A bit of CI / CD magic: setting up the delivery of database migration scripts using GitLab and Liquibase
The CI / CD development methodology is already applied to most projects. It is…
Why do you need continuous delivery and continuous deployment?
There are a lot of materials on how to establish continuous delivery, but there…
How to speed up a website by 4 times by simply reconfiguring the server
If you are working with a site that is gradually growing - the number of…
Cloud kitchen - preparing data for monitoring using the vCloud API
One of the tasks of administering a cloud infrastructure is monitoring its…
A million distributed databases in the cloud
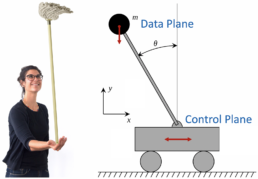
Remember children's fun? Place the mop in the palm of your hand and keep it…
Data Center Automation
Most HPE servers have an Integrated Lights Out (iLO) management controller. Its…
The World's Best CDNs to Work: A Comparative Review
Content delivery networks (CDNs) are widespread these days. This is quite…
Kubernetes 1.21 - unexpectedly many changes
CronJob The blog post says that CronJob are declared stable, but then there is…