More recently, at the beginning of summer, there were massive calls for updating Exim to 4.92 version due to the vulnerability CVE-2019-10149. And the other day it turned out that the malware Sustes decided to use this vulnerability.
Now all, who urgently updated the soft, can again be “happy”: on July 21, 2019, Zerons researcher discovered a critical vulnerability in the Exim Mail Transfer agent (MTA) by using TLS for versions from 4.80 to 4.92.1 inclusive, allowing remote code execution with privileged rights (CVE -2019-15846).
Vulnerability
The vulnerability is present when using both the GnuTLS and OpenSSL libraries for establishing a secure TLS connection.
According to developer Heiko Schlittermann, the configuration file in Exim doesn’t use TLS by default, however, many distributions create the necessary certificates during installation and include a secure connection. Newer versions of Exim also set the tls_advertise_hosts = * option and generate the necessary certificates.
depends on the configuration. Most distros enable it by default, but Exim needs a certificate+key to work as a TLS server. Probably Distros create a Cert during setup. Newer Exims have the tls_advertise_hosts option defaulting to “*” and create a self signed certificate, if none is provided.
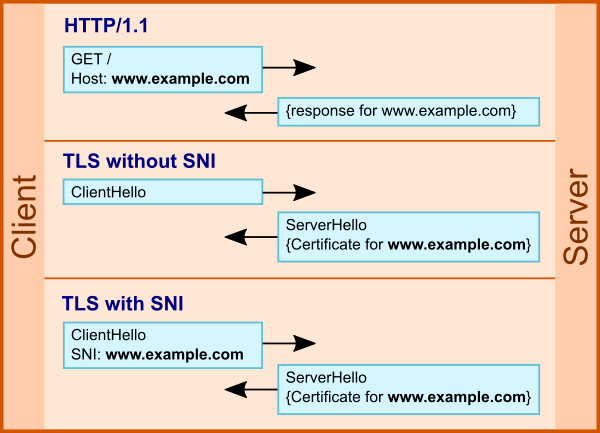
The vulnerability itself consists in incorrect SNI processing (Server Name Indication, a technology introduced in 2003 in RFC 3546 for a client to request the correct certificate for a domain name, Distribution of the TLS SNI standard / WEBO Group’s blog) during a TLS handshake. It is enough for an attacker to send an SNI ending in a backslash (“\”) and a null character (“\ 0”).
“Quay’s” researchers found a bug in the string_printing (tls_in.sni) function, which is the incorrect \ “escaping. As a result, the backslash is written in unescaped form to the print spool header file. Further, this file with privileged rights is read by the spool_read_header () function, which leads to heap overflow.
Notice that, Exim developers have created PoC vulnerabilities with the execution of commands on a remote vulnerable server, but it is not yet publicly available. Due to the ease of operation of the bug, this is just a need of time, and quite a short one.
Number of potentially vulnerable public servers
According to the statistics from a large hosting provider E-Soft Inc on September 1, on leased servers with version 4.92 is used more than 70% of hosts.
|
Version |
Number of Servers | Percent |
| 4.92.1 | 6471 | 1.28% |
| 4.92 | 376436 | 74.22% |
| 4.91 | 58179 | 11.47% |
| 4.9 | 5732 | 1.13% |
| 4.89 | 10700 | 2.11% |
| 4.87 | 14177 | 2.80% |
|
4.84 |
9937 |
1.96% |
| Other versions | 25568 |
5.04% |
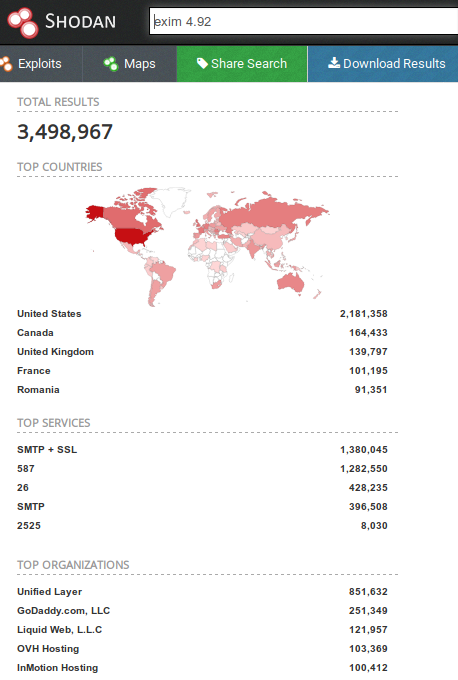
If you turn to the search engine Shodan, then from 5,250,000 in the server database:
According to the search engine Shodan, from 5,250,000 in the server database:
- about 3,500,000 use Exim 4.92 (about 1,380,000 with SSL / TLS);
- over 74,000 use 4.92.1 (about 25,000 with SSL / TLS).
Thus, there are about 1.5 million publicly known and accessible Exim potentially vulnerable servers.
Protection
- The simplest, but not recommended, option is to not use TLS, which will result in forwarding e-mail messages in clear text.
- In order to avoid exploitation of the vulnerability, it will be more preferable to upgrade to Exim Internet Mailer 4.92.2.
- If it is not possible to upgrade or install the patched version, you can set the ACL in the Exim configuration for the acl_smtp_mail option with the following rules:
# to be prepended to your mail acl (the ACL referenced
# by the acl_smtp_mail main config option)
deny condition = ${if eq{\\}{${substr{-1}{1}{$tls_in_sni}}}}
deny condition = ${if eq{\\}{${substr{-1}{1}{$tls_in_peerdn}}}}