AWS is the largest cloud service provider. Common cloud services include storage, computing power, databases, analytics, security, monitoring, developer tools, networks.
Cloud is where you store your data / applications / processes and access them anytime over the internet.
The Five Pillar
AWS engineers have written the basic practices documentation for proper and painless hosting in the cloud,. These practices include:
- Operational Excellence
- Security
- Reliability
- Performance Efficiency
- Cost optimization
Let’s analyze these practices and the Shared responsibility model in this article.
Operation excellence
Human error is a major cause of malfunctions and operational incidents. The more operations you can automate, the less chance of human error.
This practice is aimed at automating processes in order to reduce the factor of human error.
Two concepts:
- Infrastructure as a Code (ex. CloudFormation. CDK)
- Observability (Analytics, Metrics, Actions)
Infrastructure as a Code allows you to write code to deploy AWS services via yaml / json (CloudFormation) files or in your favorite language (Cloud Development Kit). You write once – you use it many times, isn’t it a DevOps heaven?
Observability allows you to view your infrastructure, collect various metrics, and if any bad or expectedly good situation occurs, then in AWS you can configure an action for this.
Example of a bad situation: You have deployed a large food delivery service. Tested, everything works perfectly, the application is gaining popularity, your cloud engineer horizontally scales your service up to 100 instances, and at some point half of the instances go offline (suppose someone lit a cigarette incorrectly during a night smoke break in an AWS data center) … And half of the users start to complain about the inaccessibility of food delivery. What to do at night without food?
What did we do before we learned about operation excellence: we call a cloud engineer, he flies to the office to his PC, in a tremor begins to deploy instances in another AWS data center. And hurray, by morning all services have been restored. But customers are already lost, they have found another delivery. You lose!
What do we do after we have learned about operation excellence: we set up the metric for the minimum number of instances of 100, and the next time someone tries to light a cigarette, we will be ready and AWS will return all missing instances for us as soon as a problem occurs. You win!
Security
Focuses on how to secure your infrastructure in the cloud. Three important concepts related to security in the cloud:
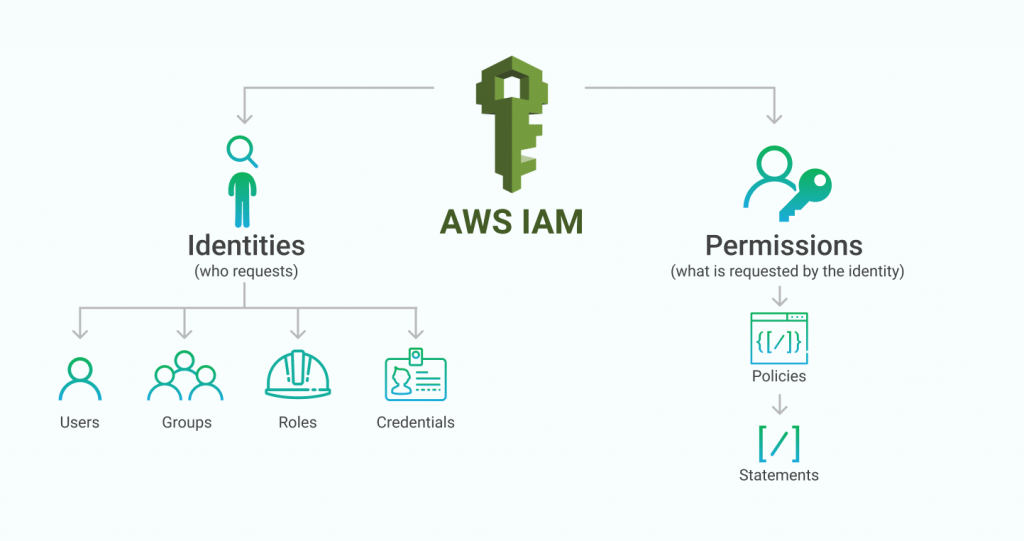
- Identity and Access Management (IAM)
- Network security
- Data Encryption
IAM is a key AWS service that allows you to create users, roles, groups, policies.
Network security – you can configure which traffic can travel across your network in the cloud and which cannot. All possible types of filtering: from checking headers in https requests to ports for tcp connections.
Reliability
Focuses on how you can build fault-tolerant services. The cloud gives you the means to build fault-tolerant services that can withstand disruption so you design your services for reliability.
Two concepts for building resilient systems:
- Fault Isolation (Resource, Availability Zone, Region)
- Limits (soft and hard)
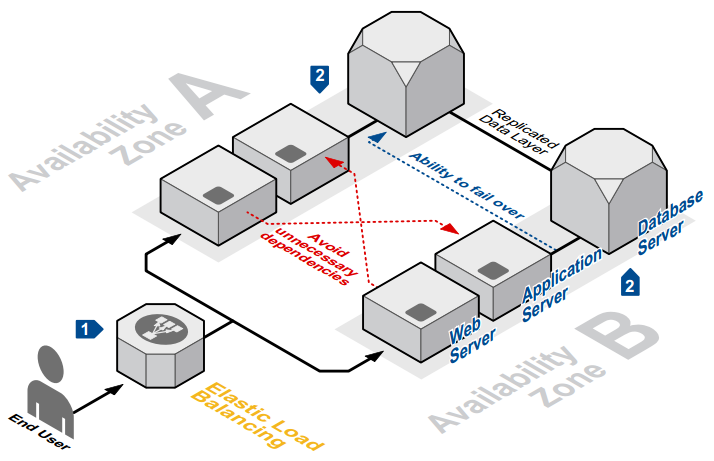
Fault Isolation says that it is worth isolating your services from failures, the fewer parts of your system fail, the better, it would seem that everything is simple.
What should be done to achieve this? Hosting resources in different AWS datacenters, in different regions and availability zones will help you to make your services highly available.
The second concept is setting limits. The most accessible example is protection against DDoS attacks. You test the operational bandwidth of your application, set the limit on receiving to a maximum of 150% of the current bandwidth, and you will not be able to “bother” you.
Performance Efficiency
Focuses on how you can run services in the cloud efficiently and in a scalable manner. While the cloudgives you the ability to handle any amount of traffic, it requires you to choose and configure your services to scale.
Two main concepts:
- Selection
- Scaling
The first concept is the choice of services for your needs. Choose those services that are suitable for your specific task. If it is batch processing of big data – there is AWS EMR, if it is streaming – Kinesis, if data migration to the cloud – AWS DataSync. All of them are optimized for their specific task.
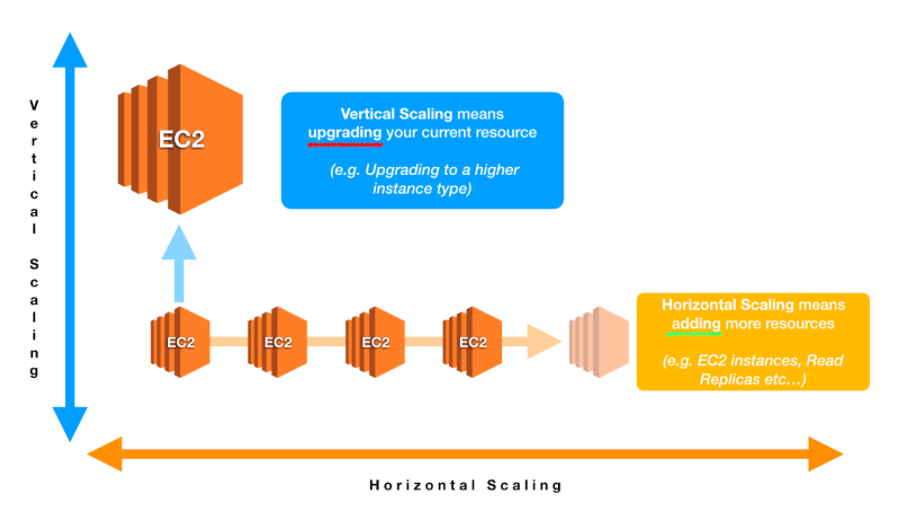
Scaling allows you to increase the performance of your application by increasing the capacity of an instance (vertical scaling) or increasing their number (horizontal scaling).
Cost optimization
Focuses on optimizing costs helps you achieve business results while minimizing costs. The Pay-as-you-go model makes the following changes to your cost optimization process:
- Pay for use
- Cost Optimization Lifecycle
Shared responsibility model
This model shows who is responsible for what in AWS.
From AWS Documentation: “AWS is responsible for securing the AWS Cloud infrastructure that runs all of the services offered. This infrastructure consists of the hardware, software, networks, and objects that power AWS cloud services.
Customer responsibilities will be determined by the AWS cloud services selected for use. The choice of services determines the amount of customization that the customer must perform as part of their security responsibilities. Customers who deploy an Amazon EC2 instance are responsible for managing the guest operating system (including updates and security patches), any application software or service components installed on the instances, and configuring the firewall (security group) provided by AWS for each instance. For abstract services such as Amazon S3 and Amazon DynamoDB, AWS manages the infrastructure layer, operating system, and platform, and clients access endpoints to store and retrieve data. Clients are responsible for managing their data (including encryption settings), classifying their resources, and using IAM tools to enforce appropriate permissions. ”
What does this mean? If a nuclear bomb falls on the AWS datacenter, they take responsibility for this incident. And they will make excuses / compensate for the damage. If you do not encrypt data when transferring from your computer and the data is intercepted and stolen, this is your problem.
Afterword
You have read AWS Cloud Core Concepts. In this article, you learned the following:
- The Five Pillars of AWS Architecture
- Important models that represent cloud-based thinking
- Key concepts within each of the five pillars
- Shared responsibility model.