The first attacks appeared almost simultaneously with the Internet. DDoS as a phenomenon has become widespread since the late 2000s (see www.cloudflare.com/learning/ddos/famous-ddos-attacks).
From about 2015-2016, almost all hosting providers made protection from DDoS attacks, like most prominent sites in competitive areas.
If 10-20 years ago most of the attacks could be repelled on the server itself, now everything is more complicated.
First, briefly about the types of attacks.
Types of DDoS attacks in terms of choosing a protection operator
L3 / L4 attacks (OSI model)
- UDP flood from the botnet (many requests are sent directly from infected devices to the attacked service, the channel is blocked by servers);
- DNS / NTP / etc amplification (many requests for vulnerable DNS / NTP / etc are sent from infected devices, the sender’s address is spoofed, a lot of packets responding to requests floods the channel of the attacker; this is how the most massive attacks on the modern Internet are performed);
- SYN / ACK flood (many connection requests are sent to the attacked servers, the connection queue overflows);
- attacks with packet fragmentation, ping of death, ping flood
These attacks aim to “fill up” the channel of the server or “kill” its ability to receive new traffic.
Although SYN / ACK flood and amplification are very different, many companies deal with them equally well. Problems arise with attacks from the following group.
Attacks on L7 (application level)
- http flood (if a website or some http api is being attacked);
- attack on vulnerable parts of the site (without a cache, very heavy load on the site, etc.).
The goal is to make the server “work hard”, process a lot of “as if real requests” and be left without resources for real requests.
Although there are other attacks, these are the most common.
Serious attacks at the L7 level are created in a unique way for each attacked project.
Why 2 groups?
Because there are many who know how to beat off attacks at the L3 / L4 level well, but either do not take up protection at all at the application level (L7), or dealing with it is weaker than the alternatives.
Who is who in the DDoS protection market
L3 / L4 protection
In order to beat off attacks with amplification (“blocking” the server channel), there are enough wide channels. Do not forget that very rare attacks with amplification last longer than an hour. If you are Spamhaus and everyone doesn’t like you – yes, you they can try to put down your channels for several days, even at the risk of further survival of the used global botnet. If you just have an online store, – 1 Tbit for several days, you will not see very soon (I hope).
In order to repel attacks with SYN / ACK flood, packet fragmentation, there is a need for equipment or software systems to detect and block such attacks.
Such equipment is manufactured by many operators have already installed it and sell DDoS protection services. Some companies are developing their software solutions right noe.
Of the well-known players, L3 / L4 DDoS is more or less effective in repelling everyone. I’m not going to say who has the maximum channel capacity (this is insider information), but usually it’s not so important, and the only difference is how quickly the protection works (instantly or after a few minutes of the project’s downtime).
The question is how qualitatively this is done: an attack with amplification can be repelled by blocking traffic from countries with the most harmful traffic, or you can discard only really unnecessary traffic.
But at the same time, based on my experience, all serious players in the market can cope with this without problems: Qrator, DDoS-Guard, Kaspersky, G-Core Labs (formerly SkyParkCDN), ServicePipe, Stormwall, Voxility, etc.
Some operators have a separate service “protection against attacks at the L3 / L4 level”, or “protection of channels”, it costs much cheaper than protection at all levels.
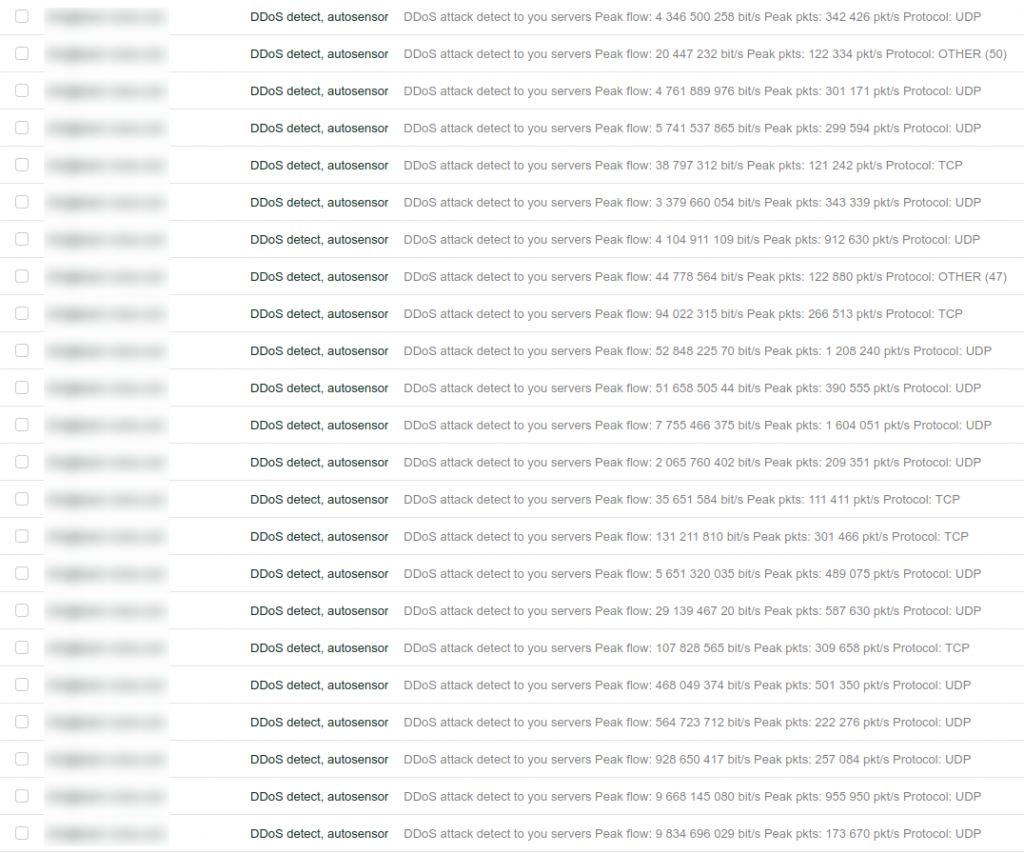
L7 protection (application level)
Attacks at the L7 level (application level) are able to beat units steadily and efficiently.
I have a real big enough experience with
- net;
- DDoS-Guard;
- G-Core Labs;
- Kaspersky
They charge a fee for every megabit of pure traffic, a megabit costs more than 15$. If you have at least 100 Mbps of pure traffic – oh. Protection will be very expensive. In the following articles, I can tell you how to build applications in order to save very well on the capacity of protection channels.
The real “king of the hill” is Qrator.net, the rest are somewhat behind them. Qrator is the only one in my practice what give a close to zero percentage of false positives, but at the same time it is several times more expensive than other market players.
Other operators have high-quality and stable protection. Many of the services we support are protected by DDoS-Guard, G-Core Labs, and we are quite happy with the result, I can recommend them.
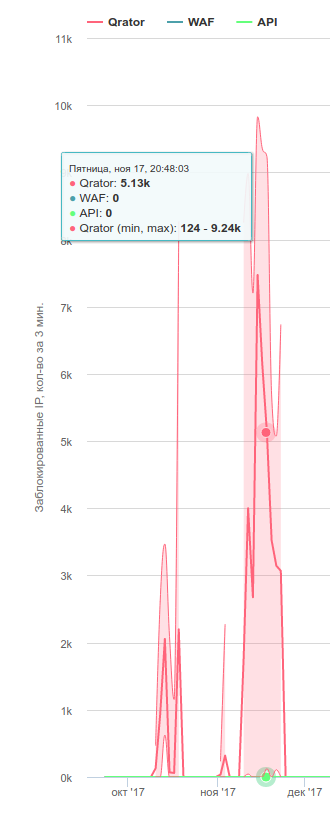
Attacks repelled by Qrator
There is still experience with small protection operators such as cloud-shield.ru, ddosa.net, etc. I definitely can’t recommend it, because experience is not very large, I will talk about the principles of their work. The cost of protection is often 1-2 times lower than that of large players. As a rule, they buy a partial defense service (L3 / L4) from one of the larger players + make their own defense against attacks at higher levels. It can be quite effective + you can get good service for less money, but these are still small companies with a small staff, please remember this.
Cloudflare
CloudFlare is a separate phenomenon. This is already a huge company that costs several billion dollars, their customers are half the traffic generators in the world, and the DDoS protection service is simply the most famous among their services. We also constantly use them for DNS hosting, CDN, as a traffic proxy service.
For a site / service that does not have complex attacks, Cloudflare is quite ok, but in case of serious attacks (when they do not just “fill up” the channel and combine many types of attacks), their Business plan for $ 200 never saved us, but it’s cheaper and more effective as other players.
Why is it like that? I think it’s difficult to make a massive almost free service with very high quality.
What is the difficulty of repelling attacks at the L7 level?
All applications are unique, and you need to allow traffic that is useful to them and block harmful traffic. It’s not always possible to put out bots unambiguously, so you have to use many, really MANY stages of traffic purification.
Once the nginx-testcookie module was enough, and now it is enough to repel a large number of attacks. When I worked in the hosting industry, my L7 protection was built just on nginx-testcookie.
Unfortunately, attacks have become more difficult. testcookie uses checks on bots based on JS, and many modern bots can successfully pass them.
Attacking botnets are also unique, and you need to consider the characteristics of each large botnet.
Amplification, direct flood from a botnet, filtering traffic from different countries (different filtering for different countries), SYN / ACK flood, packet fragmentation, ICMP, http flood, while at the application / http level you can come up with an unlimited number of different attacks.
In total, at the level of protection of channels, specialized equipment for cleaning traffic, special software, additional filtering settings for each client, there can be tens and hundreds of filtering levels.
To properly manage this and correctly tune the filtering settings for different users, you need a lot of experience and qualified personnel. Even a major operator who decides to provide protection services cannot make it easy: experience will have to be gained on “dead” sites and false positives on legitimate traffic.
For the protection operator, there is no “beat DDoS” button, there are a large number of tools, you need to be able to use them.
And one more bonus example.
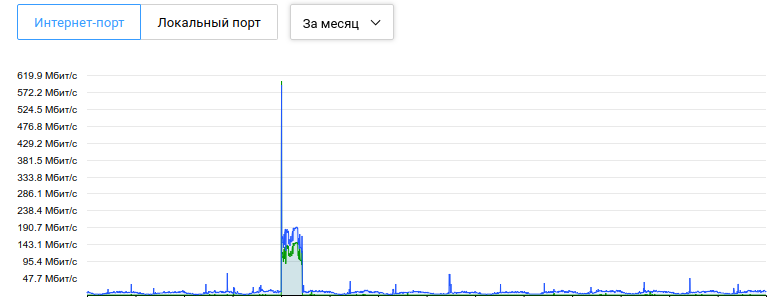
The server without protection was blocked by the hoster during an attack with a capacity of 600 Mbps
(The “loss” of traffic is not noticeable, since only 1 site was attacked, it was removed from the server for a while and the block was unlocked within an hour).
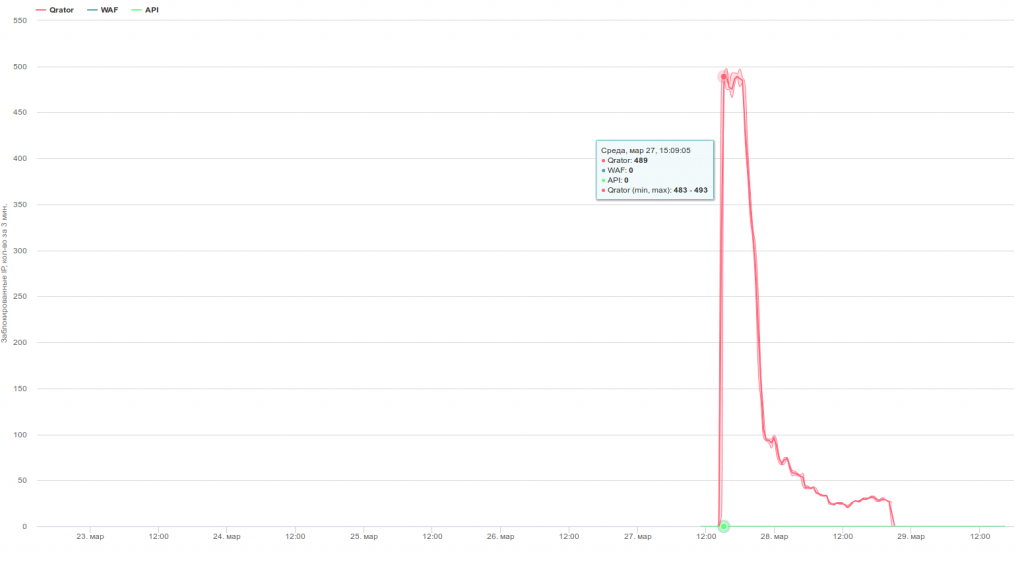
The same server is protected. The attackers “surrendered” after a day of repulsed attacks. The attack itself was not the strongest one.
L3 / L4 attacks and protection against them are more trivial, mainly they depend on channel thickness, algorithms for detecting and filtering attacks.
L7 attacks are more complex and original, they depend on the attacked application, the capabilities and imagination of the attackers. Protection from them requires great knowledge and experience, and the result may not be immediately and not one hundred percent. Until Google came up with another neural network for protection.