Nemesida WAF Free is a free version of Nemesida WAF that provides basic protection for a web application from OWASP attacks based on signature analysis. Nemesida WAF Free has its own signature database, detects attacks on web applications with the minimum number of false positives, updates from the Linux repository, installs and configures in a few minutes, doesn’t require compilation and can be connected to the already installed NGINX version 1.12.2 or higher.
Some time ago, was announced support for Nemesida WAF Free for the NGINX Mainline and Plus versions (previously only the Stable branch was supported). Having decided not to stop there, was added the functionality of sending detected attacks to your personal account in the Free version.
What allows the new (for the Free version) function:
- visualize attacks, search by parameters, generate a report in PDF format
- send attacks per email
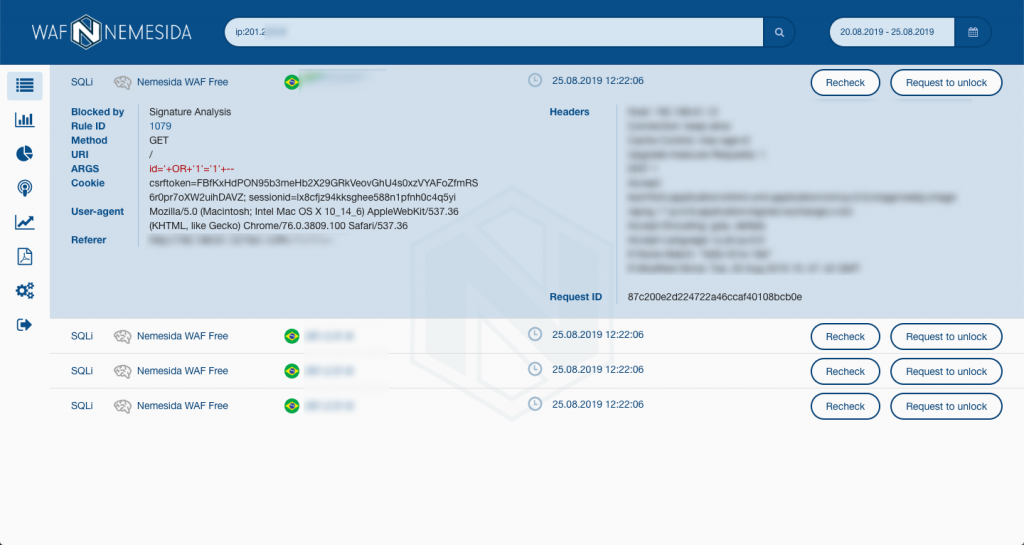
- receive information about the contents of a blocked request
- receive information about the source of the attack by its IP address (via ip.pentestit.ru)
- integrate Nemesida WAF Free with SIEM and third-party systems for analyzing and visualizing events (attacks are sent to the API, after which they get into the database for further processing, PostgreSQL is used)
Features of Nemesida WAF Free
- minimum hardware requirements
- minimal increase in response time during request processing
- install and update from repository
- the ability to connect to an already installed NGINX
- installation and setup in a few minutes
- ease of maintenance
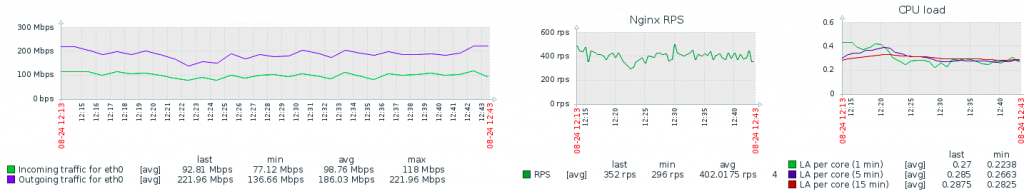
High loads
Even with high traffic intensity (~ 500 RPS), Nemesida WAF Free practically doesn’t load the processor and doesn’t consume memory:
Traffic statistics
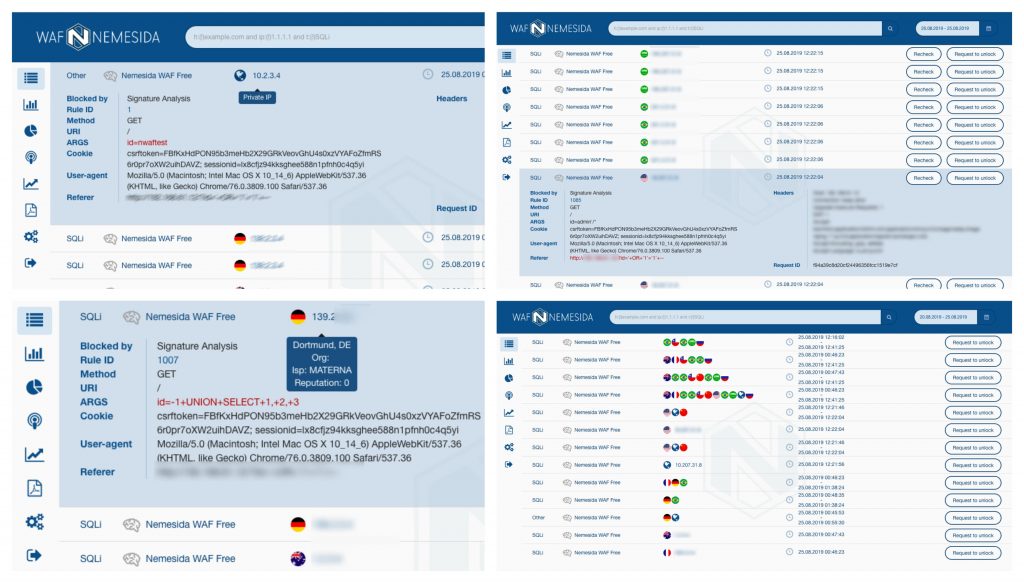
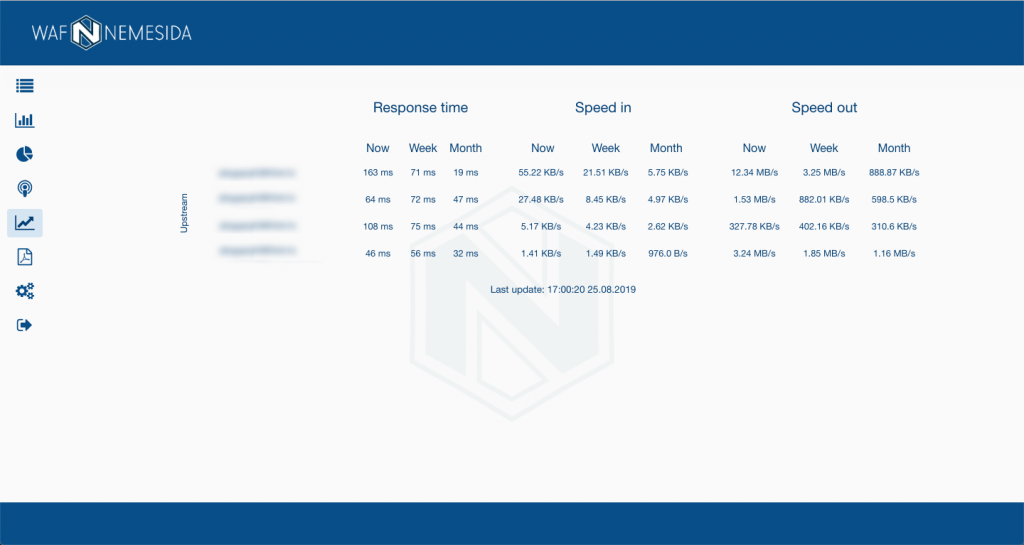
Nemesida WAF personal account allows you to display statistics of traffic and response time from the final web application. To do this, connect the VTS dynamic module to NGINX. After setting the necessary parameters, statistics will be available in your personal account:
Event Search
The search string in the Personal Account can take various values, for example, search by the occurrence of an attack, IP source, type of attack, etc.:
Types of Blocked Attacks
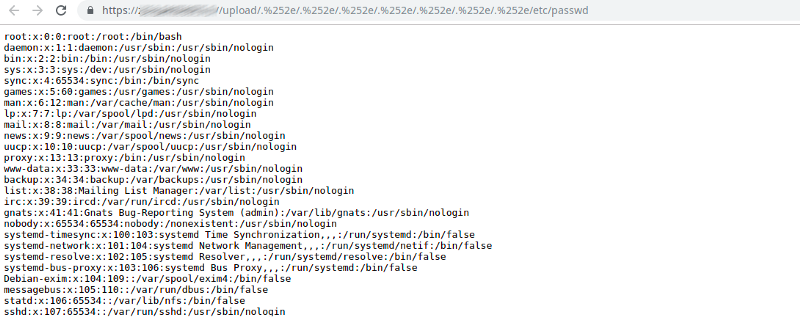
- Injection (RCE, SQLi, XXE, OS command, etc.)
- Xss
- Information leakage
- Path traversal
- Open redirect
- Web shell
- HTTP Response Splitting
- RFI / LFI
- Server-Side Request Forgery
Signature Information
The latest signature set is available at rlinfo.nemesida-security.com. In addition, each request blocked by the signature method has a rule identifier (RuleID), by clicking on which, you can always create an exception rule:
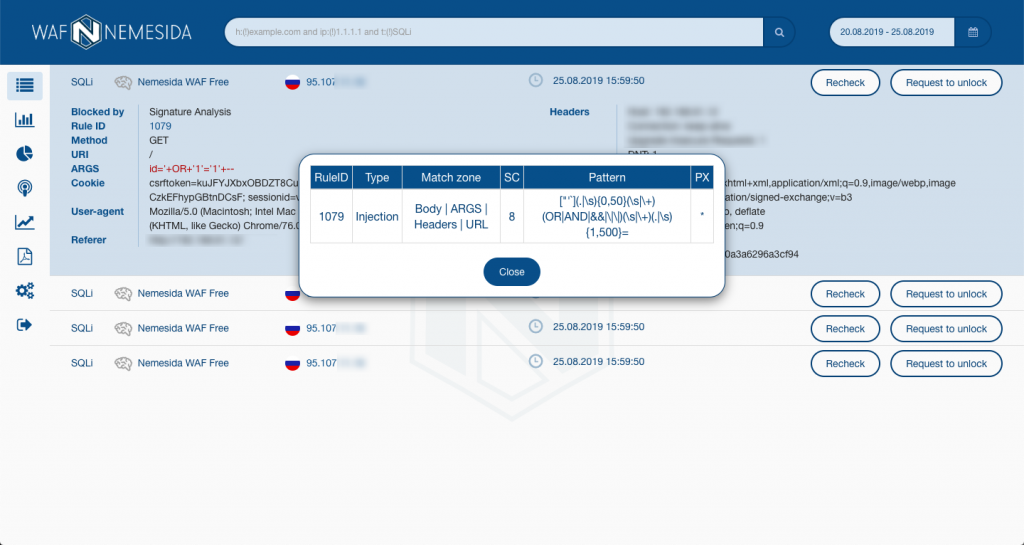
Except this
In Nemesida WAF Free, you can create your own signatures (RL), exclusion rules (WL), disable or put WAF in LM mode (similar to IDS) for a specific or all virtual hosts, and also use these features for IP addresses of request sources.
Installation and setup
- Nwaf-dyn-1.x dynamic module for NGINX (~ 5 min.)
- Nemesida WAF API (~ 10 min.)
- Personal account (~ 15 min.)
- Virtual Appliance (VMDK for KVM / VMware / Virtualbox with Nemesida WAF components already installed under Debian 10, 1.3 GB)
Despite the absence of the machine learning module and auxiliary components in the Free version (vulnerability scanner, virtual patch, etc.), Nemesida WAF Free is an “easy” but effective tool to counter inappropriate attacks on a web application. All Nemesida WAF Free components are available for Debian, Ubuntu, and CentOS distributions.