Amazon Cloud Watch
Cloud Watch is used to monitor the health / state of mainly all AWS cloud services, including standard server health monitoring, port availability, storage, database operation, a place on S3 and a lot of other checks.
There are 3 types of states in Cloud Watch – OK, ALARM, and UNSUFFICIENT DATA. The names speak for themselves: the check is in the OK state, in the error or alarm state, and also in the unknown state. For all of these conditions, you can configure triggers that will take an action when the counter changes to this state.
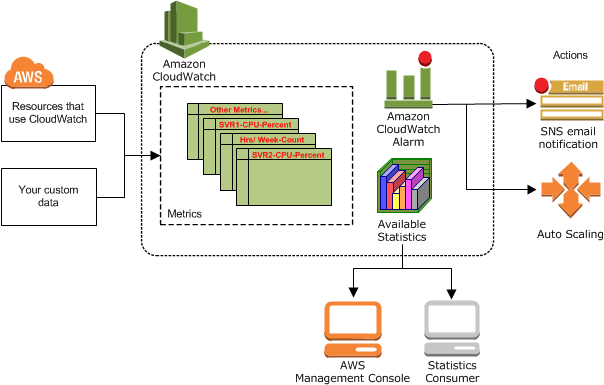
Auto-scaling, for example, is based on CloudWatch counters data. According to CloudWatch policies, triggers can launch new copies of servers to increase the application’s power and also stop work of unnecessary servers while reducing the load.
The console of this service provides almost all of Cloud Watch’s configuration functionality, but through the command line utilities it can be done much faster and more accurately than through the web interface.
Amazon Cloud Watch Billing
Cloud Watch service fees include the number of checks that has exceeded Free Tier. You can simply configure an elementary monitoring in this limit.
AWS Identity and Access Management (IAM)
The IAM service allows you to control access rights to all other AWS services. Having a lot of employees, it is necessary to divide the access between administrators, developers, test engineers and so on. Within one account can be created up to 80 user accounts, separated by groups, which are under control of security policies.
To each IAM user can be assigned:
- key pair
- login and password
- a couple of certificates
With keys and certificates, users can access APIs and command line utilities. With login and password – the console, which is available only for members of the organization. The address on the login screen of such a console looks like this: https://company.signin.aws.amazon.com/console. Each AWS account owner has the right to create his own corporate login screen.
Rules for limited access to AWS services, generated in JSON format:
{
"Sid": "Stmt1327249403354",
"Action": [
"ses:*"
],
"Effect": "Allow",
"Resource": [
"*"
]
}
Using such an example, members of the group have full access to SES service and them are allowed all actions related to SES.
IAM is also easy to use for a transferring rights for a short time to third parties, such as freelancers. Keys, certificates, and passwords you can quickly close and disable current access to AWS.
IAM Billing
Using IAM is completely free. The fee is charged only for resources consumed by users.