In Penetration testing we conduct a series of activities, which help you to identify and exploit security vulnerabilities by simulating an attack on a computer or network from external and internal threats to give you a clear picture of the effectiveness or ineffectiveness of the security measures that have been implemented.
The process involves an active analysis of the system for any potential vulnerabilities that could result from poor or improper system configuration, both known and unknown hardware or software flaws, or operational weaknesses in process or technical countermeasures. This analysis is carried out from the position of a potential attacker and can involve active exploitation of security vulnerabilities.
Why Penetration testing?
- Avoid chances for reputation loss
- Achieve Compliance
- Performing this assessment on a regular basis will also help to address specific regulatory requirements, such as FFIEC/GLBA, HIPAA/HITECH, NERC, and PCI DSS requirement
- Identifying higher-risk vulnerabilities that result from a combination of lower-risk vulnerabilities exploited in a particular sequence
- Testing the ability of network defenders to successfully detect and respond to the attacks
- Identifies weaknesses in security concepts, systems and applications
- Analysis of the security measures against “Inside out“ attacks
- Provide management with an understanding of the level of risk from Internet-accessible services.
- Provide recommendations and details to facilitate a cost-effective and targeted mitigation approach.
- Create a basis for future decisions regarding information security strategy, requirements and resource allocation.
- To execute a real-world attack on critical infrastructure and understand the level of risk that exists at a single moment in time.
Methodology: Penetration Testing
Phase 1: Initialization
Know your requirements:
We overcome this by sitting down with your team and let you teach us about your company and systems. As you are most familiar with the case in this matter, we rely on your experience to walk us through what you have in an interactive manner.
This process alone can save months of effort and cost.
Agreement is signed before testing begins:
This agreement spells of restrictions, limitations, and obligations between the organization and the team of penetration testing. This agreement aims to increase the effectiveness of the test itself while minimizing operational impact.
Phase 2: Real Testing
- Reconnaissance and Enumeration: Checking the Internet for the customer’s public-facing presence and information.
- Network Surveying and Services Identification: Drawing a picture of what the customer’s perimeter looks like to the outside world
- Automatic and Manual Testing
- Exploitation
- Privilege Escalation
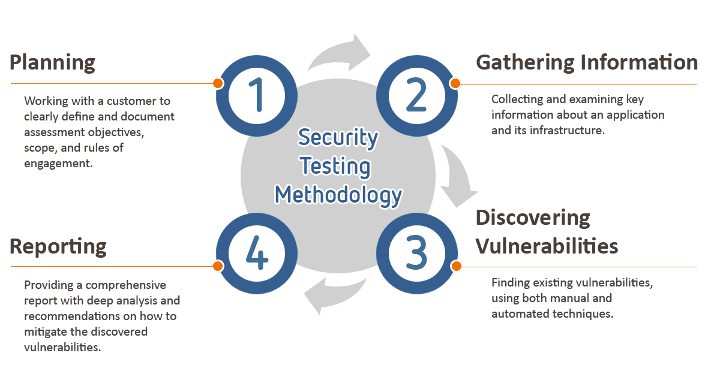
Phase 3: Reporting
- The work will be done and we will be sure to keep you informed every step of the way.
- The report will be created to inform you on what has been discovered and what we propose to correct any problems.
- We will work with you to make sure that you understand the results and get the knowledge necessary to take any action that may need to take.