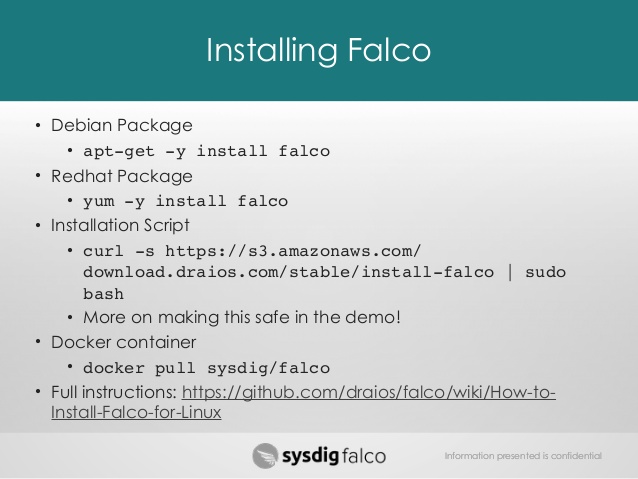
First, deploy Falco using an automatic installation script (not recommended for production; perhaps for testing purposes, it is better to install it in a virtual machine):
# curl -s https://s3.amazonaws.com/download.draios.com/stable/install-falco | sudo bash # service falco start
 Now run the shell in the nginx container:
Now run the shell in the nginx container:
# docker run -d --name nginx nginx # docker exec -it nginx bash
On the host, the following entry should appear at the end of the / var / log / syslog file:
Aug 15 21:25:31 host falco: 21:25:31.159081055: Debug Shell spawned by untrusted binary (user=root shell=sh parent=anacron cmdline=sh -c run-parts --report /etc/cron.weekly pcmdline=anacron -dsq)
Note, that Sysdig Falco performs its functions without making changes to the containers, what is very convenient.
Docker was created according to the most of security requirments and some of its features help to ensure it. However, do not forget about caution, since there is always a need to constantly monitor current trends and apply the best practices that have developed in this area. It’s also worth to use container-specific security tools to deal with Docker vulnerabilities and threats.