When conducting penetration testing, it is necessary to aggregate data from several sources and to compare the results of periodic tests. For this purpose, specialized frameworks are used, which will be discussed in this article.
During the testing for penetration of a large project or by a team of participants, the question arises of team interaction and systematization of the results – these are reports of various analysis tools and vulnerabilities identified in manual mode – all this represents a huge amount of information in which there is no proper order and system approach, you can miss something important or have the possible doubles. There is also a need to reduce reports and normalize them and bring to a single view. To solve these problems, there are several popular products.
Trello
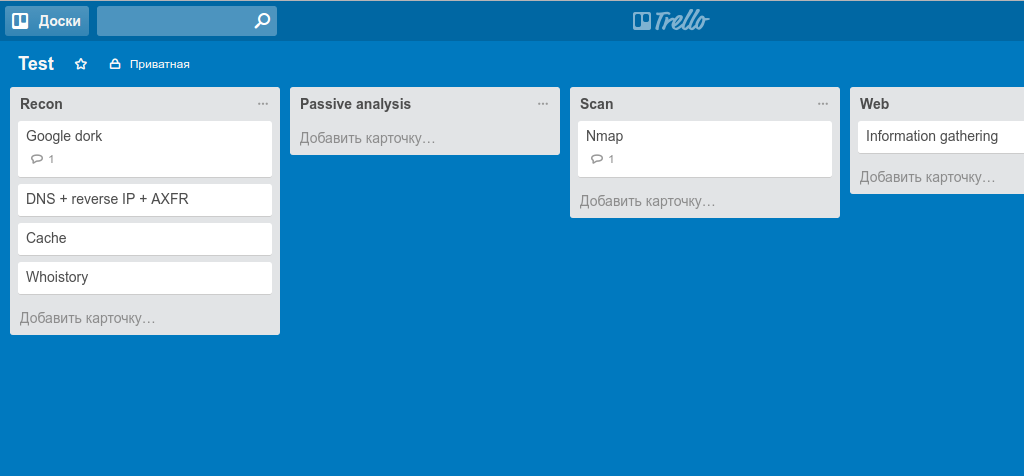
One of the most popular solutions from the development world has come to the world of information security. Trello helps you see all the details of the project at a glance. The main advantage of Trello is the ability to see several simultaneously launched projects and their status at the current time. If you lead a group of developers or other executors working on projects with a deadline or a fixed goal, this system can give you an idea of the progress of projects at any given time. This is well applicable when conducting an audit by several employees. This system is often used by CTF players to coordinate actions.
Official website: trello.com
MagicTree
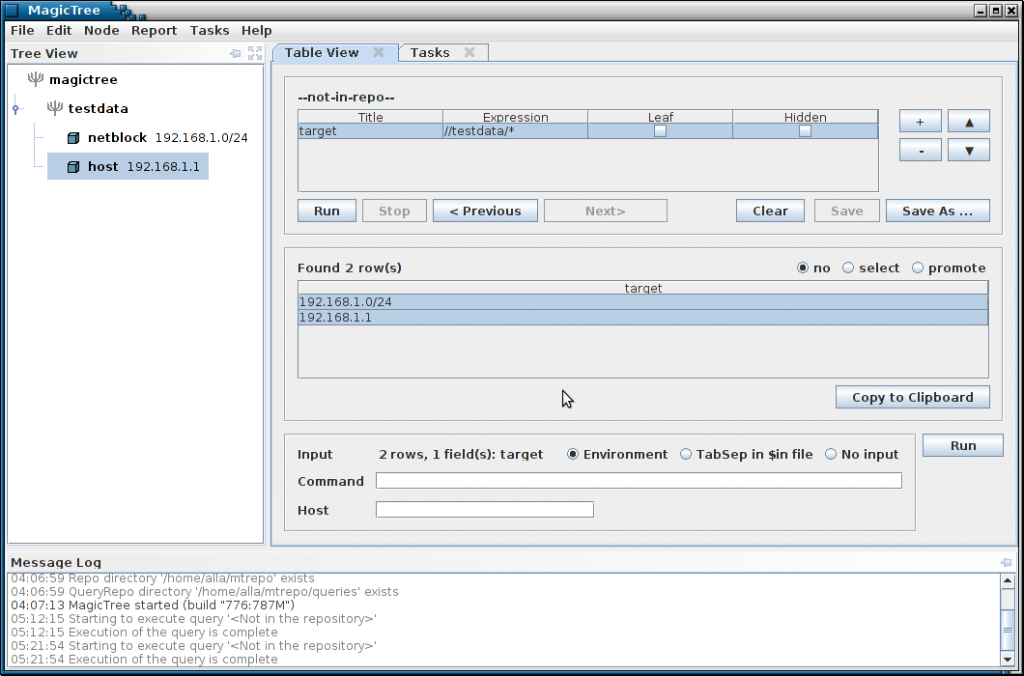
MagicTree stores data in a tree structure. A fairly convenient view for presenting information that is collected during network testing: host, ports, services, applications, vulnerabilities, etc.
The storage scheme is quite flexible for adding new information without violating the existing structure data: for example, you need to add the host MAC address – for this, a child node is added to the host node.
MagicTree allows you to retrieve data in the form of a table or list. The query interface uses XPath expressions to retrieve data. Also, this program allows you to use variables to interact with external components, such as nmap or nessus, and enter data directly into the host tree.
Official Website: www.gremwell.com/what_is_magictree
Dradis
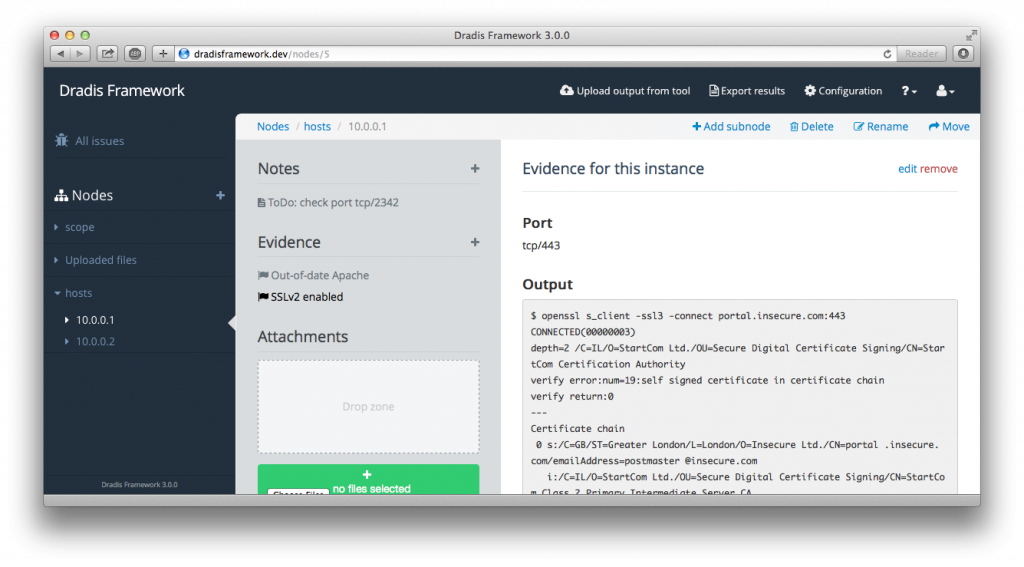
One of the oldest and most popular frameworks. Natively installed on Kali Linux. The Dradis Framework is an open source platform to simplify collaboration and reporting in the field of information security.
Dradis is a standalone web application that provides centralized storage of information. There are two versions – Community Edition (free) and Professional Edition (from $ 59). The pro version has more functionality, including integration capabilities, a reporting system, support (including priority), available methodologies, etc. It is possible to expand the functionality in the form of plugins / add-ons.
Supports work with the following utilities:
- Acunetix
- Brakeman
- Burp suite
- Metasploit
- Nessus
- Nexpose
- Nikto
- Nmap
- NTOspider
- Openvas
- OSVDB
- Qualys
- Retina
- Surureheck
- Vulndb
- w3af
- MediaWiki
- wxf
- Zed Attack Proxy
There are versions for Linux / Mac that can be installed from the git repository. There is also a virtual upgrade for Cloud9, the cloud provider.
The project has a good community, which allows you to improve and expand the capabilities of the framework.
Official website: dradisframework.org
Faraday
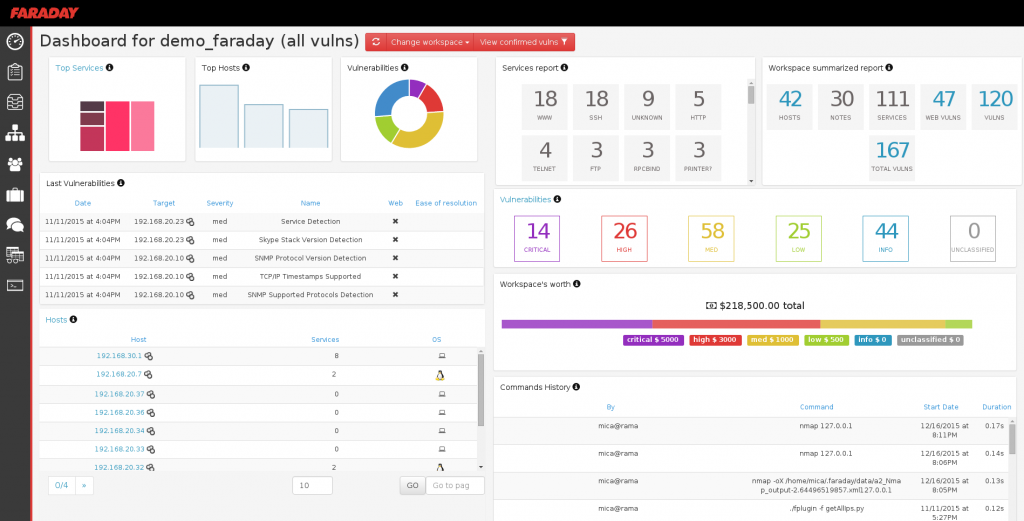
Faraday is the most powerful collaboration environment, true multiplayer penetration testing. Supports work in ArchAssault, Archlinux, Debian, Kali, OSX, Debian. It works in real time, instantly processing the results sent by one or another pentester. In this framework, is the concept of gamification, specialists are given the opportunity to measure skills in the number and quality of fixed vulnerabilities.
In this framework, there is a system of risk assessment in financial terms (which for me personally is quite subjective – author’s comment), but can provide the necessary information for business owners or top management of the company.
There are also additional Workspace for BugBounty program participants of the following vendors:
- Airbnb
- Github
- Imgur
- Mozilla
- ownCloud
- Vimeo
- Western Union
- Yahoo
The framework is distinguished by a rather thought-out interface that allows you to intuitively understand the functionality.
The framework is available in 3 editions: Community, Professional and Corporate.
Faraday exists as a client service and server (in Professional and Corporate versions).
This framework can interact with the following utilities (both in the form of import, and in the form of API or plugins):
- Acunetix (REPORT) (XML)
- Amap (CONSOLE)
- Arachni (REPORT, CONSOLE) (XML)
- arp-scan (CONSOLE)
- BeEF (API)
- Burp, BurpPro (REPORT, API) (XML)
- Core Impact, Core Impact (REPORT) (XML)
- Dig (CONSOLE)
- Dnsenum (CONSOLE)
- Dnsmap (CONSOLE)
- Dnsrecon (CONSOLE)
- Dnswalk (CONSOLE)
- evilgrade (API)
- Fierce (CONSOLE)
- ftp (CONSOLE)
- Goohost (CONSOLE)
- Hydra (CONSOLE) (XML)
- Immunity Canvas (API)
- Listurls (CONSOLE)
- Maltego (REPORT)
- masscan (REPORT, CONSOLE) (XML)
- Medusa (CONSOLE)
- Metagoofil (CONSOLE)
- Metasploit, (REPORT, API) (XML) XML report
- Nessus, (REPORT) (XML .nessus)
- Netsparker (REPORT) (XML)
- Nexpose, Nexpose Enterprise, (REPORT) (simple XML, XML Export plugin (2.0))
- Nikto (REPORT, CONSOLE) (XML)
- Nmap (REPORT, CONSOLE) (XML)
- Openvas (REPORT) (XML)
- PasteAnalyzer (CONSOLE)
- Peeping Tom (CONSOLE)
- ping (CONSOLE)
- propecia (CONSOLE)
- Qualysguard (REPORT) (XML)
- Retina (REPORT) (XML)
- Reverseraider (CONSOLE)
- Shodan (API)
- Skipfish (CONSOLE)
- Sqlmap (CONSOLE)
- SSHdefaultscan (CONSOLE)
- Telnet (CONSOLE)
- Theharvester (CONSOLE)
- Traceroute (CONSOLE)
- W3af (REPORT) (XML)
- Wapiti (CONSOLE)
- Webfuzzer (CONSOLE)
- whois (CONSOLE)
- X1, Onapsis (REPORT) (XML)
- Zap (REPORT) (XML)
Sometimes it is necessary to write your own plugin – there is documentation for their creation and integration into the system. It is also possible to debug the plugin using the live debug mechanism.
Official website: www.faradaysec.com
Conclusion
Some frameworks are rather specific and narrowly targeted; some, like Faraday, have redundant functionality and powerful expansion capabilities, but they are all designed to fulfill one role – to process results in a high-quality and structured way
Conducting a full-scale audit of information security with the involvement of highly qualified specialists will help you avoid incidents that can undermine the reputation of your organization and cause you significant losses.