The competitive market pressure in various fields of activity has created a web-infrastructure which is very responsive to the environment. Modern web application deployment architectures are complex and require the integration of many heterogeneous technologies, creating the potential for multiple vulnerabilities.
Accelerated development cycles and constant updates of web applications further aggravate the situation. In such an environment, business risks are too high for companies to ignore, as vulnerabilities in web applications expose critical business operations and sensitive data to risk.
Significant financial losses can result from unforeseen delays in business processes, intellectual property theft, loss of customer trust and brand reputation. In a number of cases, web application protection becomes also a legal requirement, for example compliance with such standard for data security as Payment Card Industry Data Security.
Today’s trends in web services developing indicate the lack of common standards for secure programming of web apps, which leads to errors in software development and to serious vulnerabilities in web services that use these applications.
The situation is complicated by the fact that a vulnerable web app can be easily compromised even without the usage of specialized tools, only with the help of a browser. Protection of vulnerable web apps can be carried out either by eliminating vulnerabilities in a web app or by using specialized tools for web applications protection — Web Application Firewall or WAF.
Nowadays, the placement of traditional firewalls, Next Generation Firewalls (NGFW) or Intrusion Prevention Systems (IPS) around the network perimeter or at least as gateways to trusted network segments, is not a sufficient factor to ensure full protection of network infrastructure.
Attacks on web resources that manipulate software for malicious goals usually take place simultaneously with legitimate user sessions and mostly use standard HTTP (80) and HTTPS (443) ports. Blocking all the traffic at the port level is not an option, as access to web applications will be entirely blocked from the outside or inside. Such a dilemma of network protection is an excellent opportunity for hackers to seek for vulnerabilities at web application level.
Web Application Firewall is a security device (hardware or virtual) which primary mission is to provide protection of web portals and web apps by verifying the XML/SOAP semantics of streaming traffic, plus checking HTTP/HTTPS traffic in order to detect various attacks at the application level.
The firewall for web apps operates as a proxy server, but thanks to its ability to analyze HTTPS traffic (that is achieved through importing the target server security certificate), it can also be applied for other functions, such as SSL traffic termination and server load balancing (SLB). WAF also supports clustering and performs the acceleration of web apps.
WAF supports two main deployment modes:
- Gateway (bridge mode, transparent proxy, reverse proxy);
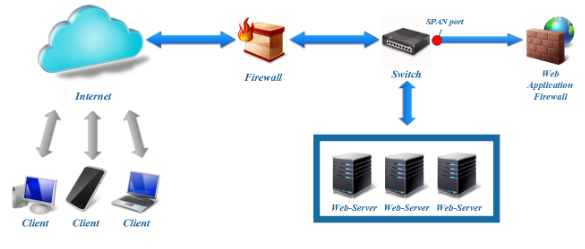
- Monitor (network monitoring mode via SPAN port).
Figure. 1. Typical WAF deployment in Gateway mode
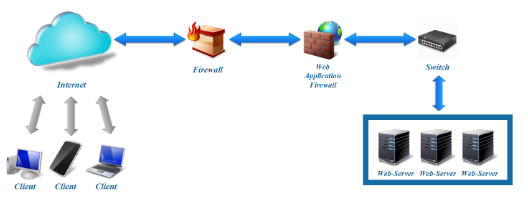
Figure 2. Typical WAF deployment in Monitor mode
The firewall for web apps (WAF) operates on the basis of two common security models:
Negative model or black list (denies what is predetermined). For providing a basic protection similar to IPS, but with a higher level of application security assessment, WAF can use both well-known signatures for most typical attacks preventing and specific signatures for kinds of attacks that seize vulnerabilities of certain web apps. For example: deny a certain potentially dangerous HTTP GET request and allow everything else;
- Positive model or whitelist (allows only what is predetermined). For improved security, another type of logic is used in addition to signatures: rules that define what is explicitly allowed. For example: allow only HTTP GET requests for a specific URL and deny all the rest.
Key features of WAF: - Support of all PCI DSS Requirements* applicable to web apps that in connection with the components of the systems in the payment card data processing environment;
- Prompt response (determined by an active policy and / or by set of rules) to threats and attacks identified in at least OWASP Top 10**;
- Scanning of incoming HTTP / HTTPS traffic plus requests to web apps and taking protection measures based on active policies and rules (allow, block, warn);
- Support and compliance with the correct functioning of the security models (positive and negative);
- Exploration and validation of web content created with Cascading Style Sheets (CSS), Dynamic HTML (DHTML), Hypertext Markup Language (HTML) and major web content delivery protocols such as Hypertext Transport Protocol (HTTP) and Transport Protocol Hypertext over SSL (HTTPS);
- Data leakage prevention – scanning of outgoing HTTP / HTTPS traffic and requests to web apps and taking protective measures based on active policies and rules, as well as timely events recording in the event log;
- Analysis of web services messages, especially public ones. As a rule this includes an overview of Simple Object Access Protocol (SOAP) and extensible Markup Language (XML), also Remote
- Procedure Call (RPC) oriented models of interaction with web services based on HTTP;
- Verification of any protocol or data constructs (proprietary or standardized) that is used to transfer data to/from web application.Protection from threats aimed directly at WAF;
- SSL and/or TLS termination (traffic decrypting and verifying before sending it to a web application).
Figure 3. The main types of attacks on the web application server
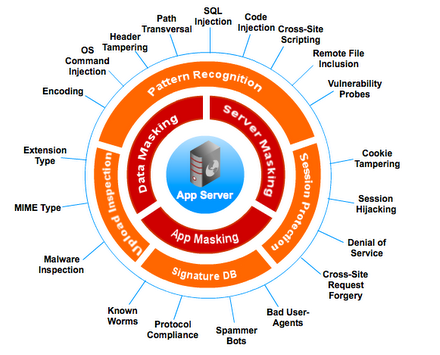
Disadvantages of IPS in the context of web resources protection
IPS devices are created to find and block attacks that common firewalls cannot handle. These systems analyze the package contents and compare it with the signatures of known attacks. Additionally, IPS systems can evaluate and block application layer Protocol anomalies.
The total number of web application vulnerabilities and their variations is several orders of magnitude higher than the total number of signatures in modern IPS systems databases. Therefore, IPS systems that operate on the principle of comparing packages with known signatures are not an effective solution against web attacks.
Reliable protection of web applications requires a deep understanding of their structure, including URL parameters, cookies, data entry forms, etc. Unfortunately, modern IPS systems are not able to fully analyze web applications structure and, hence, ensure their reliable protection.
Disadvantages of NGFW in the context of web resource protection
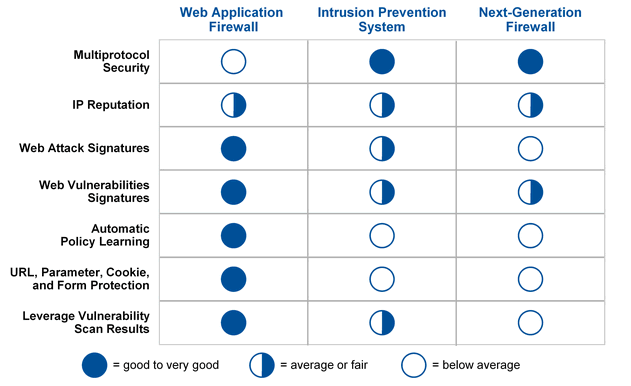
The fundamental difference between WAF and NGFW is the orientation of mentioned devices: NGFW first of all is is targeted at controlling apps which are external to the company (such as, peer-to-peer or Facebook), while WAF provides protection for user-oriented web apps hosted on internal company’s servers.
NGFW doesn’t control the HTTP/HTTPS sessions at all or they are partially under control. It blocks only known types of attacks and mainly uses a “blacklist” approach to providing web protection, and does not compensate for the vulnerabilities of poorly designed web apps.
NGFW is sufficient to protect most web applications. But for apps which require enhanced protection and continuous monitoring, WAF provides a more robust set of controls that can block both known types of attacks and ones against which protective mechanisms have not yet been developed (Zero-Day Attacks).
NGFW are not equipped with WAF, because a great amount of computing power is required for correct operation of the latter. Moreover, there is a limited set of companies that need WAF (mainly in the financial sphere). Therefore, at the moment, WAF remains an autonomous and independent technology with unique and narrowly focused functionality and high development potential in near future.
Figure 4. Comparing WAF, IPS and NGFW in the context of web-resources security
PCI DSS Main Requirements:
- Ensure firewalls functioning for cardholders data protection;
- Don’t use set as the default passwords or other system parameters;
- Provide secure cardholders data storing;
- Encrypt cardholders data during its transmitting through public networks;
- Protect all systems from malicious software and perform an antivirus software updating systematically;
- Develop and support secure systems and apps;
- Limit the possibility of access to cardholders data by business justification;
- Identify and confirm the access to the system elements;
- Limit the physical access to cardholders data;
- Perform controlling and tracking of all the access to network resources and to cardholders data;
- Perform systematically systems and security processes testing;
- Constantly Develop and maintain a policy that addresses information security for all staff.
OWASP Top 10:
- A1: vulnerabilities to code implementation (all kinds of injections, including SQL, LDAP, etc)
- A2: XSS vulnerabilities (Cross Site Scripting)
- A3: vulnerabilities arising from incorrect authentication mechanism implementation and web application sessions management;
- A4: vulnerabilities that allow to perform uncontrolled accessing to internal web application objects directly. Directory traversal ability (Path Traversal);
- A5: vulnerabilities CSRF (Cross Site Request Forgery);
- A6: vulnerabilities arising from misconfiguration of the web app and its environment;
- A7: vulnerabilities associated with incorrect implementation of cryptographic techniques of information security for critical data storing on the server side;
- A8: vulnerabilities of web application authorization mechanism (possibility of direct accessing to resources by URL);
- A9: insufficient security of the transport Protocol;
- A10: vulnerabilities which allow to use a web app to redirect users to any site (Open Redirects).